Five key takeaways from Outpost24’s Cyber Resilience Day
True to its theme ‘Cyber Resilience’, our recent cyber security gathering was able to dissect the fast-moving threat landscape with insights and information nuggets from a panel of security experts and practitioners on the shortcomings and the need for better use of threat intelligence.
Here are five takeaways from the Cyber Resilience Day in Breda co-hosted with our customer CM.com and a panel of cybersecurity experts:
- Victor Acin, Head of Threat Intel Research, Outpost24
- Lennart Branderhorst, Threat Intel Lead, DNB
- Francisco Dominguez, Research & Innovation, Hunt & Hackett
- Sandor Incze, CISO, CM.com
Traffers are taking credential theft to a new level
Stolen credentials are still the primary method of cyber-attacks, but the increased professionalization of cyber-criminal groups, specifically the rise of traffers, has introduced a new dynamic in the Credential Theft Ecosystem.
Traffers are highly organized cybercriminal groups. They spread different types of malware families with goal of exfiltrating credentials for profit. Their industry-like structure includes a complex chain of product and service providers, to spread the malware as far and wide as possible, and the management of the dedicated space for the sale of stolen credentials.
Outpost24’s KrakenLabs has been closely monitoring several traffers groups, gathering information from forums, and Telegram channels, as well as obtaining and analyzing malware samples from different sources. We will continue to monitor these groups as part of our cyber threat intelligence solution, helping organizations improve their cyber security posture with real-time threat detection and faster remediation.
Find out more about Cybersecurity trends from the dark web – the rising threats of Traffers by Victor
Most companies haven’t figured out how to use threat intelligence
While threat intelligence is no longer a buzzword, there is still no common standard for leveraging real-time threat intelligence effectively. Most companies are swarmed with data, and struggle to derive actionable insights. It’s a hard job, and without the right processes and tools, there’s no return on investment. Before you go ahead and buy a shiny cyber threat intelligence solution, do ask yourself:
- What are my business requirements and use case for using threat intelligence?
- How will I measure the impact of threat intelligence on my security posture?
- What is my business’s security maturity and what type of threat information do I need?
- Do I have the right process and talent to handle the threat data?
- Am I aware of the limitations of threat intelligence and what it can do for me?
The bottomline is you need to think carefully about the value of threat intelligence and what it can do for your organization. Many solution is not an as-a-service solution, and actually require you to develop in-house competencies. And if you do need to outsource that expertise, make sure you go with a vendor with managed services experience or a MSSP that can deliver what your organization needs. Check out Francisco’s talk.
DORA, NIS2 and TIBER will become the new standard for cyber resilience in Europe
There is growing pressure around cybersecurity and data privacy for regulated industries. Not to mention the new Digital Operational Resilience Act (DORA), and Network and Information Security (NIS 2) Directive that are coming into effect by the end of 2024, in addition to the framework for Threat Intelligence-based Ethical Red Teaming (TIBER). During the group discussion, many participants expressed their concern around the complexity and implication in terms of budget and resourcing to comply with these new standards. The best way to move forward is to understand what the new regulatory standards entail, and prepare your organization step-by-step.
- Make sure your organization’s cyber hygiene is in order through:
- Regular or continuous vulnerability assessment
- Ensure access control
- Limit privilege access
- Keep systems and software up-to-date
- Monitor, analyse, and audit logs
- Enforce strong passwords
- Practise proactive risk management
- Start with Advanced Red Teaming (ART) exercises. TIBER will become a standard not only in the financial and insurance sector, but regulated industries like healthcare and government, eventually. ART is a lighter version of TIBER that will enable organizations to do next-level testing of their protections, procedures, and responses before easing into the more stringent TIBER
- Identify your vital suppliers and discuss their security policies. From the SolarWind, to Kaseya, and Mimecast attacks, it’s more important than ever to protect the supply chain and ensure the companies you’re working with are as committed to cybersecurity as you are.
But how does it work in real-life? In the financial sector, TIBER testing is already being performed at varying degrees. Lennart from the pioneering TIBER-NL program, coordinated by the Cyber Unit of De NederlandscheBank (DNB), shares his first-hand experience about the challenges of TIBER testing: it can be rather difficult to make Threat Intelligence actionable during the testing, and with recurring tests the threat data can become repetitive, leading to lengthy reports that makes it even harder to make meaningful conclusions. It’s a emerging standard that still needs to be refined.
More on “The Good, Bad and Ugly of TIBER Testing” from Lennart
Buying more security tools won’t make your organization more secure
Companies have access to more security tools than ever, but it doesn’t make them safer. Sandor, CISO of CM.com shares that companies often get too caught up in shiny new tech and forget about the fundamentals. He provides a glimpse into the key building blocks of the public company’s cybersecurity program.
- Get the basics right: Basic security hygiene still protects against 98% of attacks. CM.com takes their security hygiene seriously and use different security testing tools and methods to continuously identify risks and tighten their security posture.
- Proactive threat monitoring: As a public listed company and a key technology partner for the Formula 1 Grand Prix in the Netherlands, the risk of cyber-attack has never been higher. In addition to cyber hygiene best practices, CM.com also leverage threat intelligence to proactively monitor external threats such as advanced persistent threats, unwanted mentions in the dark web forum, and potential malware infections that could pose a risk to their business.
