
Proactive Cybersecurity Strategy: Reducing Risk Ahead of Time
A proactive cybersecurity strategy is no longer optional. Learn why and how you can implement proactive security in your organization.
Read moreGet continuous visibility of your attack surface with actionable context for faster defense against threat actors targeting your organization.
Cybersecurity is not a project; it’s a journey.
We’re here all the way with you.
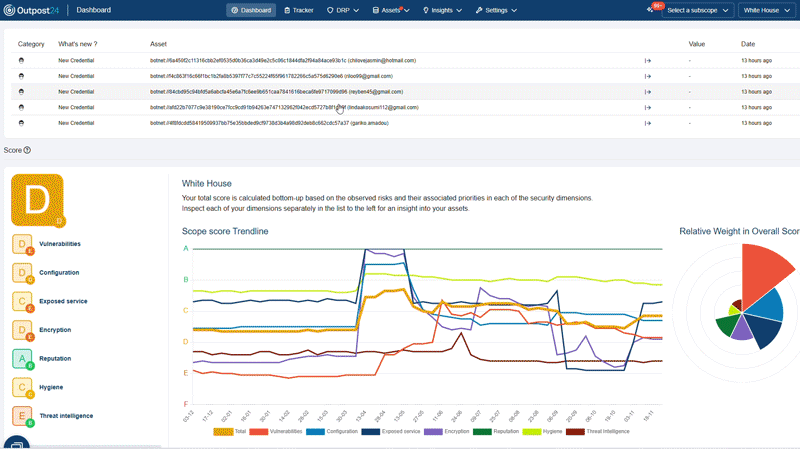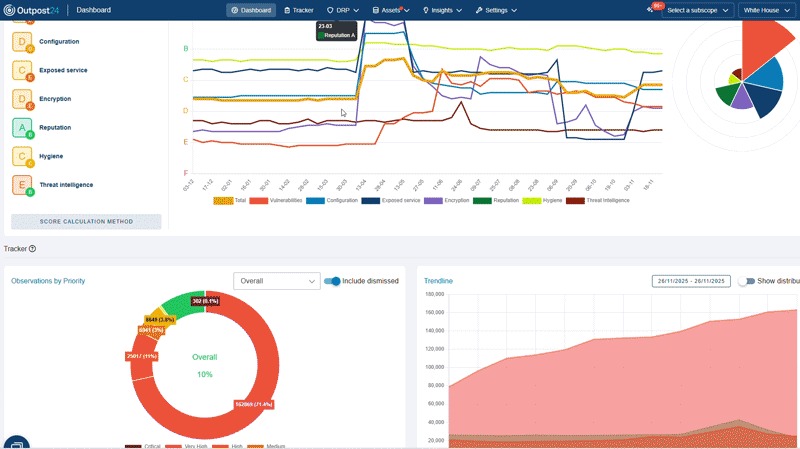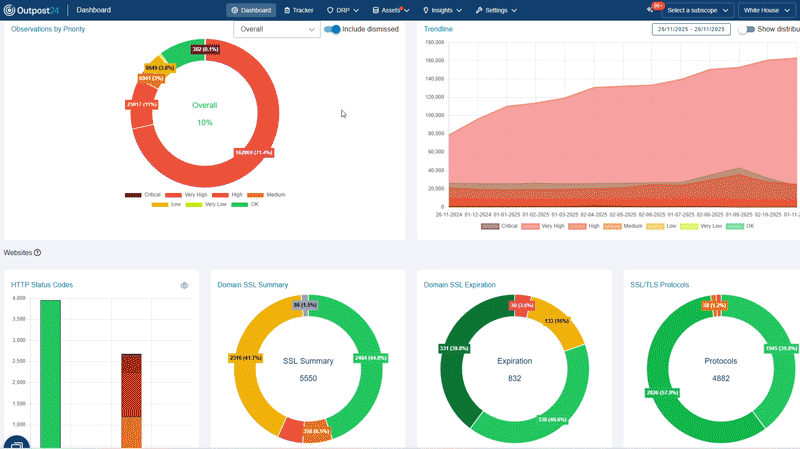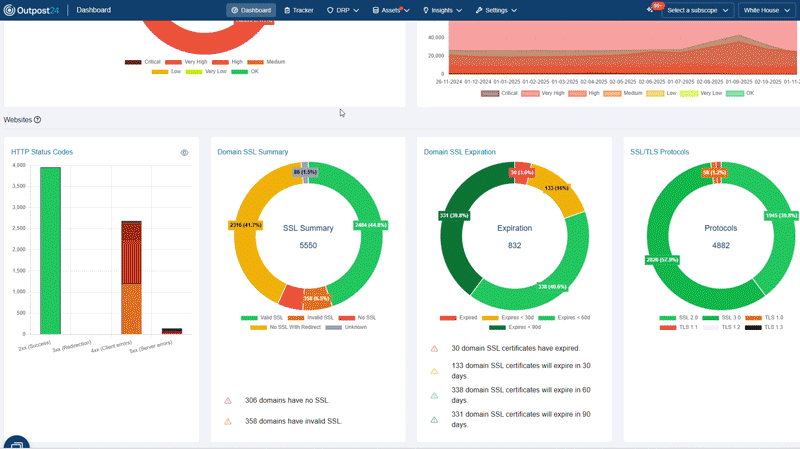
A cloud-based platform that provides you continuous 360° visibility of your growing attack surface with relevant context. Our unique