New attack analysis: What you need to know about the Endesa data breach
Following the recent cyberattack on Endesa, one of Spain’s largest electricity and gas providers, Outpost24’s threat intelligence team has compiled a comprehensive analysis of the incident based on publicly available evidence from underground forums, leaked dataset listings, and the threat actor’s own statements. The analysis examines the likely initial access vector, the probable origin of the data, and the broader security implications associated with compromised credentials and privileged access.
What we know about the Endesa data breach
In early January 2026, a threat actor began advertising the sale of a database allegedly belonging to Endesa. According to the seller, who uses the aliases “glock” and “spain”, the database contains personal and financial information relating to more than 20 million individuals and offered it for sale on underground forums specializing in database trading.
On January 11, 2026, Endesa confirmed in a statement that it had detected evidence of unauthorized and illegitimate access to certain personal data of customers related to their energy contracts. The company stated that password data was not compromised and that, at the time of disclosure, there was no evidence of the exposed data being used fraudulently. Endesa did, however, urge impacted customers to remain vigilant against potential phishing or spam campaigns.
Endesa reported that the attackers accessed and likely exfiltrated basic customer identification information, contact details, national identity numbers, contractual information, and payment details, including IBANs. To date, the company has not reported operational outages or system disruption beyond the unauthorized extraction of data.
Affected individuals have been notified, including customers of Endesa’s gas distributor, Energía XXI. At the time of this analysis, no threat actor has been formally attributed to the incident.
How the breach likely occurred
The analysis below reflects Outpost24’s threat intelligence team’s assessment of the most likely attack path, based on observed threat actor behavior, leaked datasets, and technical indicators consistent with credential-based access and backend data extraction.
- Initial access vector via compromised legitimate credentials: The threat actor’s own statements, specifically “I also do cracking as a service” and “Don’t blame me for my work; blame your employees for not doing theirs,” strongly suggest that initial access was obtained through compromised credentials. This would have enabled the attacker to perform lateral movement across internal systems with minimal resistance and potentially access privileged information directly.
- Data exfiltration without encryption or operational disruption: Although there are references to attempted negotiations and implied pressure tactics regarding the potential sale or disclosure of the data, there is no evidence of encryption, ransomware deployment, or destructive activity. All signs indicate this was a breach focused exclusively on exfiltration rather than disruption or extortion through encryption.
- Salesforce Customer Relationship Management (CRM) platform likely involved: Based on the files listed in the threat actor’s publications, it is possible that the data was exfiltrated using a Salesforce backend data extraction mechanism, most likely accessible via compromised employee or service credentials with elevated Application Programming Interfaces (API) and integration privileges. The inclusion of Change Event objects, Data Lake model tables, and enriched datasets indicates access beyond standard CRM usage, pointing to integration and analytics roles.
Threat actor behavior and analysis
Analysis of underground activity and observed behavior provides insight into the likely characteristics, intent, and capabilities of the individual behind the data sale.
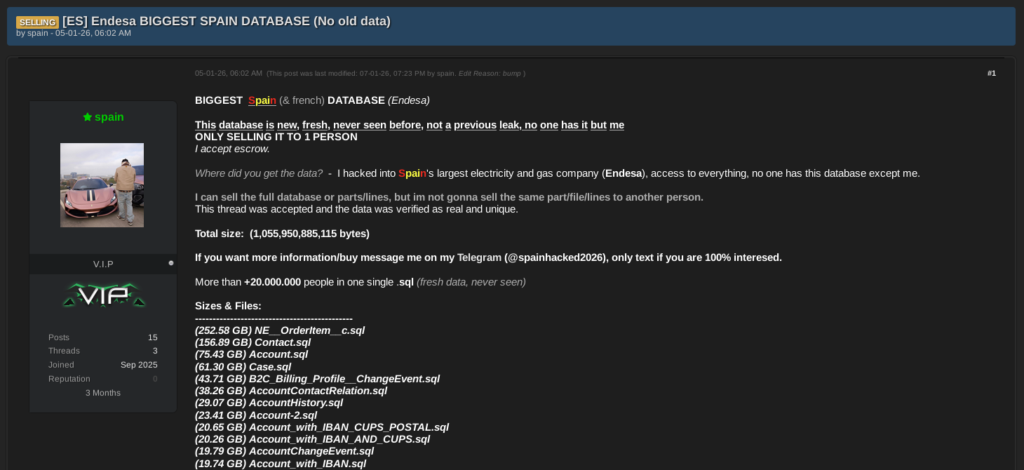
Original post from DarkForums on January 5, 2026 (fragment).
