Lionishackers: Analyzing a corporate database seller
Outpost24’s threat intelligence researchers have been analyzing a corporate database seller known as “Lionishackers”. They’re a financially motivated threat actor focused on exfiltrating and selling corporate databases. This post explores how they operate, where their attacks are taking place, and the current level of threat they pose.
Lionishackers: Key things to know
- Even though they seem to have an opportunistic approach when choosing their targets, there seems to be certain preference for victims located in Asian countries.
- They have shown a high level of collaboration with the “Hunt3r Kill3rs” group and extensive participation in relevant underground community’s Telegram channels.
- Based on conversations maintained in Telegram channels, the threat actor has made statements suggesting they might profess the Muslim religion, which has led them to participate, to a lesser extent, in attacks of a hacktivist nature like coordinated Distributed Denial-of-Service (DDoS) attacks against Ukrainian and Israeli targets. Therefore, they could also have a certain secondary ideological motivation.
- Furthermore, they also worked on and offered other services such as pen testing, the commercialization of the Ghost botnet, and the launch of a forum project dubbed Stressed Forums.
- The group negotiates exclusively through Telegram but advertises its databases through multiple accounts on various underground forums.
- They have been creating accounts on multiple forums since at least September 2024, almost always using different aliases.
- There have been isolated accusations of scams by other users on Telegram channels and have had some of their underground forum accounts banned. However, they always publish information accompanied by images or links that show evidence of the compromises.
The threat of corporate database exfiltration
The unauthorized disclosure of sensitive information is, unfortunately, a common threat facing businesses today. While it has always been a menace, the exfiltration of corporate databases has become one of the most preferred activities for threat actors in recent years. Certain factors may have driven this preference:
- The volume of data that companies must manage has continued to grow, sometimes at a rate exceeding their capacity to manage it. This has resulted in storage methods that may not be the most appropriate or secure, or the need for third-party software for its management.
- This increase in the volume of data managed has forced the emergence of control measures at the regulatory level. These methods include the imposition of high financial penalties, something that has not escaped the attention of threat actors.
- Greater simplicity in attacks, which still involve initial access, some reconnaissance, and exfiltration of information, but do not necessarily require the use of malicious software to compromise devices and networks or encrypt the data.
- Finally, the profitability that these activities have brought to some threat actors has prompted others to join this line of work. Selling corporate databases has always existed, but the adoption of the double extortion among ransomware groups has popularized this practice, in part due to the media coverage it has generated.
How are threat actors exploiting corporate databases?
Even though most of the coverage of database leaks in the specialized media relates to ransomware groups following the double extortion method, we cannot forget those who have been around for a long time: underground forum users. There is a large community of threat actors who compromise companies and do not extort but simply sell or publish the extracted data for free to anyone who wants it. These actors are often financially motivated and leverage underground forums to promote their services.
More recently, they have also been using other platforms like Telegram for this purpose. Even in cases where threat actors publish databases for free, we can infer a financial motive, as they seek to gain a reputation in these forums that will later facilitate the sale of other databases at a higher price. Since the platforms where these types of sales or publications take place are not of common use, those who access the information are usually individuals with malicious intent. Therefore, the risk associated with these publications arose.
In addition to financial motivation, these threat actors focused on leaking databases often share other characteristics, such as acting individually rather than as part of a group. Despite acting alone, they sometimes pretend to belong to larger groups or collaborate with other forum members they know by participating in their threads. A simple financial motive is often linked to opportunistic targeting. However, due to their limited capacities, both in sophistication and resources, these actors appear to focus on compromising companies from specific regions.
Knowing and monitoring users specialized in these types of activities is vital to understanding this clandestine cybercrime, sometimes mistakenly considered low-level, which, despite its seemingly minor impact, can lead to significant financial losses. One user who has gained visibility and recognition since their emergence in September 2024 is “lionishackers”.
Lionishackers attacks and services
Lionishackers compromises their victims with the purpose of exfiltrating their information and later putting it up for sale. They do not seem to be extorting the affected companies before putting their data for sale, and neither do they seem to have a proprietary Data Leak Site (DLS) like other groups do. They solely rely on Telegram and underground forums to publicize their sales and complete the transaction with potential buyers.
SQL attacks and database exfiltration
To compromise their victims and exfiltrate information, it is most likely that the group is carrying out SQL injection attacks. They have been observed mentioning SQL injection attacks and their preference in the use of automation tools like SQL Map in some Telegram channels.
