
Pulled Pork and Watermelon: Why Integrated Cybersecurity Depends on Unlikely Synergies
Learn how a more integrated cybersecurity environment can enable stronger defense with advice from Outpost24 experts.
Read moreContinuous 360° visibility into your organization’s external attack surface, with the context to understand what really matters.
Get automatic, comprehensive discovery of both known and unknown internet-facing assets and their vulnerabilities with Outpost24’s EASM Platform.
Get visibility into both public-facing internal assets and external threats across the open, deep, and dark web in a single cloud-based solution.
Combine the power of Outpost24’s EASM solution with our certified penetration testing experts and PTaaS to discover, test, and validate both known and unknown applications.
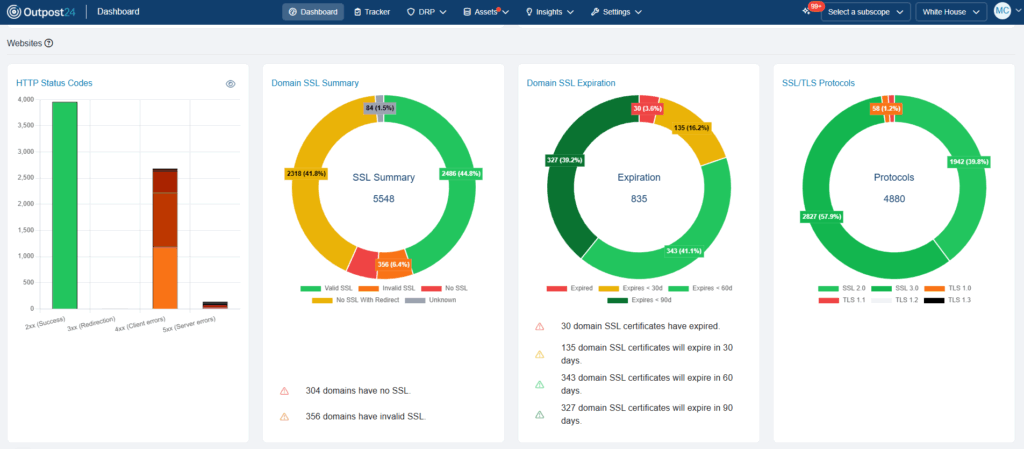
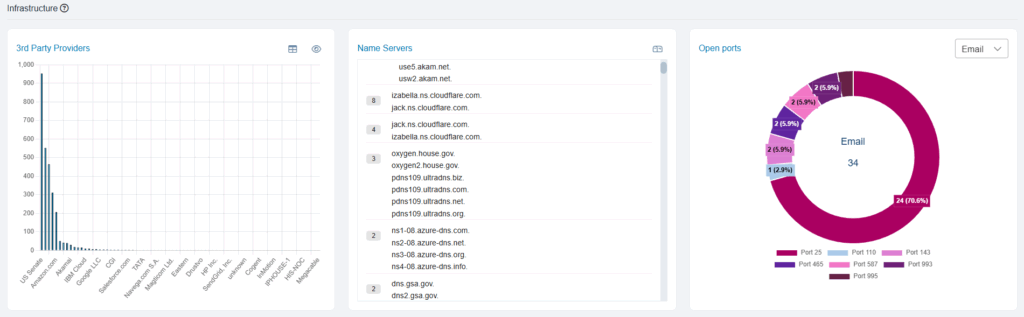
Automatically discover all known and unknown internet-facing assets, uncovering relationships across domains, subdomains, IPs, cloud instances, third-party integrations, and partner connections. Identify and mitigate threats proactively, before they become incidents.