AI-powered data enrichment modules analyze all your known and unknown internet-facing assets for vulnerabilities and attack paths, so you can take confident action.
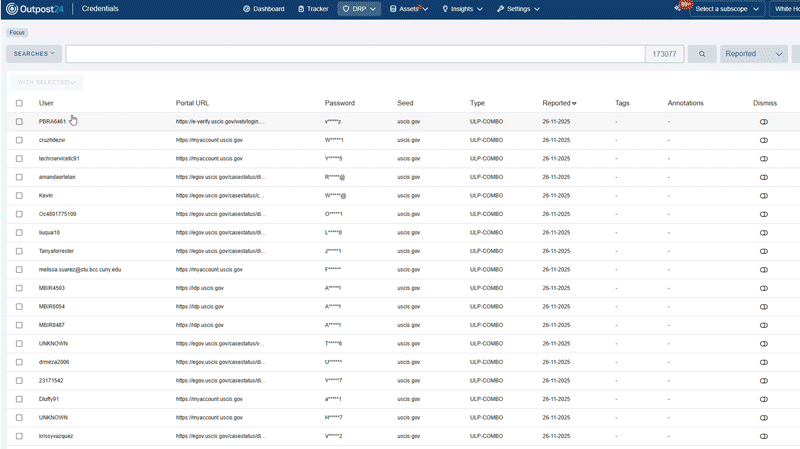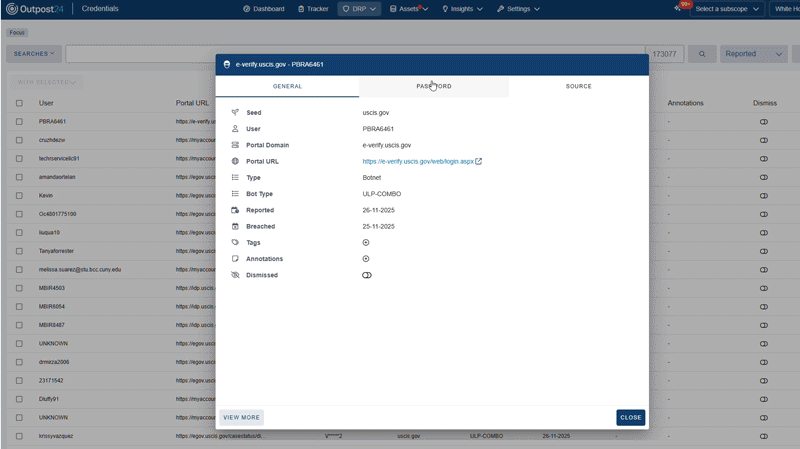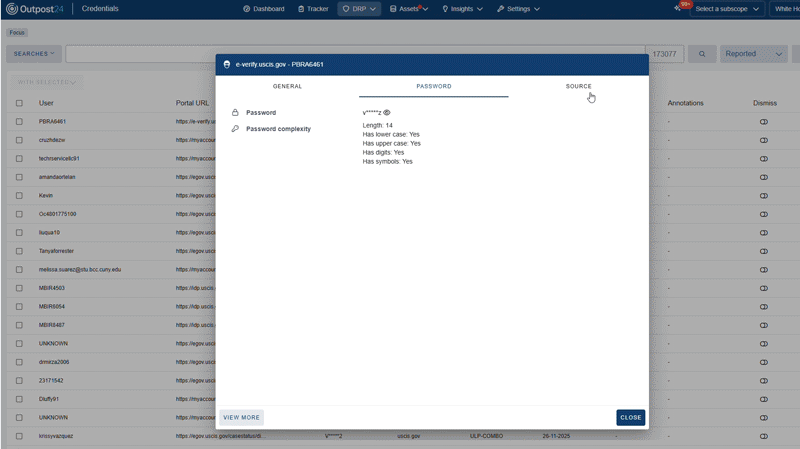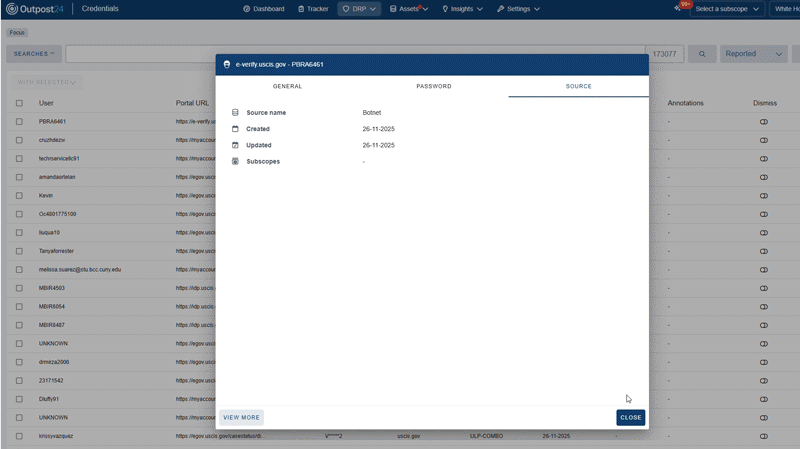
A single cloud-based solution that combines asset discovery with threat intelligence DRP. You can monitor your known (and unknown!) public-facing internal assets, as well as threats from external channels across the open, deep, and dark web. Once identified, these threats are prioritized and ready for remediation.
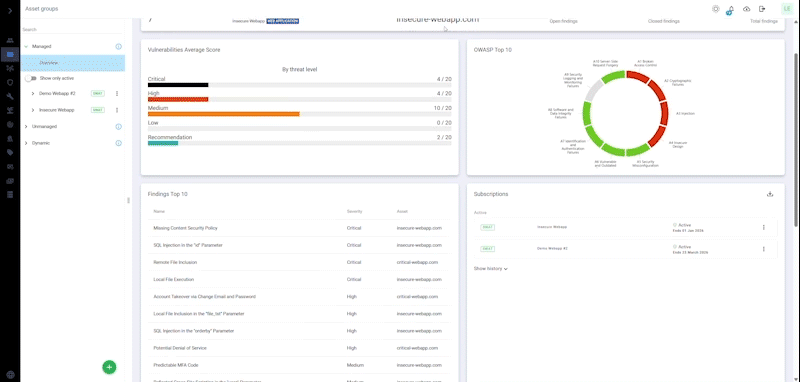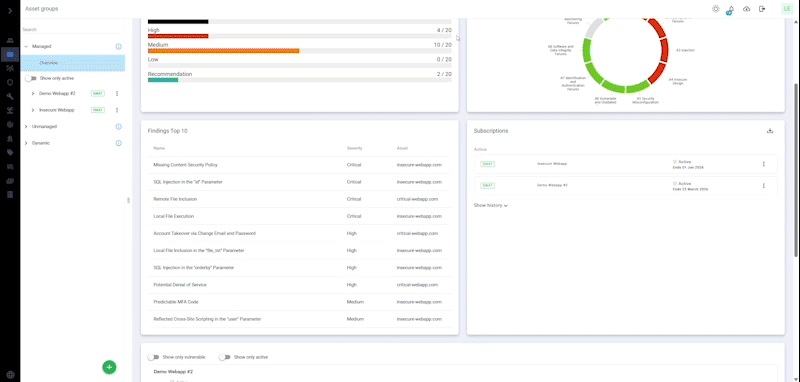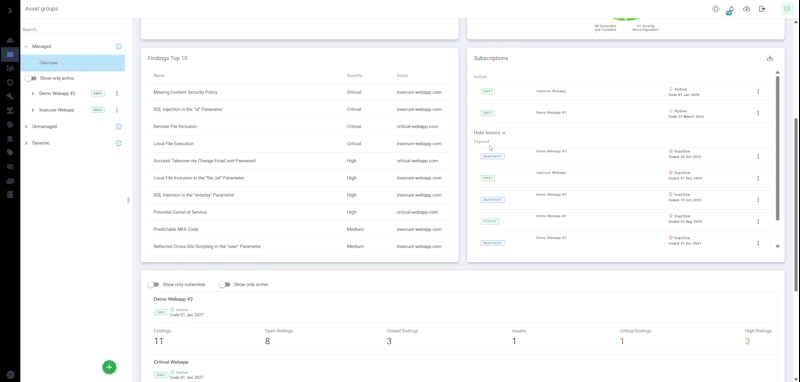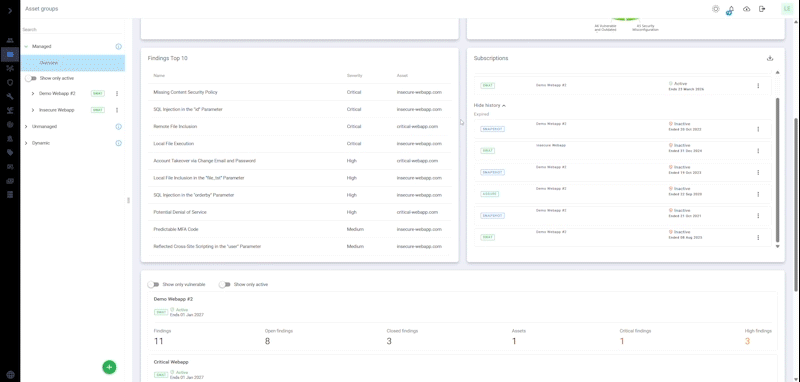
