Insight about the All World Cards underground card shop
“All World Cards” is a new underground card shop created at the end of May 2021. The card shop went quite unnoticed until it caught the attention of the cybercriminal underground and the cybersecurity industry on August 2, 2021, by making publicly available one million compromised cards totally free of charge. All World Cards has currently listed for sale more than 2,7 million compromised cards.
“AW_Cards” (aka “AW_Support”), the representative of All World Cards in the cybercriminal underground, specified the cards were stolen in 2018-2019 with a 20% valid rate at the time of publication, though later they updated it to a 3% valid rate. In this article, Outpost24 analysts review the marketing efforts of the All World Cards team to become a reputable top player in the context of underground card shops, analyze the million compromised cards they published and how these were likely stolen, and the reactions of other threat actors in the cybercriminal underground.
Marketing campaign: 1 million credit cards published
On August 2, 2021, AW_cards posted on the underground forum XSS the following offer:
In the following days, the same advertisement was posted in at least other seven carding forums more, like Club2CRD, besides the top-tier Russian forum Exploit. The offering was warmly welcomed by members of the forums: the post received 6 positive reviews in Club2CRD, for instance, while in XSS the positive reactions were even more prominent. Out of the total 72 positive reactions held by AW_cards in XSS, 50 of them were related to the “1 million free cards” post. On Club2CRD, different members stated they have checked the available free cards and found several functioning ones.
The fact that some forum members have found functioning cards is an interesting aspect of this event, as the published cards were stolen in 2018 and 2019 – according to the forum post.
Additionally, this data was published in cybercriminal underground forums and, as it attracted the attention of such communities, most probably a multitude of cybercriminals have tried to use the cards before they become unfunctional. Therefore, the fact that functioning cards were identified amongst this large base represents a positive point to the reputation of the card shop and the threat actors behind it. Following the initial buzz around their launching marketing, the threat actor AW_cards continually updates their forum posts and the “News” section of the card shop with new card additions and prices.
