Cyber Threat Intelligence
Detect and deter external threats to your business with our modular cyber threat intelligence solution. The Digital Risk Protection (DRP) modules cover the broadest range of threats on the market and deliver actionable intelligence to maximise incident response performance. Empower your security teams with a central point of control for automated, operational, tactical, and strategic threat intelligence.
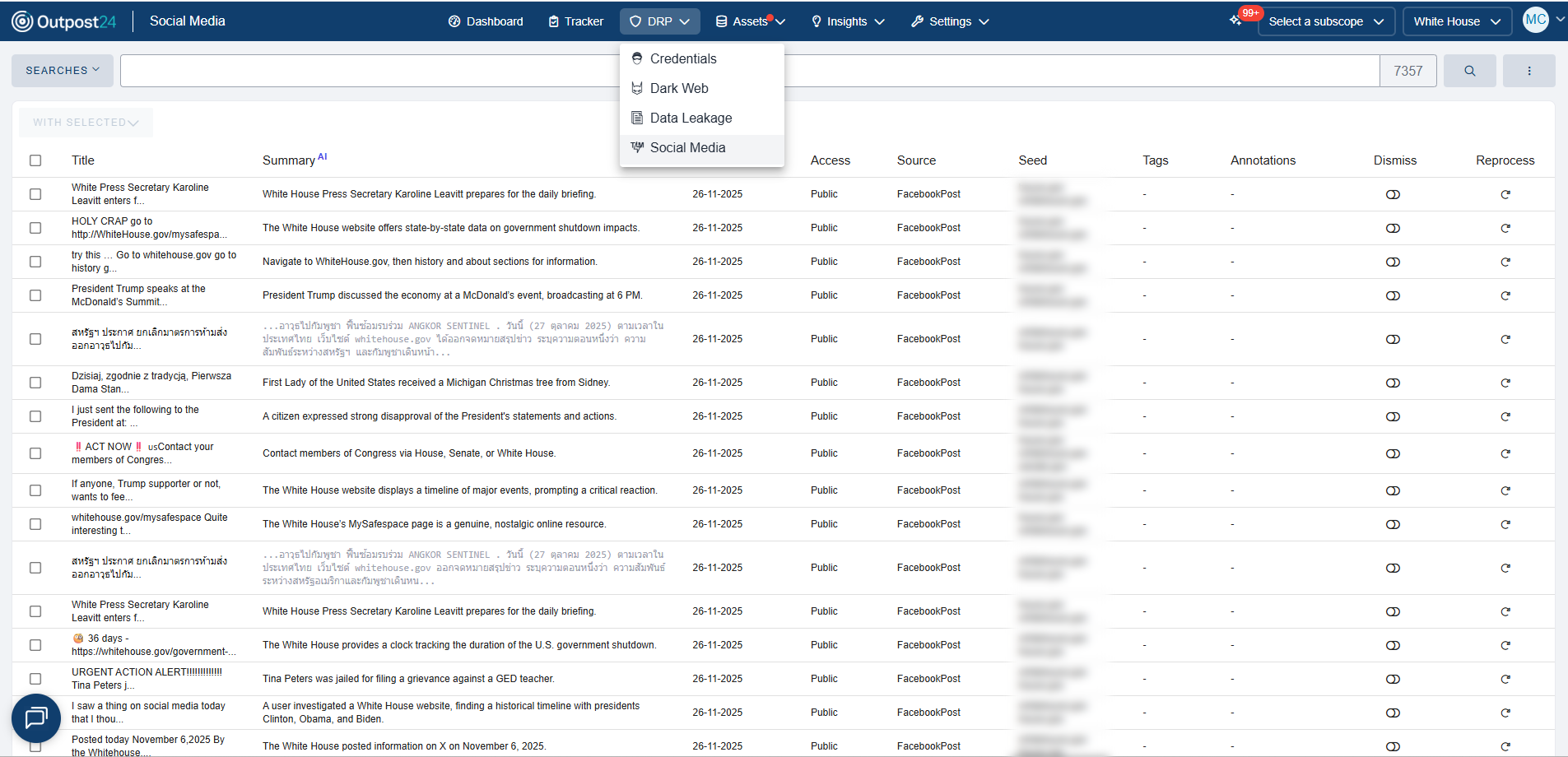
Our Cyber Threat Intelligence Solution
Each Cyber Threat Intelligence module is backed up by our world-class in-house analyst team. Enrich and contextualize threats so you can defend your assets and understand your adversaries’ plans before they strike.