More from Sandor against 98% of attacks.
Build your security program around your maturity
To conclude, there’s no silver bullet in cybersecurity, and one size doesn’t fit all. Organizations need to look at their current maturity and determine how they can blend threat intelligence into their security testing program.
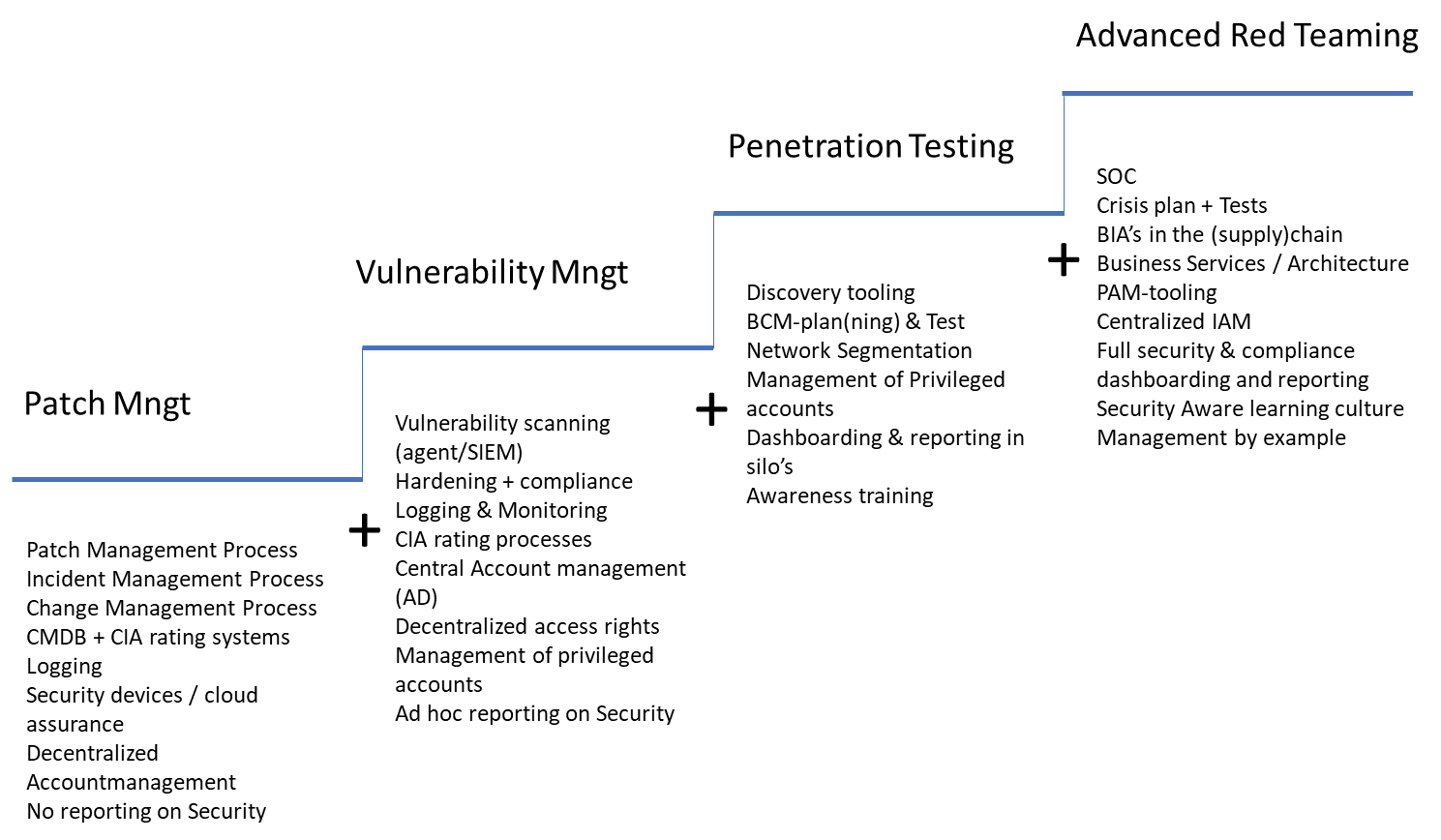
Important steps to grow the maturity level are:
- Get a good overview of technology stack and digital assets
- Define security policies and procedures
- Make sure there is a good supply chain risk management process
- Determine your risk appetite and conduct business impact analysis
- Create user awareness programs
- Define the CISO role
- Get Management/Board buy in and agree on the KPI’s
- Business Continuity planning
- Crisis planning and testing
- On a technical level implementation of:
- CMDB and asset classification
- Back-up and recovery systems
- Network segmentation
- Identity Access Management
- Patch and Vulnerability management
- Logging and monitoring
- Using discovery tooling to determine Attack surface
- Continuous Penetration testing
- A (managed) SOC service
Financial services, healthcare, retail, and government continue to be most vulnerable for cyberattacks. The above security testing maturity model provide a blueprint to access their current maturity and where they can go as they mature to prevent detrimental incidents that could compromise your security and business operations overall.
As a expert in cybersecurity testing and risk management, Outpost24 offers a range of automated and manual security testing solutions for proactive risk assessment and compliance testing. Talk to us about your pentesting needs and Red Team assessment scope today to improve your security maturity.