Threat actor profile: Several indicators suggest the activity is attributable to a lone, Spanish-speaking individual rather than a coordinated group. The threat actor’s footprint is limited, with activity confined to a small number of low-barrier forums focused on database trading. There are no signs of sustained operations, affiliate structures, or broader campaign activity. The scope and timing of the activity appear narrow, supporting the assessment that Endesa was targeted opportunistically rather than as part of a strategic or large-scale operation. These indicators point to a relatively low level of sophistication compared to established data-extortion or ransomware groups.
Underground activity and escalation behavior: Following the initial data sale advertisements, the threat actor escalated activity by issuing threats directed at Endesa after the company did not engage. In later publications, the actor warned that additional data would be released and attempted to apply public pressure after Endesa acknowledged the breach. Statements attributed to the actor include:
“If Endesa continues to not contact me, I will post more data. All of their customers are at risk because of them.”
“This isn’t about some customer energy contracts, it’s about the entire database.”
The timing of these messages suggests an attempt to increase leverage or attract buyer interest rather than evidence of a coordinated extortion campaign.
Credibility: The threat actor has not published a fixed price for the dataset and instead invited interested parties to make direct contact. Although early claims suggested the data would be sold exclusively to a single buyer, later posts offered either the full database or partial datasets. Despite repeated advertisements, there is no evidence of completed or verifiable sales, and as of January 7, 2026, the database was claimed to be unsold; its continued promotion on January 12 suggests it remains so.
The actor’s minimal presence across forums and messaging platforms, combined with a lack of established reputation, suggests limited credibility among potential buyers. Monetization efforts appear unsuccessful at the time of writing, likely due to a combination of high pricing expectations and low trust in the seller.
Communication channels: The actor’s activity has been observed across a small number of platforms.
- DarkForums: The actor joined DarkForums on September 17, 2025, initially using the nickname “glock.” When advertising the Endesa dataset, the account name was changed to “spain.” Earlier activity by the user on this forum indicates an interest in databases containing personal information related to Argentinian citizens and companies, including Grupo Hasar.
- BreachForums: Created on January 3, 2026, the account has no activity beyond Endesa-related posts.
- Telegram: A channel named @spainhacked2026 was created on January 3, 2026, has shown minimal engagement and contains a single post referencing the alleged data sale. The channel contains a single publication with a link to the username “@FedsWontCathMe” (aka “trx”). On January 5, this user joined the Telegram channel for “elhacker.NET”, a Spanish-speaking hacking community. Based on some of the publications still available from that same day, it is possible that the user promoted Endesa’s leak in there as well, with posts that were later deleted because they violated the channel’s rules.
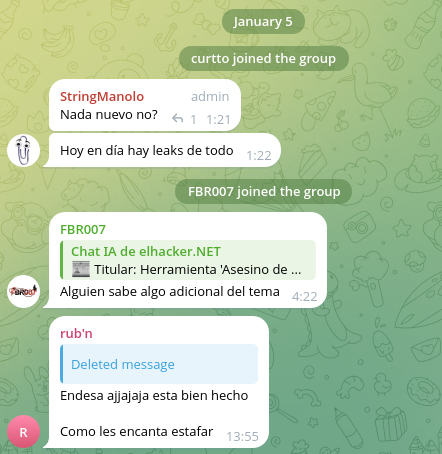
Comments on elhacker.net Telegram channel that could be related to a publication, now deleted, by the threat actor in relation to Endesa’s leaked database.
