Salesforce breach escalates: Qantas & Vietnam Airlines data leaked on dark web
The recent developments surrounding the Salesforce data breach serve as a stark reminder of the persistent threats organizations face. What began as a concerning incident earlier this summer has now escalated dramatically, with threat actors following through on their threats and releasing a substantial trove of Qantas customer data to the public.
This serves as a real-world demonstration of the evolving nature of threats, organizational attack surface and a critical wake-up call for IT leaders to manage their exposure.
Timeline of the incident
The Qantas data breach began on June 30th, 2025, when the company detected unusual activity on a third-party customer service platform, leading to a confirmation of a cyberattack on July 2nd, 2025. The breach exposed personal information of up to six million customers.
| Date/Period | Event | Significance |
| Mid-2025 | Initial intrusions began, targeting Salesforce instances of global organizations via social engineering and third-party app compromises (e.g., Salesloft Drift). | Attackers secured data without breaching the core Salesforce platform itself, exploiting customer-side vulnerabilities. |
| October 6th, 2025 | Scattered LAPSUS$ Hunters launches a dedicated Data Leak Site (DLS), listing 39 victims and issuing a final ransom deadline. | The extortion campaign enters its public phase, weaponizing brand reputation. |
| October 10th, 2025 | The final ransom deadline passes without payment from Salesforce or the victims. | The critical pivot point: the threat actors lose their leverage, leading to the data dump. |
| October 11th-13th, 2025 | Qantas and Vietnam Airlines data, along with data from four other victims, is publicly released onto the dark web. | The breach escalates to a full-blown public crisis, demonstrating the actor’s intent to damage non-paying victims. |
| October 15th, 2025 | The DLS is compromised. | Uncertainty about what will happen with the stolen data increases. |
Our analysis of the escalation and public exposure
Scattered LAPSUS$ Hunters, have followed through on their ultimatum. This is a significant data dump designed to inflict maximum reputational and financial damage.
Our ongoing analysis of the threat group’s Data Leak Site (DLS) and Telegram channels reveals a concerning picture. So far, we’ve identified six victims whose data has been publicly exposed in connection with this Salesforce attack.
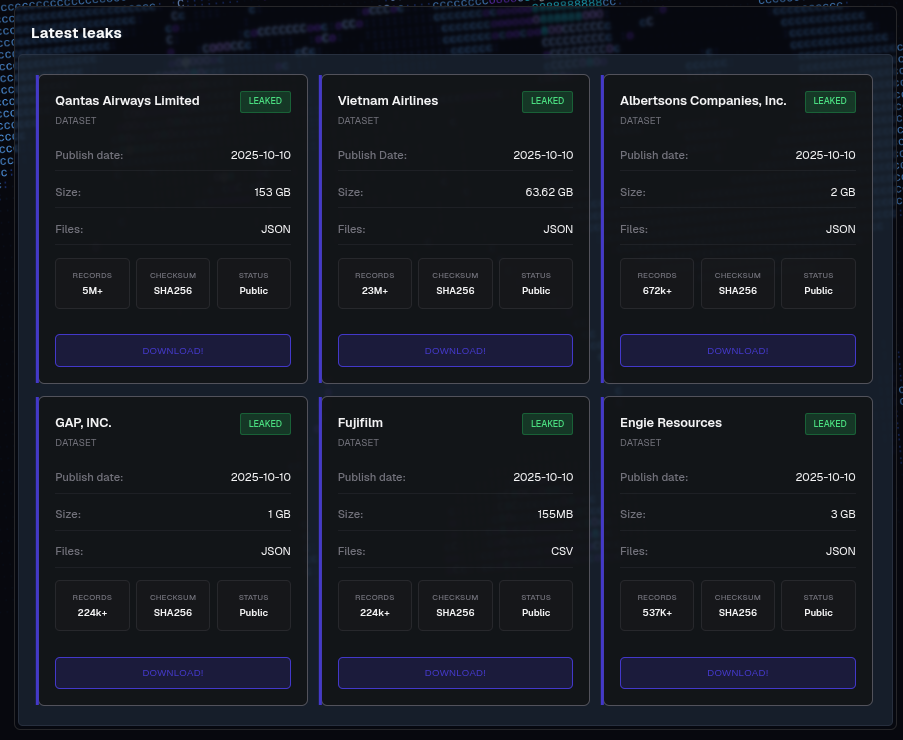
- Qantas: Approximately 153GB of client data, affecting over 5 million customer records, was released. This data includes names, emails, dates of birth, and frequent flyer numbers: all the components needed for highly effective spear-phishing and social engineering attacks.
