The 2026 Cybersecurity Threat Landscape: Persistent Adversaries, Repeatable Playbooks
As a threat intelligence team, our job is to separate noise from persistence in the cybersecurity threat landscape. In this article, we assess the threats most likely to remain and evolve through 2026 based on the threat actors, campaigns, and malware we have tracked and researched during the last year.
Our work centers on tracking adversaries with a strong footprint in the underground ecosystem: forums, Telegram channels, data leak sites, and marketplaces where cybercriminals operate.
The threat actors that cause the most damage are the ones that use repeatable playbooks and affiliate ecosystems to recruit talent and monetize consistently. In 2026, security teams will need to counter quieter intrusions, faster exploitation cycles, and more living-off-the-land (LOTL) tools and techniques that blend into normal operations.
Ransomware groups will expand Ransomware-as-a-Service (RaaS) offerings
Ransomware will remain a default monetization path for profit-driven cybercrime because it offers a direct route to payment-based extortion. Even when ransoms are not paid, the same intrusions often support follow-on monetization through data theft and resale.
Specifically, the RaaS landscape has become very competitive, and these groups are progressively facilitating resources and offering better conditions to their affiliates. The most stable RaaS groups have substantial budgets to buy critical vulnerabilities, valuable initial accesses and work with proficient affiliates organized in hierarchical team-based structures.
Alongside the constant technical evolution, these sophisticated ransomware groups also innovate in the extortion methods applied to pressure victims. For instance, the Anubis RaaS allegedly provides the affiliates 24/7 support, including legal support for negotiations and direct outreach to victims, regulators, and media.
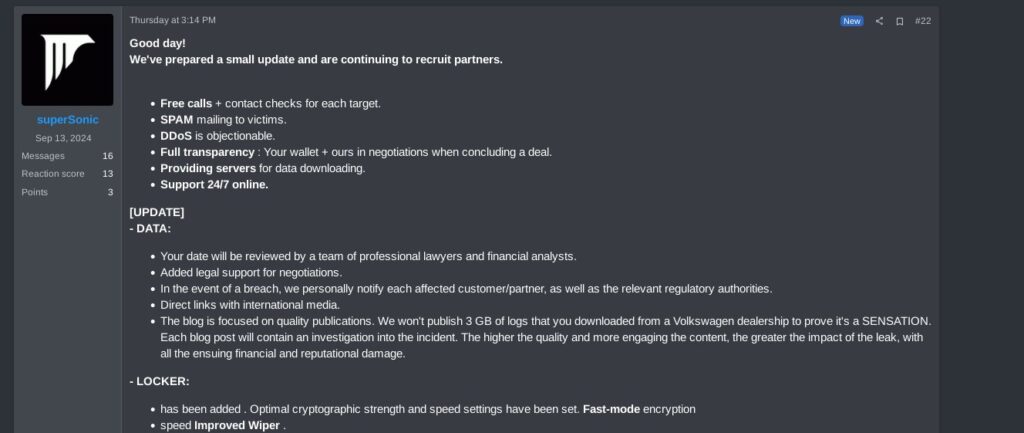
The representative of the Anubis RaaS announcing they are recruiting partners.
Further highlighting the evolution in these extortion methods is the CL0P-linked extortion activity targeting Oracle E-Business Suite (EBS), associated with CVE-2025-61882. This issue is remotely exploitable and described by Oracle as potentially enabling remote code execution without authentication. Reporting on the campaign describes extortion-first behaviour and TTP alignment with CL0P’s previous data-theft-driven campaigns.
The ransomware tactics to watch out for in 2026
- Supply-chain attacks: More ransomware intrusions will originate from the supply chain, targeting assets like file-sharing platforms, customer-support platforms, enterprise resource planning systems, and identity management cloud platforms. That approach allows attackers to monetize across a broad victim pool.
- Extortion without encryption: While encryption remains common, data theft alone will keep growing because purely data-extortion has been proven to be easier to implement while, at the same time, highly effective for ransom negotiations.
- More time pressure on defenders: Patch-to-exploit windows will shrink as adversaries weaponize vulnerabilities quickly, including suspected zero-day flaws.