Analysis of the published credit cards
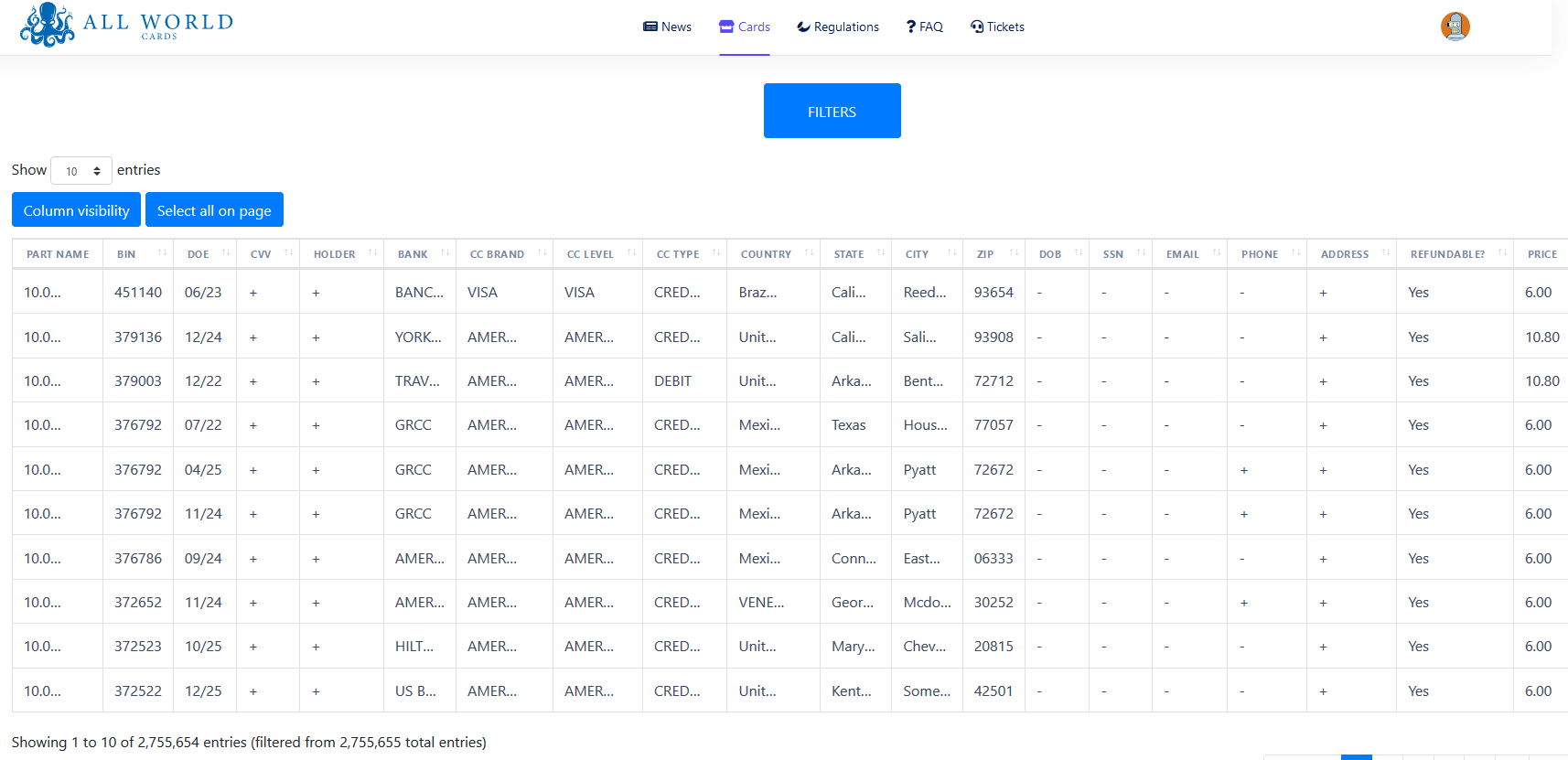
The 1 million credit cards released by the All World Cards administrator were shared in a ZIP file, “allworldcards_free_1000000.zip”, protected with the shop TOR domain as a password. The compressed file named “allworldcards_free_1000000” is a text file with 1 million lines and its modification date is August 2, 2021. Each line of this text file contains information about one credit card. The information per card might include:
- Credit card number (PAN)
- Expiration date
- CVV
- Cardholder name
- Country
- State
- City
- Address
- ZIP code
- E-mail password (in a few cases)
- Phone number
- Pin code (in a few cases)
- IP address (in a few cases)
While the credit card number, expiration date, and CVV are always present, the rest of the information is not always available and sometimes the format or the order changes, making the analysis more difficult.
Where were these cards stolen?
The fact that this data always includes the CVV number means that we are looking at card-not-present (CNP) data, instead of track data extracted from physical skimmers or POS malware.
The card-not-present data together with the kind of information sometimes available like phone number, e-mail, IP address or even e-mail password make us believe that the sources of these stolen credit cards were phishing, digital skimmers (Magecart schemes), and even social engineering. Some of the credit card information found in the dump contains insults by the victims to whoever was trying to steal the financial information, after realizing that it was a fraud. This is quite common to see in phishing attacks, where advanced users might notice the fraud attempt, but not in digital skimmers scenarios, where the malicious actions are invisible to the user and the attackers steal the financial information that users enter to pay in e-commerce sites.
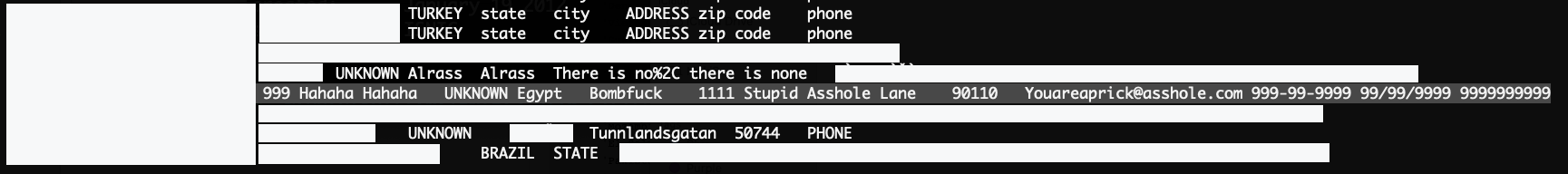
Looking at the data and the difference in format between the different records, we can probably assume that different threat actors were stealing these cards using the same or different methods and that it is not a unique provider, who would likely use the same data format and method.
