Analyzing the Gonjeshke Darande attack on Iranian crypto exchange Nobitex
The cyberattack by Gonjeshke Darande on Nobitex (Iran’s largest cryptocurrency exchange) made global headlines, not only for its scale, but for its political intent. This bold act of digital sabotage occurred within a rapidly deteriorating geopolitical context. On June 13, 2025, Israeli airstrikes targeted key Iranian military and nuclear facilities. Iran responded with swift retaliation, escalating tensions across the region.
In this environment, the Nobitex hack stands out not just as a significant cyber incident, but as a symbolic strike, designed to undermine Iran’s financial stability, expose alleged regime corruption, and deliver a political message in the language of cyberwarfare. We’ll walk through how the attack happened and the lessons we can learn.
How did the Nobitex attack play out?
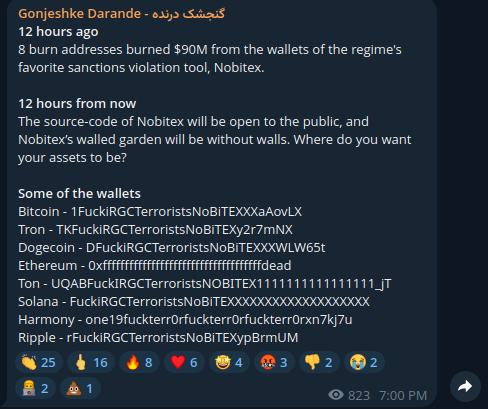
On June 18, 2025, Gonjeshke Darande, a suspected Israeli nation-state threat actor posing as an Iranian opposition hacktivist group, infiltrated the Iranian crypto exchange Nobitex and burned US$90M in different cryptocurrencies. The threat actor decided to burn the money by sending it to invalid cryptocurrency wallets, instead of profiting from it with a financial goal.
We can hypothesize that the attackers wanted to give a clear political and ideological statement, and at the same, destabilize the Iranian leadership and financial sector.
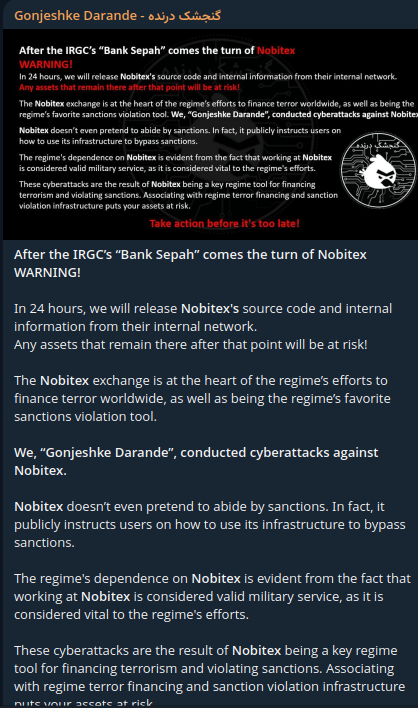
The emptied funds were transferred to invalid wallets containing the string “FuckiRGCTerroristsNoBiTE”, where they accuse the Islamic Revolutionary Guard Corps (IRGC) (part of the Iranian Armed Forces) of being terrorists. In their public statement announcing the attack, Gonjeshke Darande called Nobitex a “key regime tool for financing terrorism and violating sanctions”, accusing the Iranian government of using the cryptocurrency exchange as a means to evade the economic sanctions to trade and commerce with Iran that have been imposed by many countries.
How did Gonjeshke Darande access the funds?
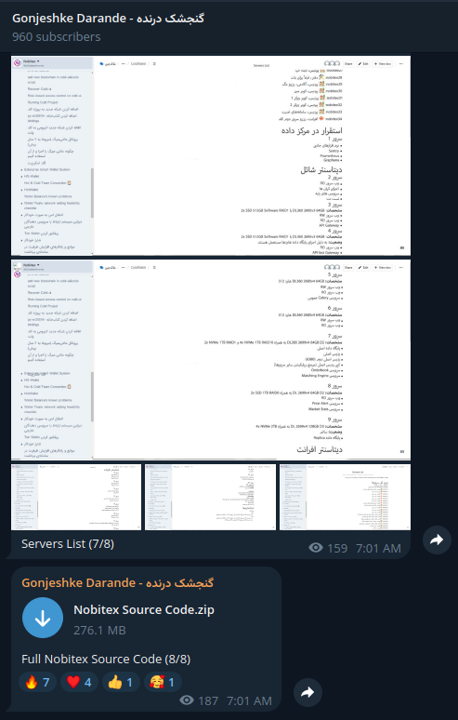
Gonjeshke Darande had presumably obtained a high-privilege access into the internal systems of Nobitex well in advance of the operation but was preparing for a relevant geopolitical event to maximize impact, effectively conduct the last stage attack, and empty the funds. That is evidenced by the fact that Gonjeshke Darande also uploaded the full source code of Nobitex to their Telegram, making it accessible to any interested third-party and incentivizing use with malicious intent.
The zip allegedly contains data about deployment configurations, internal privacy mechanisms, and scripts related to the management of cold wallet systems. By leaking this data, Gonjeshke Darande appears to be aiming for broader reputational and operational damage beyond the financial loss alone.
More evidence is needed to know exactly how the attackers accessed the crypto exchange funds, but it is very likely that they had access to internal documentation that detailed the inner workings of the exchange and possibly even authentication credentials to access the funds. Another hypothesis would be that a member of the organization infiltrated as an employee, or collaboration with insiders. At the time of writing, these are speculations based on our experience in the field of threat intelligence.