Financially motivated young cybercriminals (a.k.a ‘show-offs’) like Scattered Spider will remain a threat
In the 2026 cybersecurity threat landscape, it’s expected that some of the most damaging intrusions will stem from human interaction rather than novel exploits. Young, financially motivated crews keep scaling because of three main factors:
- Persuasive, native-English social engineering attacks.
- Speed and coordination from online communities.
- Access to ransomware tooling through affiliate ecosystems.
Arguably the most relevant group in this category is known as Scattered Spider, a loose and chaotic group of teenagers that emerged from the so called The Com or Hacker Com, the subset of The Com specialized in conducting cyber intrusions. At first, they focused on carrying out sim swapping attacks, but when cybersecurity measures improved and the attacks turned less profitable, they switched to ransomware attacks and cryptocurrency theft.
In 2025, Scattered Spider became even more disruptive as they established an alliance with important cybercrime groups that resulted in the infamous triad Scattered Lapsus$ Hunters, an alliance composed members of Scattered Spider, Lapsus$, and Shiny Hunters. Through Telegram channels, they have claimed some of the most notorious attacks reported in media this 2025, including the Jaguar Land Rover incident that halted factory activity for weeks.
They leverage their wide reach on Telegram to obtain initial access and recruit insiders in large corporations, ask for proof of access to common enterprise identity environments and propose a commission-style payout model.
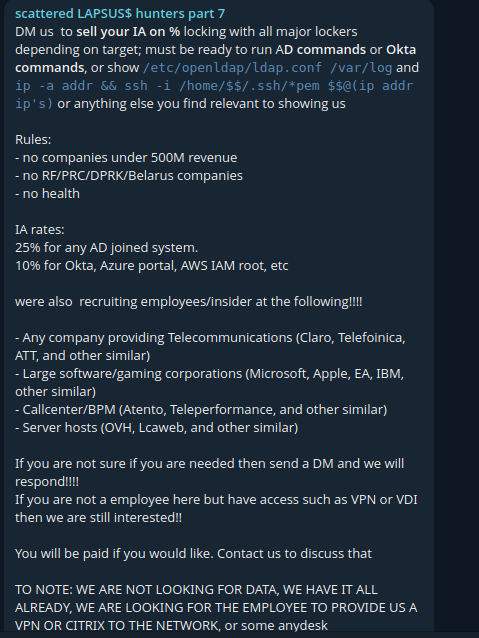
Screenshot from the Scattered Lapsus$ Hunters Telegram channel soliciting initial access and insider participation, with commission-style payouts and preferred target categories.
Many Scattered Lapsus$ Hunters victims in 2025 were targeted as clients of the Salesforce CRM platform, including Adidas, Allianz Life, Chanel, Pandora, LVMH subsidiaries, and Qantas. Their modus operandi in this incident involved voice phishing calls. The threat actor called English-speaking employees, pretended to be IT support, and tricked them into revealing login credentials or installing malicious versions of Salesforce tools. In another campaign (also targeting Salesforce clients), they compromised OAuth tokens from the Salesloft Drift integration to query Salesforce data at scale.
The threats that will enable young cybercriminals in 2026
- Vishing: Enabled by artificial intelligence, vishing will remain a primary initial access vector for attacks in 2026. Attackers will continue using scripts, pressure tactics, and “support workflows” to ensure desired actions are taken.
- Software-as-a-Service (SaaS) adjacent compromise: Attackers will increasingly target the customer and the connected app surface, not the SaaS provider.
- Affiliate-driven ransomware use: Groups will not need to build ransomware; they can instead deploy it via RaaS partners, rebrands, or “cartel” models to scale impact.
Clouds (a.k.a. credential logs) will deliver data resale at scale
In the infostealer economy, “clouds” are Telegram-based log distribution channels that package and deliver stolen data at scale. Many operate with a free channel that posts samples and a paid tier that provides broader, fresher access, often via subscriptions. The logs frequently include credentials, browser data, and other artifacts that make account takeover and session hijacking easier.
This model depends on a wider traffer ecosystem: operators and “traffic teams” provide malware builds, alongside necessary infrastructure, and training. The traffers focus on distribution and infection volume. The result is a pipeline: infections produce logs, logs feed clouds, clouds feed follow-on criminals who specialize in filtering and abusing corporate access.