A comprehensive solution that automatically and continuously monitors your internet-facing web applications for the latest vulnerabilities, ensuring nonstop protection, zero false positives and results verified by our certified pen testers.
Cybersecurity is not a project; it’s a journey. We’re here all the way with you
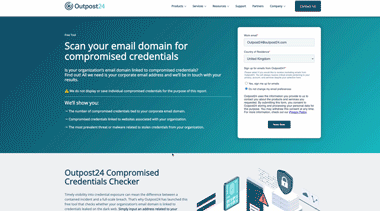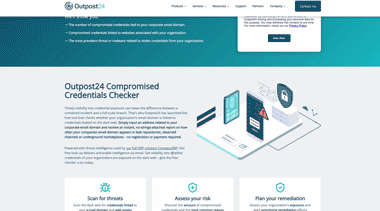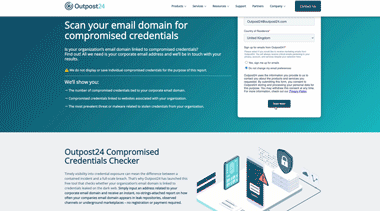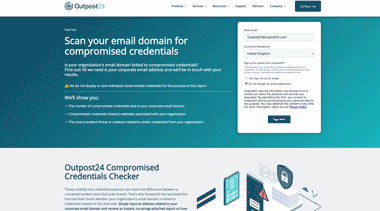
Credentials Checker
Timely visibility into credential exposure can mean the difference between a contained incident and a full‑scale breach. Check whether your organization’s email domain is linked to credentials exposed on the dark web with Outpost24 free Credential Checker.
Check our latest research, blogs, and best practices to level-up your cybersecurity program.

A proactive cybersecurity strategy is no longer optional. Learn why and how you can implement proactive security in your organization.
Read more


Understand the importance of CMDB accuracy in cybersecurity, and how security teams can ensure their CMDB can remain up-to-date.
Read more


Threat actors are increasingly targeting the insurance industry. Understand the tactics these groups use with analysis from Outpost24.
Read moreLet’s talk about your security goals and how we can help you get there. With Outpost24, you will experience: