Understanding Cyber Threat Reconnaissance with MITRE’s PRE-ATT&CK Framework
Cyberattacks don’t begin with malware; they begin with intelligence. Before a single exploit is launched, threat actors conduct careful reconnaissance, mapping out their targets in detail. This often-overlooked phase of the attack lifecycle is where defenders have a unique opportunity to get ahead.
In this post, we’ll explore cyber threat reconnaissance through the lens of MITRE’s PRE-ATT&CK framework, a powerful model designed to understand the preparation tactics of adversaries.
The Cyber Kill Chain: Understanding the anatomy of an attack
Cybersecurity has evolved from amateur hacks and firewall evasion to a battleground of advanced persistent threats (APTs), nation-state actors, and highly organized cybercriminal groups. What was once the domain of hobbyists has become a professionalized, militarized field — and like any battlefield, understanding the enemy’s tactics is key.
It’s from this military analogy that the term ‘Cyber Kill Chain‘ comes in. Originally developed by Lockheed Martin, the Kill Chain breaks down the structure of a cyberattack into seven distinct stages. It offers a linear view of how attacks unfold, from initial reconnaissance to data exfiltration.
While variations of the Kill Chain exist — such as the SANS Institute’s interpretation pictured below — the core idea remains the same: by understanding each step, defenders can identify opportunities to detect, disrupt, or contain the threat before it causes damage.
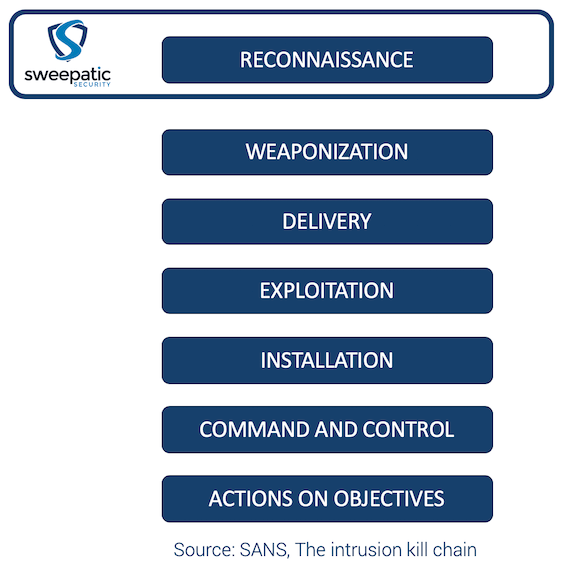
The 7 Stages of the Cyber Kill Chain
- Reconnaissance: Gathering intel on the target
- Weaponization: Crafting a malicious payload
- Delivery: Transmitting the payload to the victim
- Exploitation: Executing the attack on the target system
- Installation: Installing malware or establishing a backdoor
- Command and Control (C2): Establishing communication with the attacker
- Actions on Objectives: Completing the attacker’s goals (e.g., data theft, disruption)
Despite its influence, the Kill Chain has been criticized for its perimeter-focused, malware-centric approach, especially in the face of modern attacks that bypass traditional defenses. That’s why more dynamic and granular frameworks, such as MITRE ATT&CK and PRE-ATT&CK, have gained traction.
What is the MITRE ATT&CK framework?
As cyber threats have grown more complex, defenders need a clear picture of exactly how adversaries operate. That’s exactly what the MITRE ATT&CK framework provides.
Developed by MITRE, ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is an open-source framework that catalogs the known behaviors of threat actors based on real-world observations. It presents these behaviors in a tactics-to-techniques matrix, offering defenders a standardized way to map, detect, and respond to intrusions.
What makes ATT&CK so valuable?
- Granularity: ATT&CK breaks down attacker behavior into tactics (objectives) and techniques (how those objectives are achieved), helping organizations precisely describe and analyze threats.
- Threat Modeling: Security teams can model specific adversaries by overlaying known TTPs (Tactics, Techniques, and Procedures) onto the ATT&CK matrix.
- Defense Planning: Blue teams use the matrix to identify gaps in defenses and simulate realistic attack scenarios.
- Standardization: ATT&CK has become a global standard for communicating threat behavior across teams, tools, and organizations.
Whether you’re conducting threat hunting, red teaming, or incident response, the MITRE ATT&CK framework provides a shared language and toolkit for understanding adversaries and stopping them more effectively.
The PRE-ATT&CK framework
Most cyber defenses focus on detecting and blocking attacks after they’ve breached the perimeter. But what if you could disrupt attackers before they ever reach your network? That’s the goal of MITRE’s PRE-ATT&CK framework.
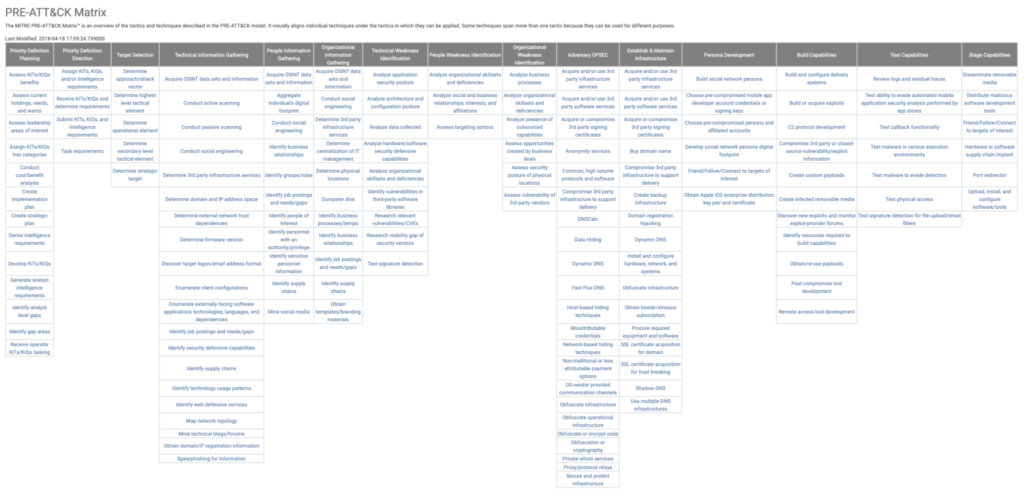
PRE-ATT&CK extends the ATT&CK model by focusing on the earliest stages of the attack lifecycle: the preparation and planning phases. It outlines the tactics and techniques used by adversaries as they gather intelligence, select targets, and build the infrastructure needed for an attack.
What is PRE-ATT&CK?
PRE-ATT&CK is a non-intrusive, intelligence-driven framework that maps how threat actors prepare for an operation, including:
- Target selection
- Reconnaissance
- Weakness identification
- Operational setup
- Capability development
Unlike ATT&CK, which deals with active compromises, PRE-ATT&CK covers pre-exploit activities that are often invisible to traditional security controls. These tactics can’t always be mitigated with firewalls or endpoint detection; instead, they require organizational awareness, training, and proactive monitoring.
PRE-ATT&CK bridges a critical gap in the cyber kill chain, helping organizations shift from reactive to proactive security. It provides valuable context for Threat Intelligence, red teaming, and attack surface management.
Understanding the threat
To effectively defend against cyber threats, organizations need to understand not just how attackers strike, but why and when they start preparing. The MITRE PRE‑ATT&CK framework breaks the preparation phase into five strategic categories, each representing a crucial stage in the attacker’s planning process.
1. Priority definition & target selection
Every attack begins with a goal. Adversaries assess their objectives — whether it’s data theft, disruption, or espionage — and define what success looks like.
During this phase, attackers identify target attributes (e.g. industry, tech stack, geography) that align with their mission. By recognizing the types of targets threat actors typically pursue, organizations can better assess their own threat profile and focus resources on likely attack vectors.
