15 Nov 2023
A pen tester’s perspective on the most common issues with vulnerability scanning and traditional pen testing of modern web apps.
03 Nov 2023
Examples of broken access control vulnerabilities and why they remain present even after vulnerability scans and assessments.
06 Sep 2023
In this blog, one of our Application Security Auditors takes a look at the new HTTP request vulnerability, gives a...
27 Apr 2023
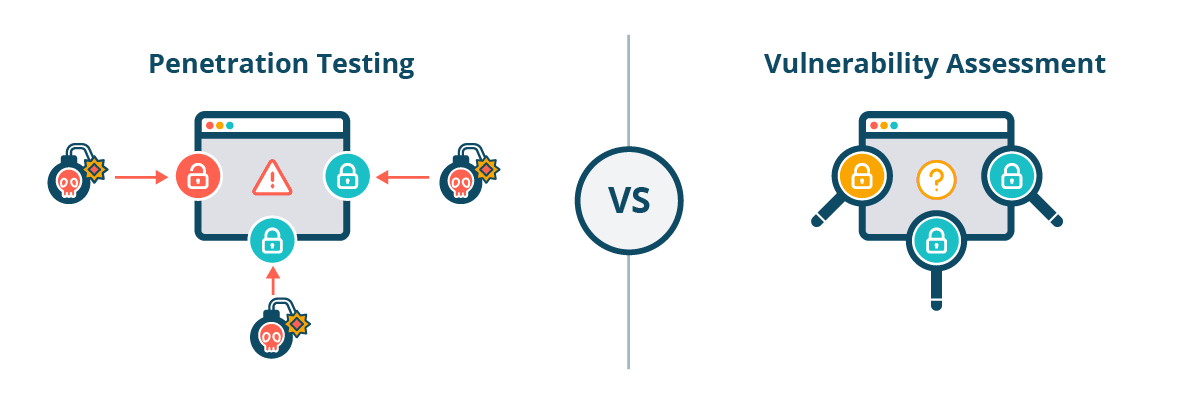
Vulnerability scanning and penetration testing should be an essential part of your cybersecurity strategy. This blog discusses the above methods...
08 Mar 2023
How an Account Takeover vulnerability, discovered during a routine customer engagement, became a candidate for responsible disclosure, via the Microsoft...