When were these cards stolen?
The threat actor advertising All World Cards shop mentioned that those published cards were stolen in 2018 and 2019. According to our insights and correlating with our records, we can confirm that some of the cards were sold in 2019 and even before, but others might be more recent too.
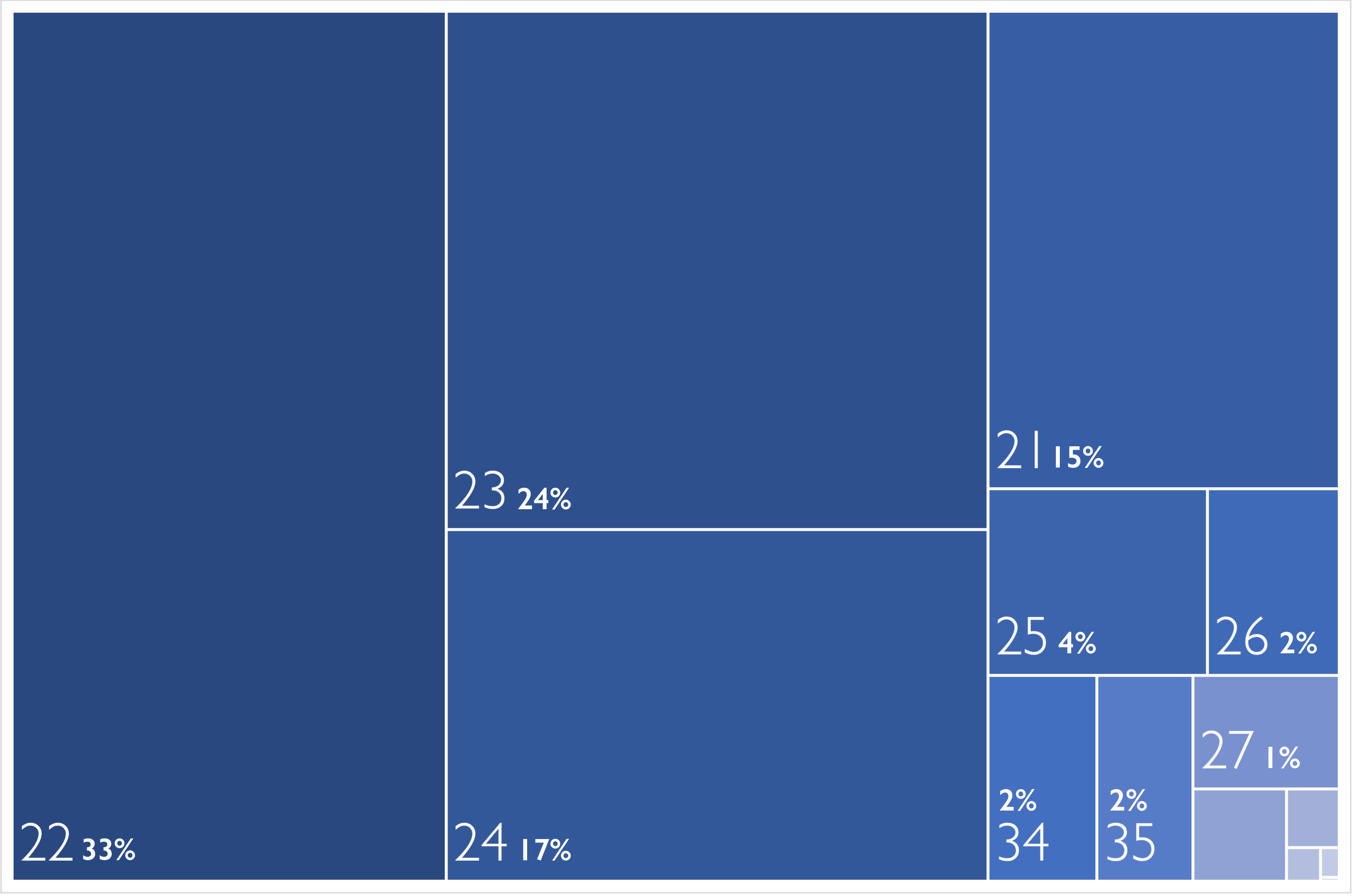
After analyzing the expiration dates of the published dump, we can see that most of the cards, around 90%, will expire between 2021 and 2024: 15% expiring in 2021, 33% in 2022, 24% in 2023, and 17% in 2024. A common expiration date is between 3 and 5 years after the card is issued (depending on banks).