2. Information gathering
This phase involves collecting open-source and technical intelligence on the target organization. Threat actors explore:
- Employee identities via social media
- Public infrastructure data (e.g. DNS records, IP ranges)
- Technology stacks and known exposures
The goal is to build a complete attack surface map, often more comprehensive than what the target organization itself maintains.
3. Weakness identification
Armed with intelligence, attackers begin probing for vulnerabilities — both technical and human. This can include outdated software or misconfigurations, unpatched CVEs, or susceptibility to phishing or social engineering.
Techniques like vulnerability scanning, bait testing, or even psychological profiling are used to assess exploitable gaps.
4. Operation installation
Once viable entry points are found, attackers set up their offensive infrastructure. This may involve:
- Registering fake domains or lookalike websites (cybersquatting)
- Deploying malware staging servers
- Developing social engineering personas
- Practicing Operational Security (OPSEC) to avoid detection
OSINT monitoring can detect early signals, like suspicious domains or impersonation campaigns — enabling pre-attack intervention.
5. Capability development
Finally, attackers tailor their tools and techniques to the specific weaknesses of the target. This might include things like writing custom malware, simulating internal processes, and testing evasion techniques.
These capabilities are refined before the first exploit is ever launched, making early detection extremely challenging without threat intelligence and counterintelligence techniques.
Together, the five PRE-ATT&CK phases offer a blueprint for understanding and anticipating threats before they escalate. By aligning defenses to this early-stage activity, organizations can move from reactive to predictive security.
TIBER-EU: Turning Threat Intelligence into action
Understanding threats is just the first step — testing your defenses against them is where theory becomes practice. That’s the philosophy behind TIBER-EU (Threat Intelligence-Based Ethical Red Teaming), a European framework designed to help critical financial institutions conduct realistic, intelligence-led security assessments.
Unlike traditional penetration tests, which often follow a checklist of technical flaws, TIBER assessments are tailored to the actual tactics, techniques, and procedures (TTPs) of threat actors known to target a specific organization or sector.
What Is TIBER-EU?
Created by the European Central Bank (ECB), TIBER-EU provides a standardized way for banks, insurers, and other financial entities to test their resilience against advanced persistent threats (APTs).
It requires collaboration between two independent teams:
- A Threat Intelligence (TI) team that maps out realistic adversary behaviors
- A Red Team that emulates those behaviors in a controlled attack scenario
The goal is to simulate full attack paths, assess detection and response capabilities, and strengthen defenses under pressure.
Where PRE‑ATT&CK Fits In
PRE‑ATT&CK is a natural fit for TIBER-style assessments because it helps define the early-stage TTPs used by adversaries during reconnaissance and preparation — exactly the types of behaviors a TI team should consider when designing red team scenarios.
By mapping real-world threat actors using the PRE‑ATT&CK matrix, security teams can:
- Select realistic attacker profiles and goals
- Understand how adversaries gather intel and stage attacks
- Design red team exercises based on specific and actionable intelligence
For organizations already investing in External Attack Surface Management (EASM), PRE‑ATT&CK and TIBER provide a structured way to connect reconnaissance insights to active defense testing.
Turning reconnaissance awareness into resilience
Cyberattacks don’t start at the moment of compromise; they begin long before, during the quiet phase of reconnaissance. By leveraging frameworks like MITRE PRE-ATT&CK, organizations can shine a light on this early-stage activity, gaining critical visibility into how threat actors plan, prepare and position their attacks.
Outpost24’s EASM platform is built to operationalize the PRE‑ATT&CK framework. It continuously monitors your external footprint, identifies exposed assets and weak points, and maps your organization the same way an attacker would — all before the first intrusion attempt.
Don’t wait until the breach. See your organization through the eyes of an attacker and take control of your exposure before they do. Sign up for a free attack surface analysis today.