Furthermore, the group has also been observed selling databases with credentials from social media platforms or email services, indicating a broader targeting scope beyond corporate infrastructure. Therefore, although not confirmed, we cannot rule out the possibility that they would also be simply using valid credentials to gain initial access.
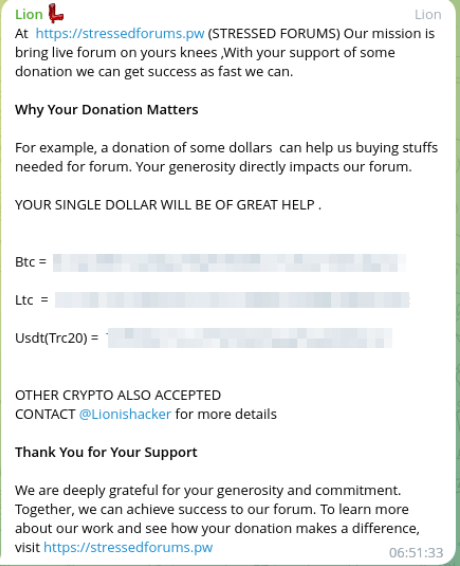
Stressed Forums and other services
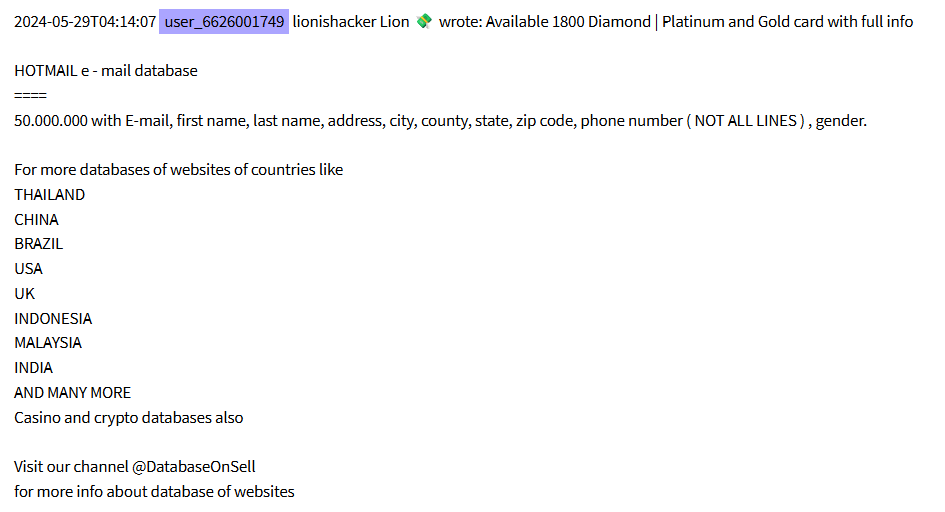
In addition to exfiltrating companies or organizations databases, Lionishackers has also been involved in selling social media platforms or email services databases. In July 2024, they advertised in Telegram the commercialization of a botnet dubbed “Ghost”, supporting attacks against layers 4 and 7.
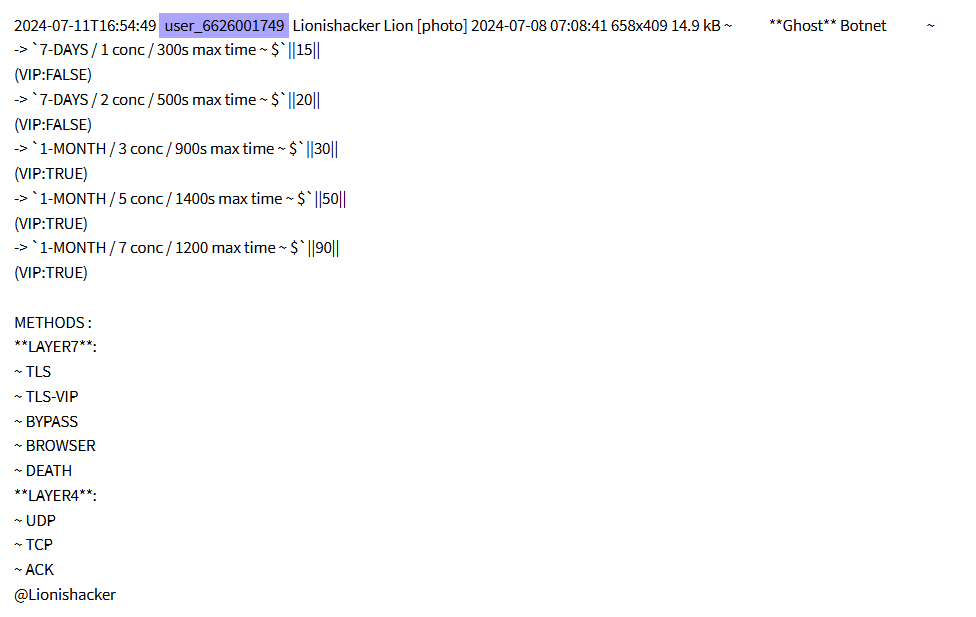
One month later, in August 2024, the group announced a forum dubbed Stressed Forums. This project, which would have been active since at least April, was promoted in Telegram with messages asking for donations to buy “stuff needed for the forum”. It was launched during a period when other major forums like Breach Forums were being seized by law enforcement authorities, so it’s likely that it attracted some users while it lasted. It did not get much attention from the press or the underground community in general and, at the time of writing, it is not available.