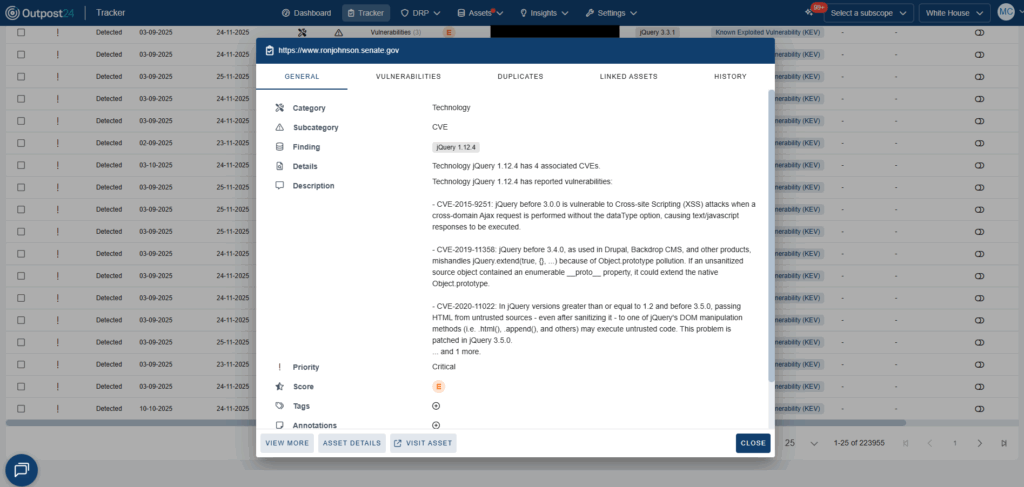
Integrate asset, vulnerability, and risk data into your SIEM, CMDB, or SOAR tools. Sync with ServiceNow or Splunk to streamline workflows and maintain a single source of truth.
Get real-time alerts that integrate with your tech stack and automate next steps for a faster, smoother remediation process.
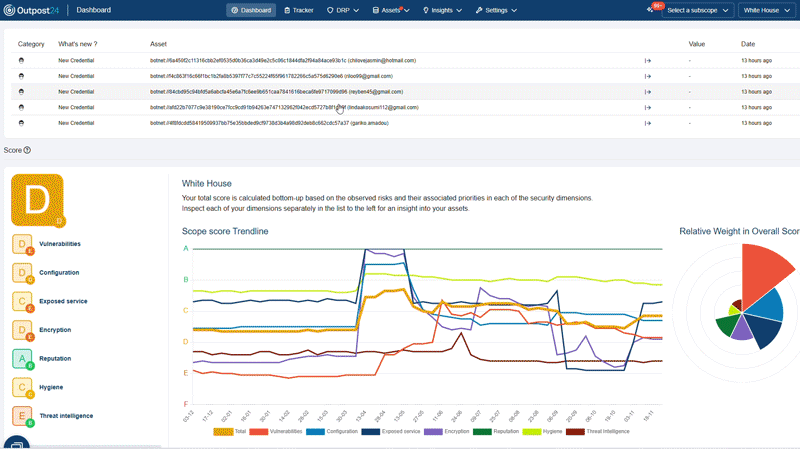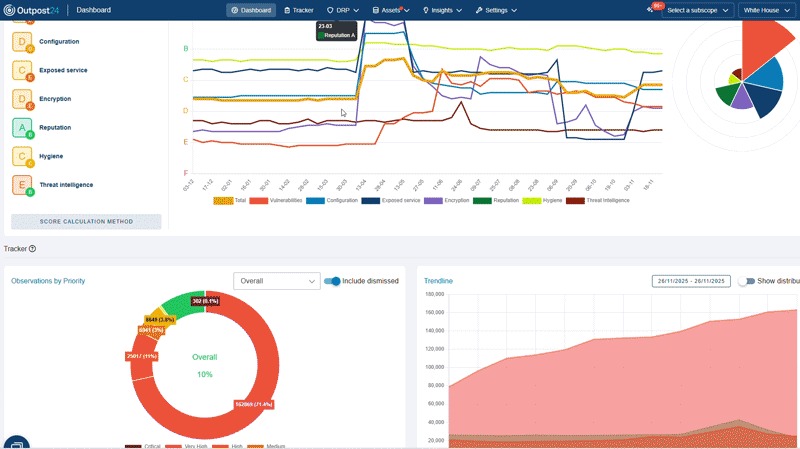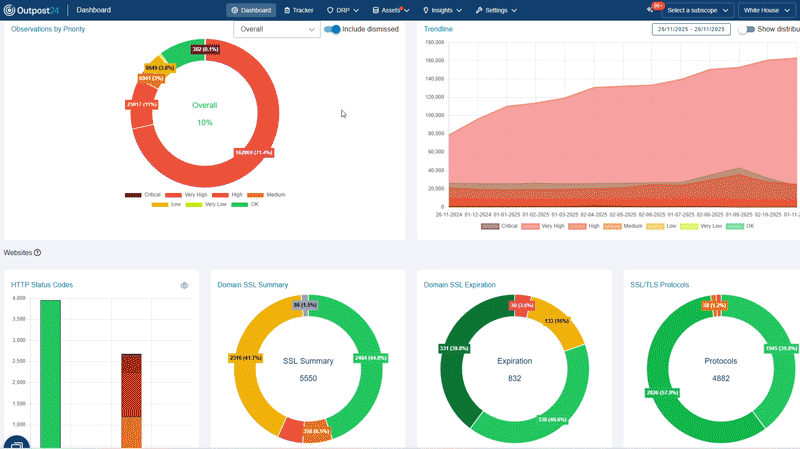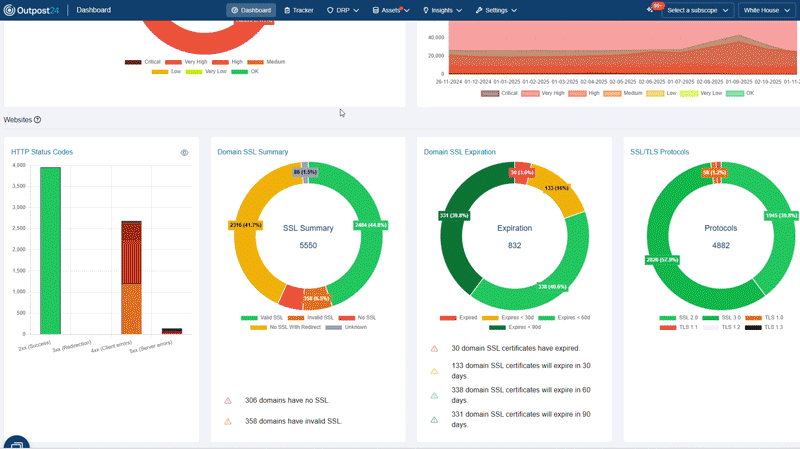