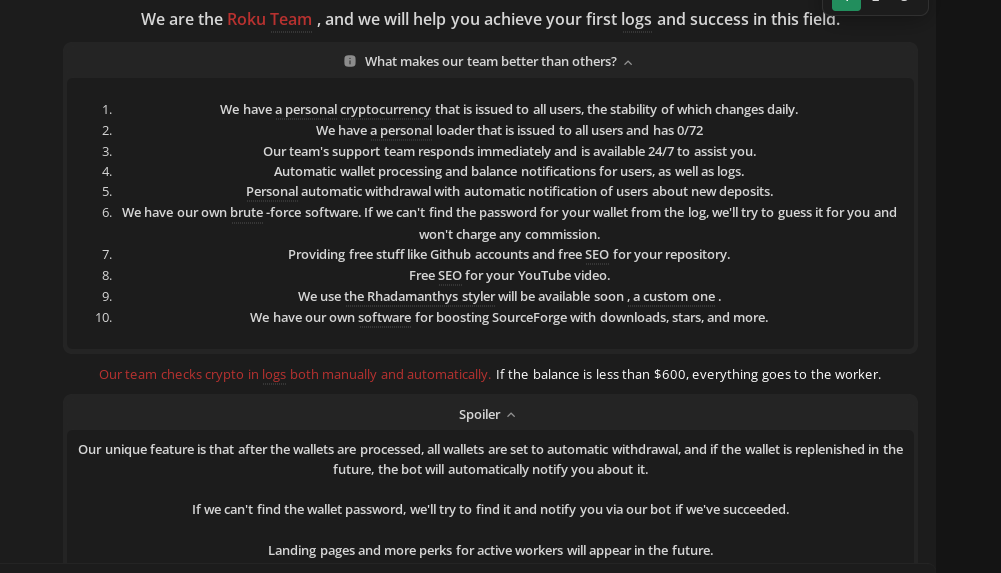
Underground forum announcement by traffer team Roku Team promoting loader access, 24/7 support, and automated wallet handling.
Rather than running phishing or malware campaigns, a buyer simply purchases the data and then pivots to:
- Account takeover
- Password reset abuse
- Session replay via cookies and tokens
- Downstream attacks (fraud, data theft, ransomware staging)
What we expect to intensify in 2026
- Greater log volume, more buyers, lower skill requirements: Telegram makes access frictionless compared to traditional forums.
- Corporate exposure through personal behaviour: With greater blending of work and personal device usage and increased teleworking adoption, one compromised endpoint can leak browser sessions and credentials used for work.
- More initial access checker tools: Buyers will continue sorting logs for corporate domains, virtual private networks, SaaS, and admin portals, then test access at scale.
How to stay secure
To navigate the 2026 cybersecurity threat landscape, identity and support workflows will need to function as a primary control point. Phishing-resistant multi-factor authentication (MFA) for admins, helpdesk, and SaaS owners can reduce the impact of vishing and credential reuse. Stronger verification for resets and device enrollments, plus fast alerting on MFA changes, new devices, OAuth consents, and connected apps, can trigger warnings to spot intrusions early or even prevent them entirely.
It’s likely that persistent threats from the ransomware ecosystem will include data-theft extorsion with quieter intrusions and the abuse of widely used enterprise software that allows one flaw to impact many organizations simultaneously. A clear inventory of internet-facing apps, faster patching, and exposure reduction through network segmentation and web application firewall controls can lower the chance that a single exploited app tier becomes a broad data-theft event. Monitoring for bulk exports, archive creation, and unusual outbound transfers often provides earlier warning than waiting for encryption.
Finally, mitigating the threat of Telegram “cloud” stealer-log distribution is most effective when efforts focus on disrupting the stealer-to-access pipeline. Reducing stealer infections where possible, treating browsers and sessions as sensitive assets, and making session revocation plus credential resets easy to execute when exposure signals appear can limit how far stolen logs go when they include corporate access.
How Outpost24 can help
Defending your organization against an ever-evolving cybersecurity threat landscape doesn’t need to be complicated. If you want a quick signal on whether your organization is exposed, you can use Outpost24’s free Compromised Credentials Checker to scan your email domain for leaked credentials.
If you’re interested in learning how our Threat Intelligence team could help your organization contact us today.

