Threat Actor Profile – Sodinokibi ransomware
Research & Threat Intelti-platform-feed
Last updated: 21 May 2025
Meet “Sodinokibi” this month, the threat group behind the eponymous Sodinokibi ransomware, also known as “REvil”, to understand their tactics and how you can better secure your system from this threat
Threat actor profile: Sodinokibi
Known Aliases
- Sodin
- REvil
- Gold Southfield
- Sodinokibi
- UNKN
- Unknown
- White Ursia
Key points
- The Sodinokibi aka REvil threat group is comprised of the developers behind the eponymous Sodinokibi Ransomware-as-a-Service offering.
- Previous affiliates of GandCrab ransomware moved to Sodinokibi to continue their attacks after the developers of GandCrab publicly announced their “retirement” in May 2019.
- If certain languages (mainly Russian, CIS and Syrian Arabic) are detected in the victim’s system, the ransomware attack is aborted.
- Some research suggests that the threat actors behind GandCrab and Sodinokibi are linked.
Deep Dive
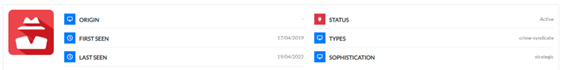
- “Sodinokibi” is the threat group behind the eponymous Sodinokibi ransomware, also known as “REvil”. The first activity attributed to this threat group dates from April 2019 when they exploited the critical vulnerability CVE-2019-2725 to install Sodinokibi ransomware. This vulnerability affected Oracle WebLogic and anyone with HTTP access to the WebLogic server was able to carry out an attack.
- Since then, according to analysts at Secureworks, affiliates of the Sodinokibi gang continued to distribute their ransomware through exploit kits, scan-and-exploit techniques, remote desktop protocol (RDP) services, and backdoored software installers.
- In late December 2019, the threat group launched a ransomware attack on foreign exchange company Travelex’s network on New Year’s Eve, forcing their website offline and encrypting more than 5GB of sensitive data through a ransom demand of $6 million. It was suggested that the hacker used the critical vulnerability in Pulse Secure VPN CVE-2019-11510 to gain entry and remotely execute malicious code. Travelex was forced into administration as a result.
- In January 2020, the Sodinokibi group published data stolen from Artech Information Systems after the victim refused to pay the demanded ransom. The threat group has shown a willingness to name victims and release stolen information in the event that a ransom is not paid. Sodinokibi was disclosing stolen data on their leak site titled “Happy Blog”: hxxp://dnpscnbaix6nkwvystl3yxglz7nteicqrou3t75tpcc5532cztc46qyd[.]onion. The threat group’s leak site has since been updated to the following address: blogxxu75w63ujqarv476otld7cyjkq4yoswzt4ijadkjwvg3vrvd5yd[.]onion
- Additionally, in June 2020, Sodinokibi was spotted scanning point-of-sale (PoS) systems to compromise.
- Sodinokibi operates on a Ransomware-as-a-Service model, wherein a group of developers maintains the code while their affiliates spread the ransomware. Earnings from paid ransoms are split between the malware developers and the corresponding affiliate. The affiliates are the ones executing the attacks and using different TTPs to do so.
- The Sodinokibi ransomware contains a list of blacklisted languages. If one of these languages is detected on the system of the victim, the ransomware executable will close and stop the attack without performing any action. The blacklisted languages are the following: Romanian (Moldova), Russian, Russian (Moldova), Ukrainian, Belarusian, Estonian, Latvian, Lithuanian, Tajik, Persian, Armenian, Azeri, Georgian, Kazakh, Kyrgyz, Turkmen, Uzbek, Tatar, and Arabic (Syria).
- One of the threat actors behind Sodinokibi posted on an underground forum that it was forbidden to target devices in the Commonwealth of Independent States (CIS). Also, they mentioned that it was also forbidden to attack Syrian computers.
Objective
- Financial gain
Modus Operandi
- Use of a Ransomware-as-a-Service business model to gain profit. Occasionally the group leaks data stolen from victims should they refuse to pay.
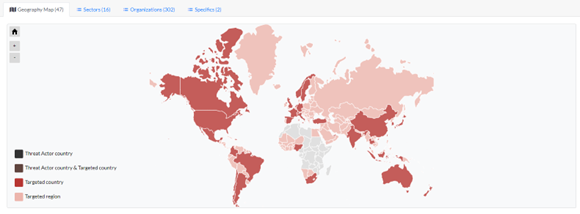
Threat actor Activity Map
Want to know more? Get a demo of our threat intelligence solution. If you are interested in learning how to access this information as Outpost24 customers, please contact your Account Manager for more details.
Other threat actors we’re tracking this month:
- “Fishy Vampire” is a financially-motivated threat actor active since at least July 2020. Fishy Vampire maintains an infrastructure of more than 400 typosquatting domains impersonating popular brands and applications related to cryptocurrencies, stock trading, and various software.
- “Black Reward” is an Iranian hacktivist group that emerged in August 2022 and began its activity by the end of September 2022. Its unique goal is generating disruption in organizations in connection with the actual government of the Islamic Republic of Iran.
- “Prestige” is a ransomware group that first emerged in early October 2022. The threat group has been observed targeting transportation and logistics companies in Poland and Ukraine amidst the ongoing conflict between Russia and the latter.
- The “Ransom Cartel” is a ransomware group first spotted in late 2021 that has been active throughout 2022. The adversary engages in double extortion techniques, threatening to leak exfiltrated files online.
- “spectre123” is the moniker responsible the Spectre’s Intel Repository project, dedicated to the publication of confidential data related to governmental and military-related documents. spectre123 motivation is mainly ideological as they believe releasing confidential documents is “for the sake of betterment of our society”.
- “WIP19” is a Chinese-speaking threat group that is most likely involved in espionage against targets in the Middle East and throughout Asia.
- As well as the following campaigns:
- Indian electric utility Tata Power Company Limited hit by Hive ransomware
- Killnet conducts a DDoS attack against Bulgarian government websites
And the following threat actor tools:
- Venus is a ransomware strain that emerged in 2021 or 2022. The main characteristic of this ransomware is its preference for gaining access to the victim’s corporate network through the Windows Remote Desktop Protocol (RDP), even when the service is running on non-standard ports.
- BlackLotus is a UEFI bootkit for Windows written in C and x86 assembly, aimed at acting as an HTTP loader. It was developed and sold in underground forums by a user under the alias maxwell187 for $5000 (license cost) and $200 (rebuild).
- RatMilad is an Android advanced Remote Access Trojan (RAT) with spyware capabilities. In a campain analysed by Zimperium zLabs researchers, Ratmilad was detected hidden under VPN applications called Text me or NumRen that allegedly provide phone number spoofing capabilities.
- Alchimist is a GoLang-based attack framework, designed to target Windows, Linux, and Mac devices. It was discovered by Cisco Talos researchers in October 2022 and is believed to be of Chinese origin.