Who are they targeting?
Regarding their preferences, the group has stated on several occasions that they are most likely to attack gambling sites. Despite these claims, their victims are also from other sectors, including industries such as government, pharmaceutical, telecommunications, education, and retail.
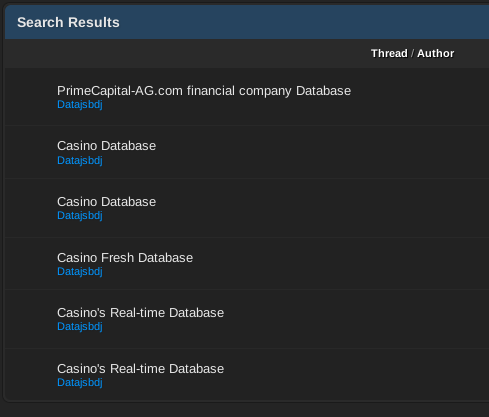
As for the regions, they have been observed leaking databases or showing interest in very diverse ones such as Thailand, Syria, and India, among many others. Despite this likely opportunistic approach, there does appear to be some focus on Asian countries.
Relationship with “Hunt3r Kill3rs”
“Hunt3r Kill3rs” is a politically motivated threat group spotted in April 2024. They owned a Telegram channel where they published their alleged victims and spread their narrative both in the Russian and English language. They have joined common fights supporting pro-Palestine threat actors and showing pro-Russian sympathies. At the time of writing, their Telegram channel had been closed.
In November 2024, Lionishackers were identified by another user as one of the admins of the Hunt3r Kill3rs Telegram channel.
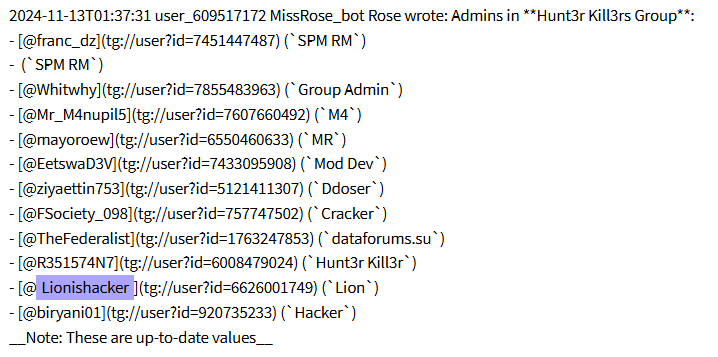
Being an admin in the channel proves the participation of Lionishackers in this group. Furthermore, they frequently used the channel to advertise their own databases for sale and has collaborated with the group in launching Distributed Denial-of-Service (DDoS) attacks against Ukrainian and Israeli targets.
Lionishackers commercialization and communication
Lionishackers have an extensive presence in both underground forums and Telegram. They rely on forums to publicize their data leaks and services but do not interact with potential buyers through this route. Instead, they include their Telegram contact details in the posts and move the conversation there.