Credentials
Detect and retrieve your compromised credentials in real-time.

Data Leakage
Detect leaked documents and information from employees & third parties.

Domain Protection
Combat phishing and cybersquatting attacks with automated detection of malicious sites.

Dark Web
Track and monitor your organization’s footprint on the Dark Web.

Hacktivism
Monitor global social borne hacktivism operations and protect your networks and employees from potential attacks.

MRTI Feed
Access millions of IOCs in real-time and manage threats more efficiently.

Social Media
Track your organization’s digital footprint, including unauthorized use of brands, logos, and assets.

Threat Explorer
Mitigate and prioritize risks with advanced vulnerability intelligence and custom alerting.
Features
- 13+ years of historical threat data
- Data gathering from open, closed, and private sources
- Human-verified delivery that minimizes false positives
- Big data analytics with context and underlying details
- STIX/TAXII threat data integration and information sharing
- Plugins available for SIEMs, SOAR, and TIPs
- Dynamic risk-scoring system to feed vulnerability management programs via API
- Flexible business model for different partnerships, including MSSP programs
- Combine with External Attack Surface Management to get a full overview of the threats facing your attack surface
- Easily automate actions with our built-in automation engine

How Cyber Threat Intelligence works
We continuously search the open, deep, and dark web to discover customer-specific threat information, using automated technology for speed and scale. We retrieve and deliver this intelligence in a modular format, giving customers a straightforward way to confront external cyberthreats and manage their digital risk.
The only European Cyber Security Company named an Overall Leader in KuppingerCole’s 2025 ASM Leadership Compass
Outpost24 was also recognized as a leader in both the Product and Market categories by KuppingerCole, leading analysts in the areas of digital identities, authentication, and cybersecurity.
Threat Intelligence Team
Our dedicated in-house threat intelligence team, KrakenLabs understand the critical importance of staying ahead in today’s ever-evolving cyber threat landscape. We specialize in providing bespoke, in-depth threat analysis and reports tailored specifically to your organization. Our services equip you with actionable insights into the latest activities from Threat Actors including IOCs, vulnerabilities and TTPs targeting your organization in an easy to digest format. We also offer expert guidance and services on proactive measures to protect your organization including threats coming from the Dark Web, breach analysis, and OSINT assessments, to ensure your organization stays one step ahead of cybercriminals.

Frequently Asked Questions
A cyber threat intelligence solution can help businesses identify the threats that are targeting them, and reduce incident response times. It can also identify if a compromise has already occurred.
Threat Intelligence by Outpost24 covers a broad range of threats on the market. With its pay-as-you-need modular architecture, you can choose the modules that are most relevant for your business.
Out Threat Intelligence solution can detect both leaked credentials in underground markets, and stolen credentials obtained by malware. Our infrastructure of sinkholes, honeypots, crawlers, and sensors are continuously searching, and can also capture credentials obtained by malware in real-time.
You can configure our solution in a matter of minutes, and get high-impact results almost immediately. The cloud-based solution eliminates the need for software installations, or endpoints.
Outpost24’s Threat Intelligence solution offers API integration with other systems. The solution also supports STIX/TAXII for easy information sharing between different data formats, and platforms.
Yes. Out threat information is backed by human intelligence. Our in-house threat intelligence team, also known as KrakenLabs, is dedicated to providing and analyzing threat intelligence within our tool, such as Threat Actor profiles, IOCs, CVEs, attack patterns, signatures, and malware. This ensures that all the information delivered to you is timely, accurate and of the highest quality.
Success Stories
Threat Intelligence enabled one of the world’s largest telecom companies, Telefónica to provide specific, predictive, and actionable intelligence to their clients for accelerated decision making.
Request A Live Demo
Please fill in your information to submit a demo request. All fields are mandatory.