30 May 2023
Digital resiliency is one of the financial sector’s most significant challenges today. Resiliency refers to an organization’s ability to detect,...
09 May 2023
KrakenLabs has developed a new naming convention that uses poisonous plants to represent the origin and criminal activities of threat...
27 Apr 2023
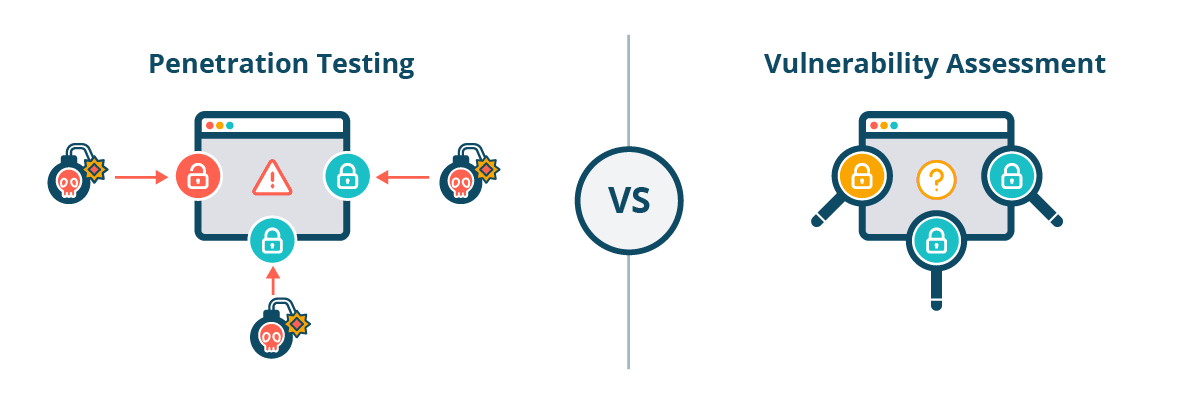
Vulnerability scanning and penetration testing should be an essential part of your cybersecurity strategy. This blog discusses the above methods...
24 Apr 2023
Outpost24, a leading innovator in cyber risk management, today announced it has appointed Brendan Hogan as Chief Strategy Officer (CSO)....
14 Apr 2023
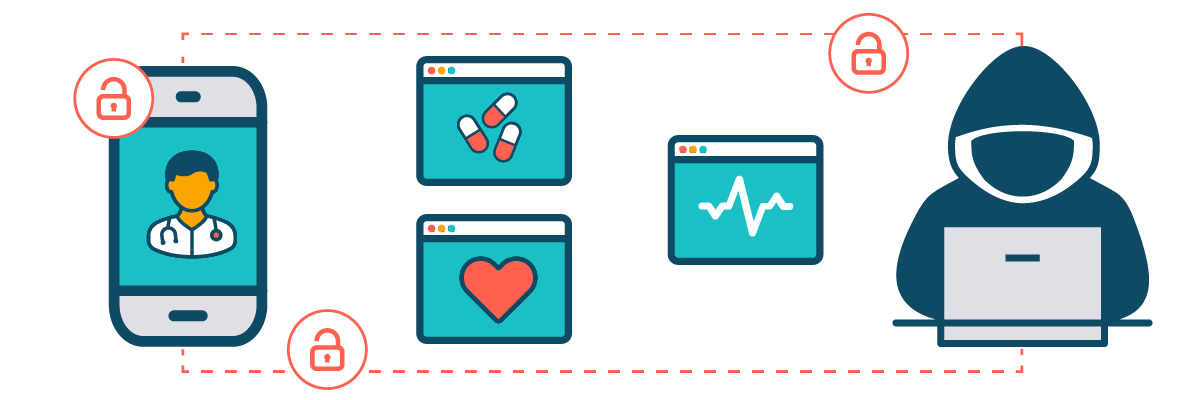
The HIPAA Security Rule requires healthcare organizations to perform regular security risk assessments to protect e-PHI. Penetration testing can help...