Keeping this in mind and seeing that there are no cards expiring before 2021 in the dump, the time when the data was stolen mentioned by the threat actor might be real, because cards issued around 2018/2019 would expire between 2021 and 2024, which matches with the expiration dates present in the dump.
Geographical distribution of the victims
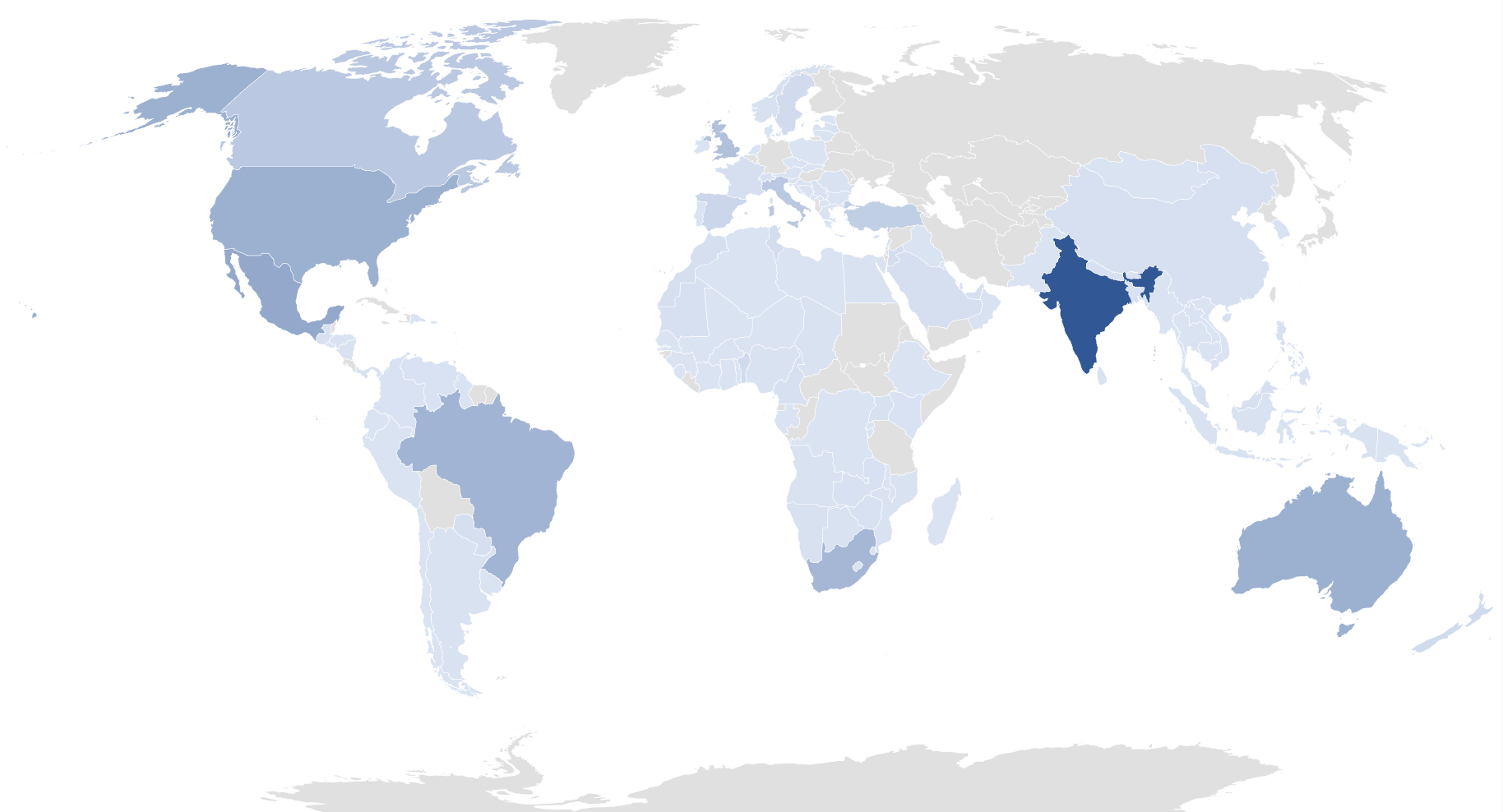
After analyzing the statistics related to the countries extracted from the dump, we can see that the victims are located in 137 different countries, being India the most affected country (~22%). After India, we have Mexico (~91K records), then United States and Australia at the same level (around 80K records), Brazil (~72K), and South Africa (~68K). It is important to highlight that some of the countries in the European continent are also present in the TOP15, with United Kingdom leading the list (~53K), followed by Italy (~41K) and then also Spain (~19K) and Sweden (~12K), among others.
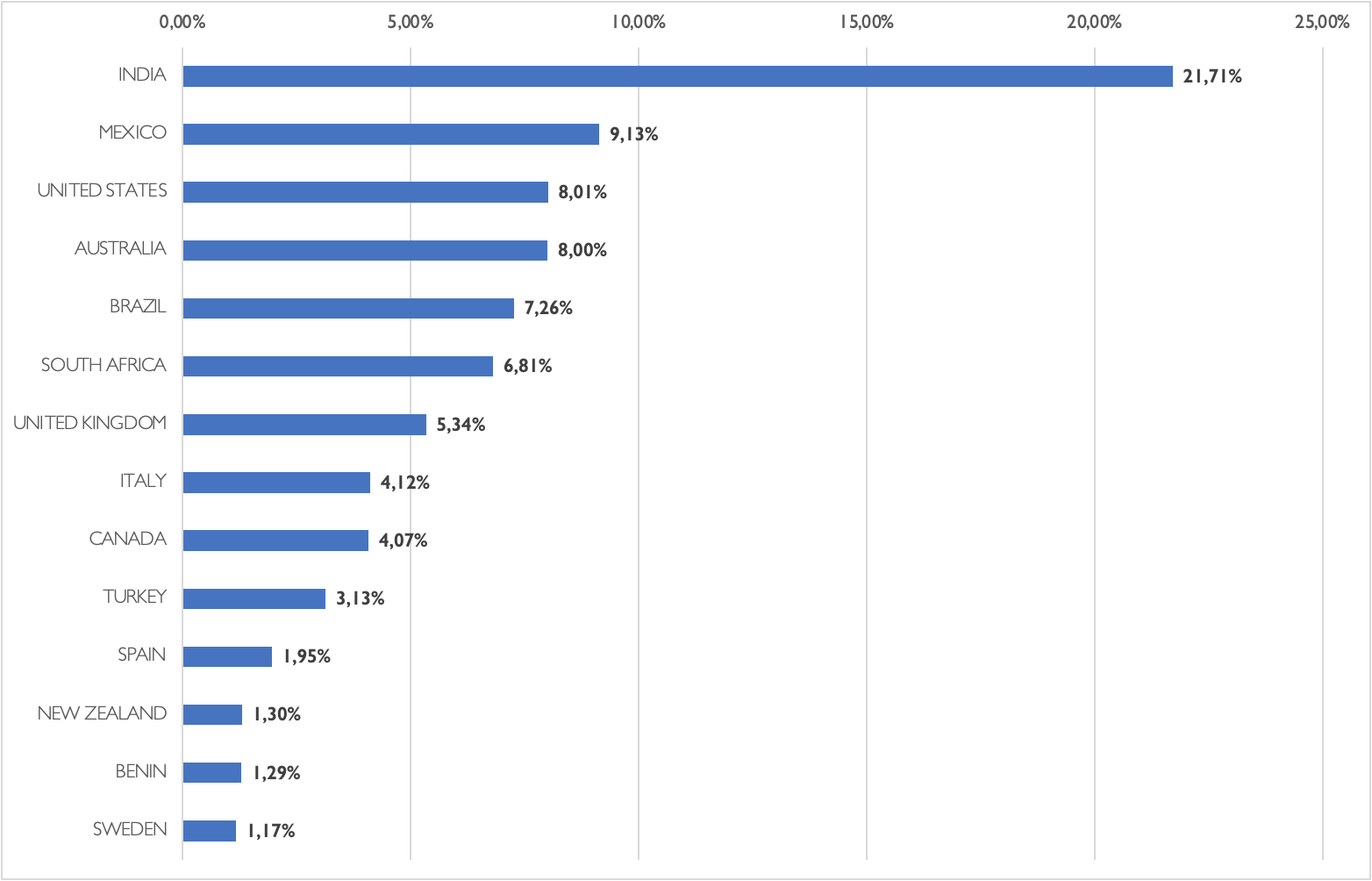
This spread geographical distribution might strength the theory that the potential sources of the stolen cards were phishing and digital skimmers, which are easier to “deploy” worldwide than POS malware or physical skimmers.
This victim’s location distribution could also mean that there are several credit card providers and not just one provider, and each might be targeting different regions and countries.
Underground reactions