On both BreachForums and DarkForums the attacker provides a Session ID for potential buyers (05f0952d5f2da5465916215dcec379d08a9eb63eda4be4378d333e3e1f68292406), however, Outpost24 analysts have not been able to relate this ID with additional public activity.
Analysis of the leaked data
The files referenced in the threat actor’s publications provide technical context for the attack methods described above and offer insight into both the scope of the data exposure and the likely source environment. The structure, naming conventions, and size of the leaked files align with the data types disclosed by Endesa in communications to affected customers.
Leaked dataset characteristics: The threat actor referenced multiple large database exports, including the following representative files.
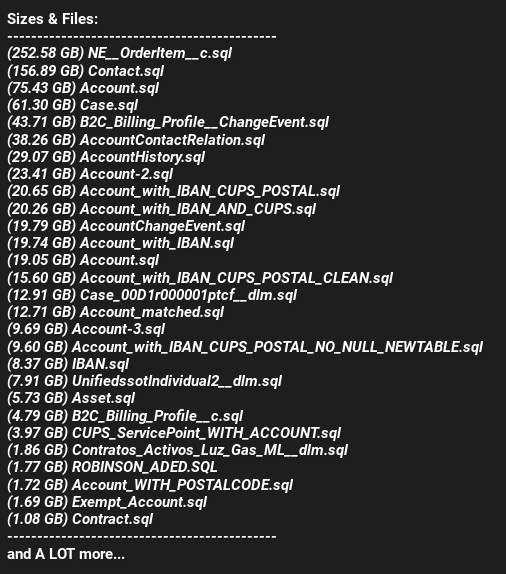
Selection of files included in the January 2026 Endesa data breach.
The full dataset referenced includes additional account, case, billing, and identity-related objects consistent with large-scale CRM data exports.
Platform indicators observed in the dataset: Analysis of file names, object types, and export characteristics indicates the data originated from a CRM environment consistent with Salesforce.
- Core CRM objects such as Account.sql and Contact.sql are consistent with standard Salesforce data models
- Custom objects and fields using __c and __dlm notation reflect Salesforce-specific schema extensions
- Change Data Capture and event streaming files, including AccountChangeEvent.sql and B2C_Billing_Profile__ChangeEvent.sql, are typically accessed via privileged APIs or backend integrations rather than user interfaces
- Objects ending in __dlm, strongly suggest Salesforce Data Cloud or data lake materialization layers, indicating backend analytics or integration access
- File sizes ranging from 20 GB to over 250 GB per object are indicative of full-table exports via bulk APIs, ETL pipelines, or data warehouse synchronization, rather than UI-based exports
- Post-processed and joined datasets, such as Account_with_IBAN.sql and Account_with_IBAN_CUPS_POSTAL_CLEAN.sql, suggest the use of an intermediate analytics or data processing environment
Combined, these files support the assessment that the data originated from a CRM environment with backend access sufficient to enable large-scale extraction, consistent with compromised credentials and elevated integration privileges.
Outpost24 recommendations
The Endesa incident highlights the value of early visibility into credential exposure. Organizations should prioritize continuous monitoring for leaked or misused credentials, including both user and service accounts associated with third-party platforms such as CRM systems, which are increasingly implicated in high-impact attack paths. Identifying leaked or traded credentials early enables rapid response actions such as forced password resets, token revocation, and account suspension before adversaries can operationalize access.
Credential exposure monitoring should be tightly integrated with identity and access management processes, particularly for accounts with elevated API, integration, or analytics privileges. When combined with detection of unusual login behavior, excessive data access, or atypical API usage, this approach can significantly reduce dwell time and limit the scale of data exfiltration.
Outpost24’s Digital Risk Protection provides continuous monitoring for leaked credentials, dark web activity, and exposed data. This intelligence enables security teams to identify emerging risks and respond quickly before access is abused. Outpost24 also offers a free Credential Checker so you can see whether your company’s email domain has appeared in leak repositories or underground marketplaces. Powered by intelligence from our CompassDRP solution, this free tool delivers actionable insights via email.
Let’s talk
If you’re interested in seeing how Outpost24 can help you assess potential credential or data exposure, contact us today.