Underground forums
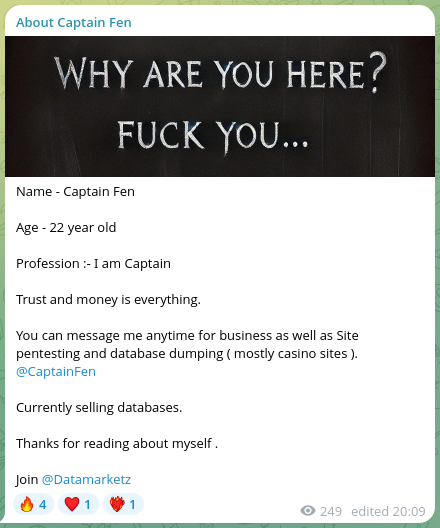
In September 2024, some months after their appearance and after having been active in Telegram for some months, the group began creating accounts in different underground forums with a peculiar approach.
Rather than consolidating their presence under a consistent alias across forums, Lionishackers has created multiple one-off accounts under distinct pseudonyms. Having this number of accounts, most of them have only one thread posted or have even been banned. This erratic behavior is not the usual way to proceed and could be an effort to evade attribution.
The common characteristic that has allowed us to attribute all these accounts to the group is that all of them would be sharing the same Telegram’s contact details in the posts.
| Forum | Username | Registration date |
|---|---|---|
| Breached | CypherX691 | – |
| BreachForums | ComplexData11 | – |
| CypherX691 | – | |
| crackingx | Hacker82828 | September 3, 2024 |
| Sussyba17 | September 23, 2024 | |
| Crackia | Sectornull101 | September 19, 2024 |
| Matadempo11 | September 24, 2024 | |
| Leakzone | Fen888 | April 2025 |
| Sinister | datwkuvnj | June 21, 2025 |
| DarkForums | Datcomon23 | September 22, 2024 |
| Sudsyba17 | September 23, 2024 | |
| Datajsbdj | October 31, 2024 | |
| Datahellosui | November 18, 2024 | |
| PremiumDataOnly | May 7, 2025 (Banned) | |
| Captainfen | May 27, 2025 (Banned) | |
| OfficialSalesMan | June 2025 (Banned) | |
| foreman | June 21, 2025 | |
| Datasellonly | July 5, 2025 |
Telegram
Even though they have been creating accounts in forums, the main communication channel for the group is Telegram.
They have extensively participated in popular Telegram group chats related to the underground community such as AKULA or B F R e p o V 3 C h a t, where they seem to be a known user. Furthermore, as mentioned before, they were active participants in Hunt3r Kill3rs’ Telegram channel.
Besides, the group managed their own accounts and channels for promoting the sale of their databases and their services. They have created accounts around their two main used aliases: Lion and CaptainFen.
Their oldest account (t[.]me/Lionishacker) and channel (t[.]me/DatabaseOnSell) are no longer available, likely due to Telegram’s restriction policies, but the group has managed to create new accounts and has kept on putting their newer data leaks for sale.
| Alias | Accounts | Channels | |
|---|---|---|---|
| LION | t[.]me/Lionishacker (Not available) | t[.]me/AboutTheLion | Created on January 16 |
| t[.]me/Lionishackers | t[.]me/DataMarketZ | Created on April 1 | |
| t[.]me/Lionishackerrr | t[.]me/YourwaytoLion | Created on July 5 | |
| t[.]me/DatabaseOnSell | Not available | ||
| CAPTAIN FEN | t[.]me/CaptainFen | t[.]me/AboutCaptainFen | Created on March 7 |
| t[.]me/CaptainFenGroup | Not available | ||
What’s the real risk associated with these threat actors?
As previously mentioned, the type of audience for whom the publications in underground forums and Telegram channels are intended consists of users with malicious intent, including those who may leverage the data for credential reuse, fraud, or corporate espionage. This means they would either download or buy databases to leverage them and carry out additional malicious activities. One could think, for example, of individuals:
- gaining access to the compromised companies for additional malicious activities;
- selling sensitive data to competitors to give them a greater commercial advantage;
- leveraging leaked Personal Identifiable Information (PII) for building sophisticated social engineering attacks;
- or simply leveraging included financial information such as credit card details or bank accounts.
Regardless of ultimate use of the leaked data and the resulting financial consequences, the additional effects faced by the affected companies involve significant reputational damage, especially when the publication in underground forums is covered in specialized media or social media platforms and news of the compromise reaches a wider audience.
Stay ahead of emerging threats
Outpost24’s CompassDRP solution combines the asset discovery powers of our EASM platform with threat-intelligence powered DRP modules. Customers are backed up by our world-class human-led threat intelligence team, KrakenLabs. Get in touch to learn more.