- Vietnam Airlines: A substantial 64GB of customer data, including over 7.3 million unique customer email addresses and related PII, was also exposed.
- The Broader Risk: These two airlines are the largest of six victims whose data has been leaked so far, with the threat group listing over 30 other organizations whose data they claim to hold.
What we understand about Scattered LAPSUS$ Hunters: The playbook
The threat group’s activity during this whole campaign, as well as on both their DLS and Telegram channels highlights their sophistication and determination. They are not simply passive data holders; they are active communicators, leveraging these platforms to:
- Publicly name and shame victims: The DLS serves as a public ledger of their “achievements,” listing companies they claim to have breached and whose data they intend to release. This public shaming tactic adds immense pressure on victim organisations.
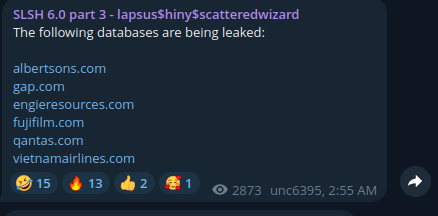
- Issue threats and ultimatum: Through Telegram, they communicate publicly, issuing threats and setting deadlines for ransom payments. Their public communications often display a confrontational stance, even towards law enforcement and security researchers.
- Showcase “proof” of compromise: Before a full data dump, they often release small samples of data as “proof of life” to legitimize their claims and further pressure victims.
- Coordinate and recruit: While less overt, these platforms can also serve as a means for the group to coordinate their activities and potentially even recruit new members or affiliates.
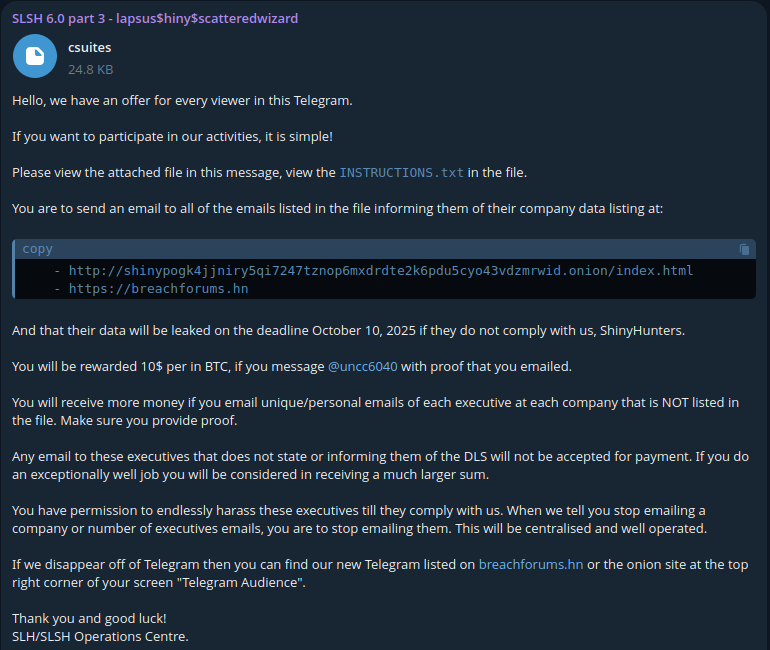
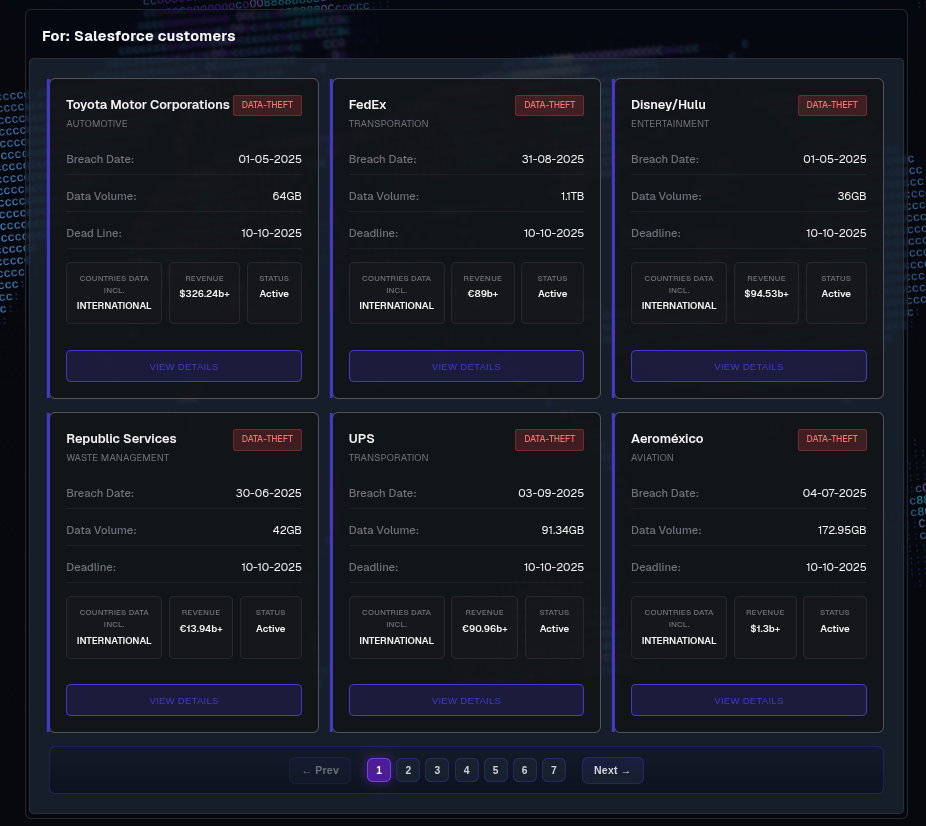
The significant volume of data released from Qantas and Vietnam Airlines, coupled with the group’s ongoing threats against 39 other listed companies, suggests that this could indeed be just the beginning. The impact on customer trust, brand reputation, and regulatory penalties for these organisations will be substantial.
Compromised data leak site (DLS)
Now, as such a complex name suggests, the threat actor seems to be a coalition of three groups. Or at least, of some of their members. This increases the difficulty of analyzing and keeping track of these incidents, as well as predicting what will happen next.
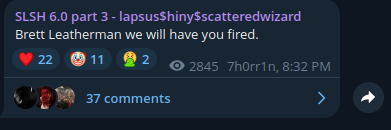
Late on October 15th, the DLS was compromised. At the time of writing, it’s still uncertain who the hacker was, but it appears that the reason for the attack was discontent about the use of the “ShinnyHunters brand” that Scattered LAPSUS$ Hunters is using.