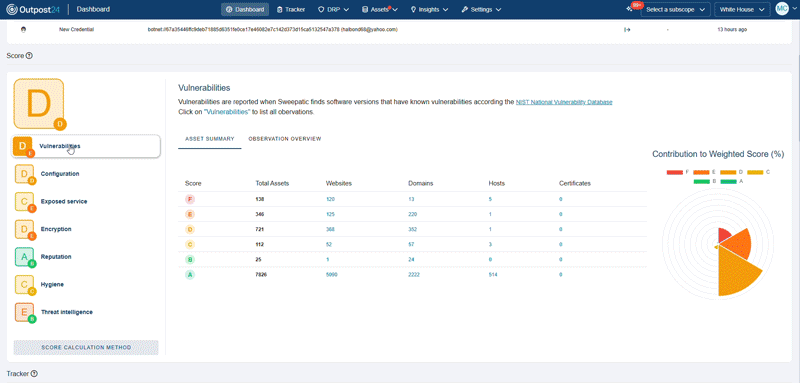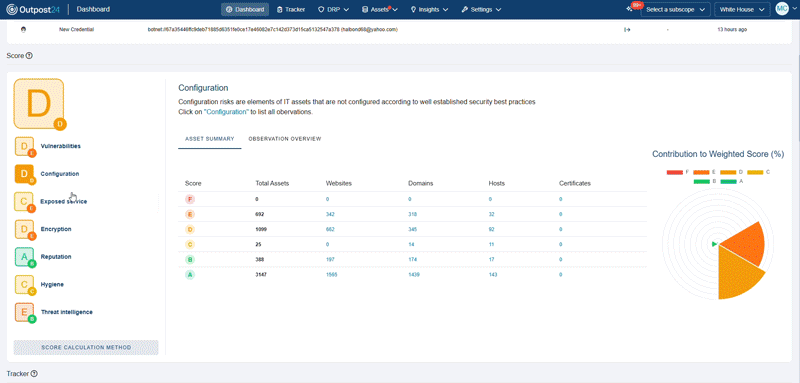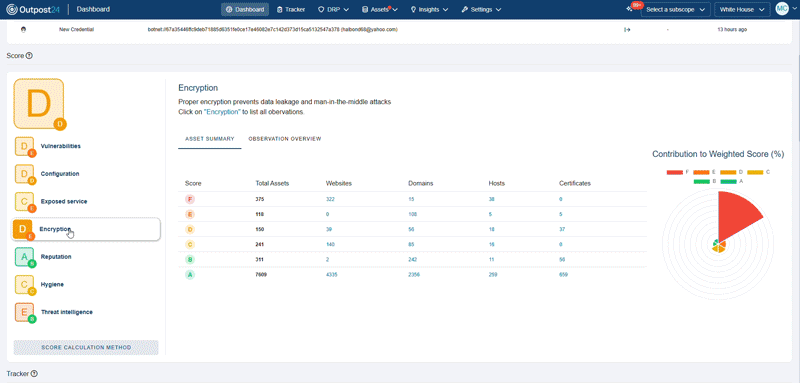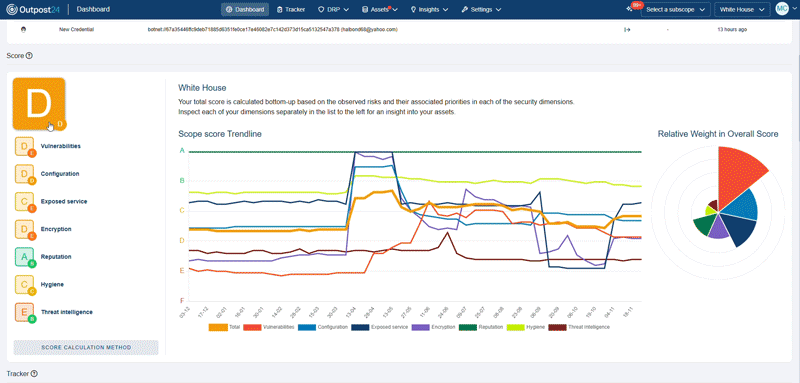
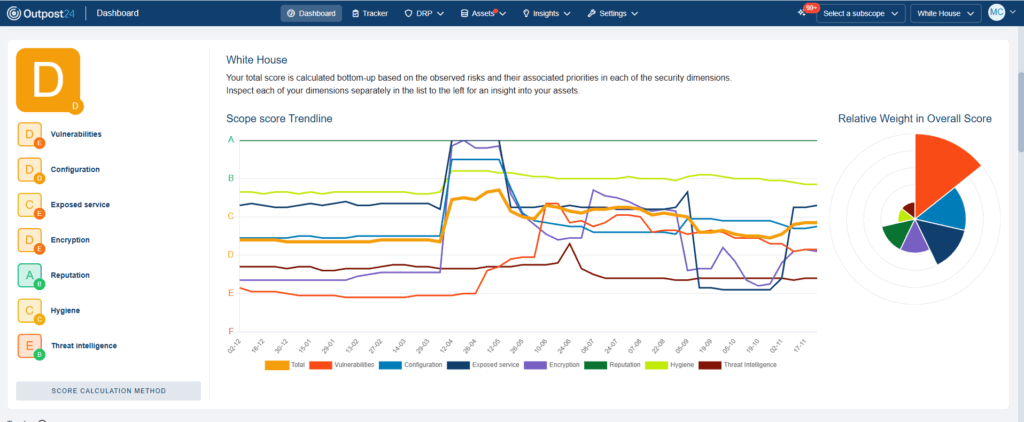
Get unique attack surface scoring and historical trends across your entire scope, at both the asset and observation level, along with industry benchmarks.


Let’s talk about your security goals and how we can help you get there. With Outpost24, you will experience:
Check our latest research, blogs, and best practices to level-up your cybersecurity program.

Learn how a more integrated cybersecurity environment can enable stronger defense with advice from Outpost24 experts.
Read more


Security teams drowning in alerts, executives demanding business justification for security investments, and an attack surface that grows daily – sound familiar? While traditional…
Read more


Shadow IT has evolved from an occasional nuisance to a pervasive security challenge that affects every organization. These unauthorized applications, services, and devices operating…
Read more