Expert Deployment Service Description
The Outpost24 Expert Deployment packages are directed at organizations that want to be up and running with the Outpost24 solutions quickly and according to best practices. With hundreds of successful deployment under our belt, the Outpost24 Managed Services team has years of implementation experience in customers’ environments and is skilled at advising the best suited deployment and configuration to fit your business needs and improve your security posture.
Deployment process
Depending on the scope of your environment the expert deployment timeline can vary between 1 and 3 months. Regardless of the scope, Outpost24 always follows a step-by-step process ensuring a successful deployment.
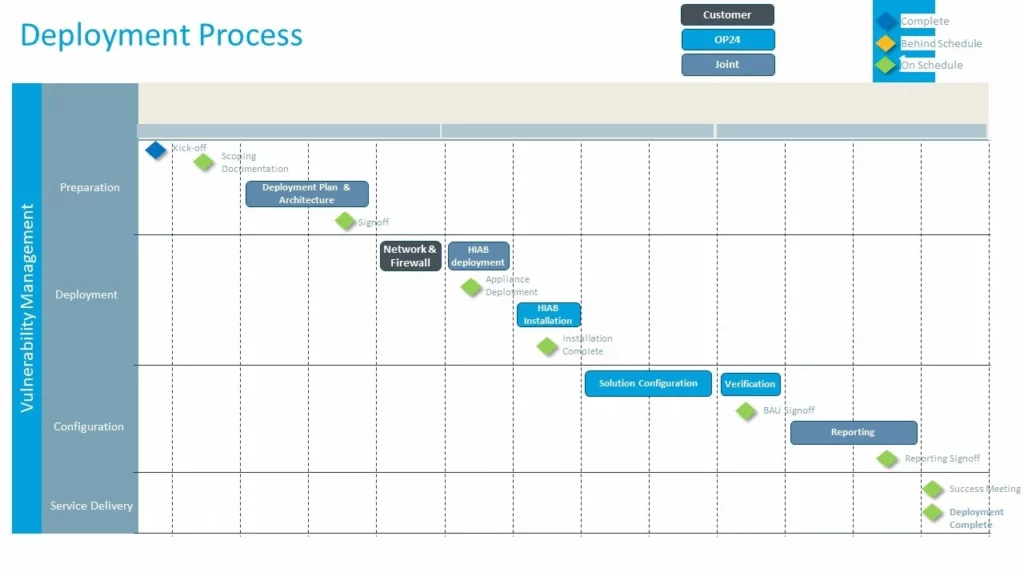
Image 1: Example of an deployment plan & responsibilities
The steps in the deployment process are as follows:
| Step | Customer | Outpost24 |
|---|---|---|
| Scoping Documentation | Provide an overview of the scope, including specific requirements for the deployment such as target structure or custom attributes | |
| Kick-off | Outpost24 will align with the relevant stakeholders, explain the deployment process, provide relevant documentation and discuss the requirements | |
| Deployment Architecture | Together with the Customer, Outpost24 will design the preferred architecture to fit your requirements and ensure the environment is scanned in the optimal manner. This will include the location of the scanners and place where the data is stored | |
| Access Method | Provide the required temporary access for Outpost24 to be able to access the environment and configure the solution | |
| Network & Firewall Rules | Implement required network changes and firewall rules in accordance with the determined architecture in order for the scanners to be configured and scan properly | |
| Scanner Deployment | Download and deploy the VM’s in your environment and provide an IP address | |
| Scanner Installation | Outpost24 will test access to the scanners and configure the distribution settings in line with agreed solution architecture | |
| Discovery Scanning | Outpost24 will perform a discovery scan on the environment to verify all active targets in scope | |
| Scan Policy Definition | Outpost24 will set up the preferred scan policy | |
| IP/Application configuration | Outpost24 will configure the IP’s or (authenticated) applications in the tool | |
| Target Grouping | Outpost24 will create a target structure in line with your business and according to the requirements indicated in the scoping document | |
| Event Notifications | Outpost24 will set up event notifications to your different teams ensuring you are notified when you want to be | |
| Scan Scheduling | Outpost24 will set up a scan schedule ensuring your environment in scanned successfully in a preferred timeframe | |
| User Configuration | Outpost24 will configure the users and their required user roles and access level | |
| Reporting Configuration | Outpost24 will create various report templates as well as scheduling these to be delivered to the different teams |
Package overview
| Step |
SMALL Up to 500 IPs |
MEDIUM Up to 2,000 |
LARGE Up to 10,000 |
X-LARGE Up to 50,000 |
|---|---|---|---|---|
| Architecture | ||||
| Requirement Assessment |
|
|
|
|
| Deployment Design |
|
|
|
|
| Deployment Assistance |
|
|
|
|
| Distributed Environments |
|
|
|
|
| HIAB Installation | 1 | Up to 5 | Up to 15 | Up to 30 |
| Configuration | ||||
| User Management |
|
|
|
|
| Target Management |
|
|
|
|
| Scan Templates |
|
|
|
|
| Event Notifications |
|
|
|
|
| Custom Attributes |
|
|
|
|
| Number or IPs | Up to 500 | Up to 2.000 | Up to 10.000 | Up to 50.000 |
| Non-authenticated Application Configuration | Up to 10 | Up to 25 | Up to 50 | Up to 150 |
| Authenticated Application Configuration | Up to 2 | Up to 5 | Up to 10 | Up to 50 |
| Cloud Configurations | Up to 10 | Up to 25 | Up to 50 | Up to 100 |
| Scanning | ||||
| Discovery Configuration |
|
|
|
|
| Scan Scheduling |
|
|
|
|
| Scan Policy Customisation |
|
|
|
|
| Netsec Authentication Setup |
|
|
|
|
| Asset Management |
|
|
|
|
| Standard CIS Compliance Scanning |
|
|
|
|
| Reporting | ||||
| Report Templates | Up to 3 | Up to 5 | Up to 10 | Up to 25 |
| Scheduled Reporting |
|
|
|
|
| Dynamic Groups |
|
|
|
|
| Maintenance | ||||
| Scheduled Updates |
|
|
|
|
| Automated Backup |
|
|
|
|
| Integrations | ||||
| AD/LDAP |
|
|
|
|
| Additional Integrations |
|
|
|
|
| Documentation | ||||
| Deployment Documentation |
|
|
|
|
| Implementation Diagrams |
|
|
|
|
| Implementation Timeline | ||||
| Time-boxed Implementation | Up to 1 m | Up to 1,5 m | Up to 2 m | Up to 3 m |
| Add-Ons | The Expert Deployment packages can be combined with the following services (price upon request) | |||
| User Training | Outpost24 offers a variety of education packages ranging from Instructor-led courses, customized education, certification and developer training | |||
| Expert Support | https://outpost24.com/service-description/customer-support | |||
Implementation Prerequisites & Conditions
- Scoping documentation has to be completed by customer in advance of project start date
- Customer is responsible for internal alignment within different teams/Opco’s/Sites/Business Units
- Customer is required to submit internal change requests for Appliance installations, firewall rules, whitelisting etc.
- All implementation projects are supported remotely. Any on-site requirements need to be scoped separately and will include travel and accommodation costs
- User training is not part of the implementation services and will have to be scoped separately by the Outpost24 Training Department.