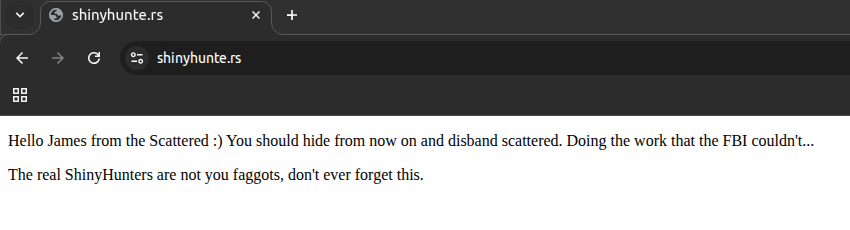
Post confirming the DLS is compromised
This is good news that the information is no longer available, right? Well, not necessarily. First of all, it was publicly available for about five days, so it has most likely already fallen into the hands of those who plan to use it. Second, now it will be more difficult to monitor the release of further stolen data and warn the victims.
It also increases uncertainty about how many people might have had access to the totality of the information exfiltrated from Salesforce, and what they plan to do with it. Finally, it looks like Scattered LAPSUS$ Hunters are really not that bothered by this and will most likely keep on going.
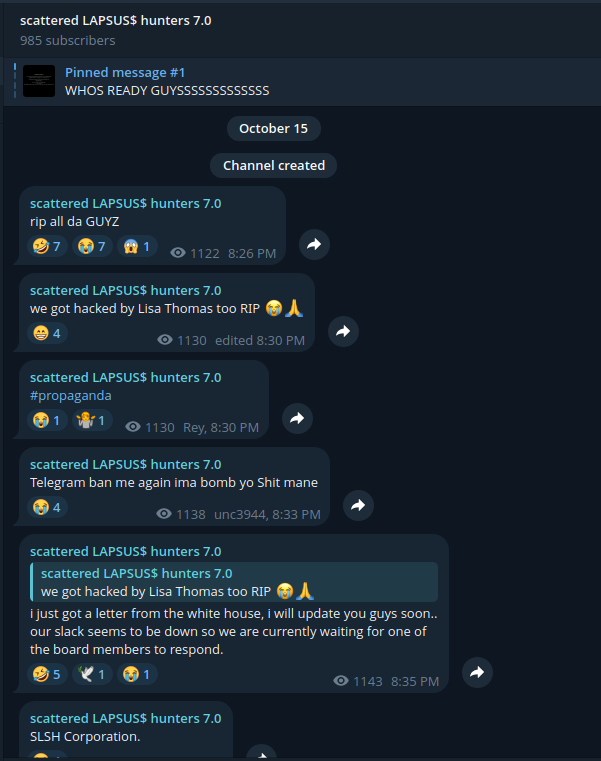
A new Telegram group makes fun of the whole situation.
The significant volume of data released from Qantas and Vietnam Airlines, coupled with the group’s ongoing threats against 39 other listed companies, suggests that this could indeed be just the beginning. The impact on customer trust, brand reputation, and regulatory penalties for these organizations could be substantial.
This incident highlights two critical realities
The third-party exposure trap
Your security perimeter is no longer just your firewall; it encompasses where your data resides and who has access. The compromise of Qantas and Vietnam Airlines data stemmed from weaknesses in their trusted third-party SaaS platform, Salesforce. A security lapse anywhere in your digital ecosystem can become your organization’s liability.
The weaponization of identity
Threat actors are increasingly targeting individuals to bypass technical controls. The primary tactic of the Scattered LAPSUS$ Hunters is social engineering, exploiting employees to gain access and potentially leading to significant data leaks.
Protect your business going forward
Outpost24 is committed to providing the visibility needed for proactive resilience. We believe that the future needs a more proactive, intelligence-led approach. We need to shift from reactive measures to proactive resilience. The ability to continuously identify, prioritize and limit your exposures fast, before incidents escalate.
Our CompassDRP solution offers crucial dark web intelligence to spot threats early. you can monitor your known (and unknown!) public-facing internal assets, as well as threats from external channels across the open, deep, and dark web. Once identified, these threats are prioritized and ready for remediation.
Is your organization’s email domain linked to compromised credentials? Let’s find out. Powered with threat intelligence used by CompassDRP, this free look-up delivers actionable intelligence via email. All we need is your corporate email address and we’ll be in touch with your results. Get your free results now.