The popularity of the shop is questionable as it has attracted a lot of initial attention since the release of its free cards, but, according to some feedback from forum members, the shop itself still needs improvements. A popular opinion is that the shop’s sites are constantly down and the support is slow – and as one forum member said “to become a top player in the market you need to fix this”. Therefore, the operational side of the card shop is still unsettled, which is very negative to its reputation and credibility. Both the clearnet and the onion version of the card shop site were reportedly unstable in the past few days:
However, AW_cards confirmed that the shop was under a Distributed Denial of Service (DDoS) attack and that was the reason for the site’s instability:

Despite these negative events, clients do not seem to complain about the quality of the products. In short, due to its sudden rise to the spotlight, All World Cards creates a situation of uneasiness to the card shops market; consequently, reactions to its emergence are diverse and have different intentions. This might be explanatory of the reason for the DDoS that the card shop has been suffering, which contributes to the worsening of the shop’s reputation and placement at the market. At the same time, reviews from clients and interested customers speak highly of the shop, mostly regarding prices and products. It is likely that after this initial buzz – especially around the 1 million free cards campaign – things will settle down and we will be able to get a clearer picture of the true worth of the card shop. In the meantime, customers’ reviews are a great thermometer to evaluate the prospects of success of All World Cards.
Threat Actor behind All World Cards
Using either AW_cards or AW_support nicknames, the card shop operators registered to popular underground forums such as XSS, Club2CRD, CardVilla, and Blackbones on May 21, 2021. It took another month for the threat actor to register the account AW_support on the top-tier Russian forum Exploit.
On the same day of the registration on XSS, the threat actor deposited 0.27 Bitcoin into their account. Threat actors typically do this to be more trusted in deals, partnerships, and job offers. If a threat actor is accused of scamming, the XSS admin or other forum moderators act as an arbitrator and pay off the affected customers with the money available in the deposit. Therefore, this action by AW_cards had the objective of making the new credit card shop look more reliable to the potential clients.
Remarkably, AW_cards is also the sponsor of the 6th articles competition of the top-tier Russian speaking forum XSS, named “XSS Hot Summer”, which distributes US$15,000 among the 7 best contestants publishing about penetration tests, bypassing security solutions, vulnerabilities, hacking, etc. Previous editions of the competition were sponsored by well-known threat actors like the REvil ransomware representative “Unknown” and the LockBit Group. Again, this action shows underground and “business” experience by the actors behind All World Cards.