Response from Nobitex
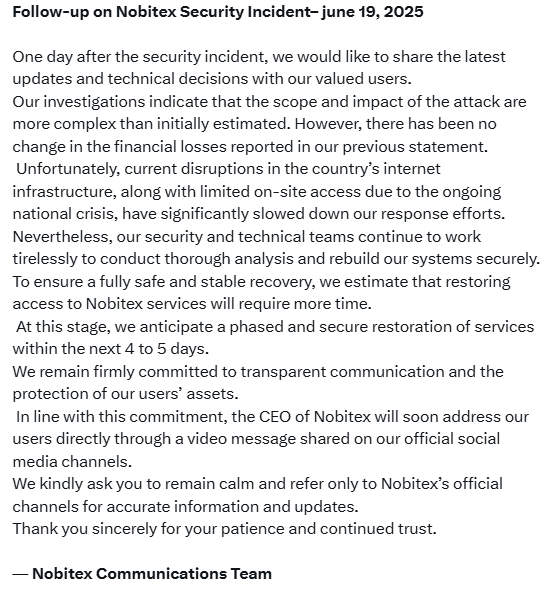
In response to the June 18, 2025 cyberattack, Nobitex confirmed unauthorized access to parts of its internal infrastructure, including its hot wallet, prompting the immediate suspension of its services and network isolation of affected servers. The exchange assured users that cold wallet assets remain secure and that losses were limited to the compromised hot wallet.
While internal investigations point to a critical failure in access controls, Nobitex has not disclosed specific details of the breach. Restoration efforts are underway but have been slowed by nationwide internet disruptions, with a phased recovery expected within four to five days.
Who is Gonjeshke Darande?
Gonjeshke Darande, also known as Predatory Sparrow, Indra, MeteorExpress, or Adalat Ali, is a cyber threat actor widely believed to be a front for Israeli state-sponsored operations. Although it publicly presents itself as an Iranian opposition hacktivist group, its technical sophistication, operational precision, and strategic targeting strongly suggest backing from a professional intelligence service.
The group has been active since at least 2019 and typically operates in cycles aligned with geopolitical tensions, particularly those involving Iran’s actions across the Middle East. Its stated goal is to retaliate against Iran’s Quds Force and affiliated proxies, claiming to act on behalf of the Iranian people.
Rather than focusing solely on disruption or financial damage, Gonjeshke Darande designs its operations to send bold and symbolic messages. The group has taken credit for high-impact attacks on Iranian critical infrastructure, including the 2021 railway system disruption using the Meteor wiper, gas station sabotage in 2021 and 2023, and the 2022 Khouzestan steel mill fire, which endangered lives by forcing molten steel to spill uncontrollably. In each case, the group left visible messages blaming the Iranian government and warning of continued retaliation. Their campaigns blend technical precision with psychological impact, often targeting national pride or public trust in institutions.
Despite their claims of protecting civilians, some of their actions (such as the steel plant sabotage) have drawn criticism for potentially endangering human lives. Nonetheless, the group remains one of the most controversial and technically advanced cyber actors in the region, walking a fine line between hacktivism and covert cyber warfare.
Why is Gonjeshke Darande targeting Iran’s financial industry?
Since the escalation of hostilities between Israel and Iran around June 13th, Gonjeshke Darande has seemingly intensified its focus on Iran’s financial institutions, with two major confirmed attacks impacting Iran’s Bank Sepah and the Nobitex crypto exchange.
Both attacks have impacted entities that, according to the threat actor, have been used by the IRGC to evade international sanctions and finance the “regime’s terrorist proxies, its ballistic missile program and its military nuclear program.”
They claimed to have destroyed critical data belonging to Bank Sepah, a bank linked to Iran’s Islamic Revolutionary Guard Corps (IRGC). In their statement, the group accused the institution of enabling the financing of Iran’s ballistic missile and nuclear programs, as well as funding terrorist proxies abroad, all while bypassing international sanctions.
Gonjeshke Darande framed the attack as part of a broader campaign against regime-affiliated institutions, thanking unnamed Iranian insiders who allegedly assisted in the operation.
What can we learn from the Nobitex attack?
The attack on Nobitex by Gonjeshke Darande marks a pivotal moment in cyber-enabled geopolitical confrontation. This was not a financially motivated heist but a strategic, ideological, and psychological operation. By destroying rather than exfiltrating funds, the threat actor emphasized its goals: dismantling public trust in regime-linked institutions and signalling its technical superiority.
Several key conclusions emerge:
- Cyber operations are now central to geopolitical influence, capable of inflicting substantial economic and reputational damage without conventional warfare.
- Cryptocurrency infrastructure is a new frontline; its perceived neutrality is vulnerable to targeted attacks aimed at state-sponsored misuse.
- Insider threats and long-term access are a growing concern for high-value financial platforms, particularly in authoritarian regimes where dissidence can serve as a recruitment vector for foreign intelligence services.
If proven to be the work of Israeli state-affiliated actors, this attack would represent an escalation in covert cyberwarfare, utilizing digital assets not only for disruption but as narrative weapons in the broader Middle East conflict.
Given the group’s established pattern of operating in cycles tied to geopolitical tensions, and the current escalation between Iran and Israel, it is highly likely that additional attacks will follow in the coming days or weeks. Financial institutions, especially those linked to state operations, IRGC entities, or sanctions evasion, remain prime targets.
This trend reflects an emerging strategy: to apply sustained pressure on the financial pillars of the regime by combining cyber disruption, data destruction, and public exposure to erode confidence domestically and undermine international trust in Iran’s digital financial infrastructure.
Stay ahead of emerging threats
Outpost24’s CompassDRP solution combines the asset discovery powers of our EASM platform with threat-intelligence powered DRP modules. Customers are backed up by our world-class human-led threat intelligence team, KrakenLabs. Get in touch to learn more.