Like many other prominent card shops, they have also advertised All World Cards placing banners in the Blackbones underground forum. This forum also has ads from FERum Shop, Moneyclub, among other card shops.

Furthermore, AW_Cards has been looking for suppliers. Establishing partnerships with card suppliers enables the card shop operators to increase the number of cards for sale. If they manage to provide a better deal than other popular card shops, prominent card suppliers may switch teams and start working with All World Cards.
The contact information provided in forums is the same listed on their card shop, focusing on communications via private messages and Jabber. AW_support also clarified that they do not manage any Telegram account, probably trying to avoid scams.
All World Cards is offering opening discounts up to 70% off, according to posts made by AW_cards. Thus, by now their prices are very competitive in comparison to their competitors’: depending on the level of details a card offers (owner’s name, email, address, etc.) and its characteristics, the prices range between US$5,5 and US$9,6. For comparison purposes, the prices of FERum Shop, another major card shop, range between US$6,9 and US$16,8. Hence, the combination between a satisfactory validity rate and inviting prices offers good competitive advantages to the newcomer All World Cards.
As it is common in this kind of underground services, the shop also has a section where customers can communicate with the administrators about different topics. In this case, this section “Tickets” allow the customers to send messages about the following categories: Paymenth [sic] problem, Technical problem, Offer, Want be supplier, Problem with CC. Good support to buyers is also key in the success of a card shop, solving issues when the goods quality is not as good as expected (using refunds, for instance).
The number of cards offered and how they operate and advertise clearly shows the threat actors behind All World Cards are not new players in the card underground ecosystem, even if the accounts and nicknames used are quite new in forums. It is quite likely that they chose to use brand new forum usernames and Jabber addresses to avoid being tied to any previous activity.
Summary of activities
- 17-05-2021: The domain allworld[.]cards is registered.
- 21-05-2021: Registration in multiple underground forums.
- 31-05-2021: 1st post advertising the card shop in underground forums.
- 31-05-2021: AW_Cards deposits 0,27 Bitcoin into their XSS account.
- 04-06-2021: The XSS administrator announces AW_cards’s sponsorship.
- 02-08-2021: They share 1 million compromised card details for free.
- 07-08-2021: They publish post looking for bank cards suppliers.
- 10-08-2021: They add several thousands of new compromised cards to All World Cards.
Conclusions
The cybercrime ecosystem is always evolving and the specific case of the carding community is not an exception. Like we mentioned in our post about the “State of Underground Card Shops in 2021”, it is fairly common to see new shops appear while others shut down. All World Cards appeared in May 2021 for the first time and their owners decided to promote their shop releasing one million credit cards to the cybercriminal community, besides trying to become more popular via sponsoring activities in some forums like XSS. The credit card analysis shows that those cards were likely stolen via phishing or digital skimmers (Magecart schemes) in 2018/2019. Even if this stolen data might seem old and obsolete, some of these cards were still valid at the time of their publication. It is likely that the original data was provided by different threat actors focusing on different regions, like the geographical distribution of victims and the diverse format of the records show.
Possessing this amount of cards is already a proof of experience and relevance in the carding world, giving more confidence about the All World Cards administrators.
In the cybercriminal community, providing proves of life is quite common, but releasing a big amount of still valid and relevant credit card information is not. The actors behind All World Cards are clearly trying to become more popular and compete face to face with other relevant card shops like FERum Shop or Brian’s Club. However, this attention will also have other consequences like the DDoS they suffered in the past days and they will need to find credit card providers, who usually “sign” exclusivity to a specific shop. Like we always mention, the cybercrime services and providers use similar business models to legitimate businesses, and this shop is a good example of that.
We will need to wait some time before knowing if All World Cards becomes a top shop for the carding community after this impacting “marketing campaign” and their sponsorship efforts.
Our Card Theft module in our Threat Compass solution provides proactive monitoring and alerts in real-time on stolen and leaked card information related to your company. Threat Context, Outpost24’s Threat Intelligence module, provides insights about threat actors and the cybercriminal ecosystem to join the dots and help to prioritize defenses.
