700Credit Breach: What Organizations Need to Know
700Credit, a US-based credit check and compliance provider, disclosed in late October that it had suffered a significant data breach affecting nearly 18,000 dealerships and more than 5.6 million consumers. According to the company’s disclosure and subsequent reporting, the exposed data includes names, addresses, dates of birth, and Social Security numbers.
700Credit has stated that its investigation remains ongoing and that there is currently no indication of identity theft, fraud, or other misuse of the compromised data. The company also maintains that the incident did not impact its internal corporate network and that all unauthorized activity was limited to the 700Dealer.com application layer.
As this incident continues to unfold, KrakenLabs, Outpost24’s Threat Intelligence team has been tracking both the publicly disclosed breach and parallel underground activity indicating that threat actors are actively attempting to monetize the exposed data.
In this advisory, we examine how the 700Credit data breach originated, how the attack developed, what we observed in underground markets, and what lessons security teams should take from this incident.
Where the attack originated and how it developed
In interviews with industry media, 700Credit Managing Director Ken Hill described the breach as the result of a sustained “velocity attack” that began in late October 2025. The attackers gained access through an integration partner whose environment had been compromised months earlier.
The compromised partner failed to notify 700Credit in a timely manner. During that window attackers obtained access to logs and API tokens associated with the partner’s integration. Those credentials allowed the attackers to authenticate successfully and issue large volumes of legitimate-looking API requests against 700Credit’s own systems. Using 700Credit’s APIs, the attackers queried consumer records tied to dealership credit applications.
When these unusual request patterns were detected on October 25, 2025, 700Credit shut down the exposed API endpoint and initiated forensic analysis. According to the company, external cybersecurity specialists confirmed that the attackers did not gain access to internal networks or backend systems and that no malware was deployed.
However, by the time the activity was contained, threat actors had already exfiltrated a substantial volume of data. 700Credit stated that roughly 20% of stored consumer records accessible through that application layer were pulled before the endpoint was disabled.
This attack did not rely on exploit chains, malware deployment, or privilege escalation within 700Credit’s internal network. It relied on persistent, trusted access through valid credentials tied to an external integration.
Underground sales claims and threat actor activity
As 700Credit worked through containment and disclosure, Outpost24 Threat Intelligence identified parallel activity in underground forums that indicates rapid monetization attempts were already underway.
On November 16, 2025, a user operating under the alias ROOTBOY advertised a 700Credit database for sale on both the Exploit and DarkForums underground forums. The seller claimed the dataset contained approximately 8.4 million customer records, including full names, dates of birth, addresses, Social Security numbers, and, in some cases, employment information. Sample records were posted publicly as proof, and the initial asking price was set at USD 2,500.
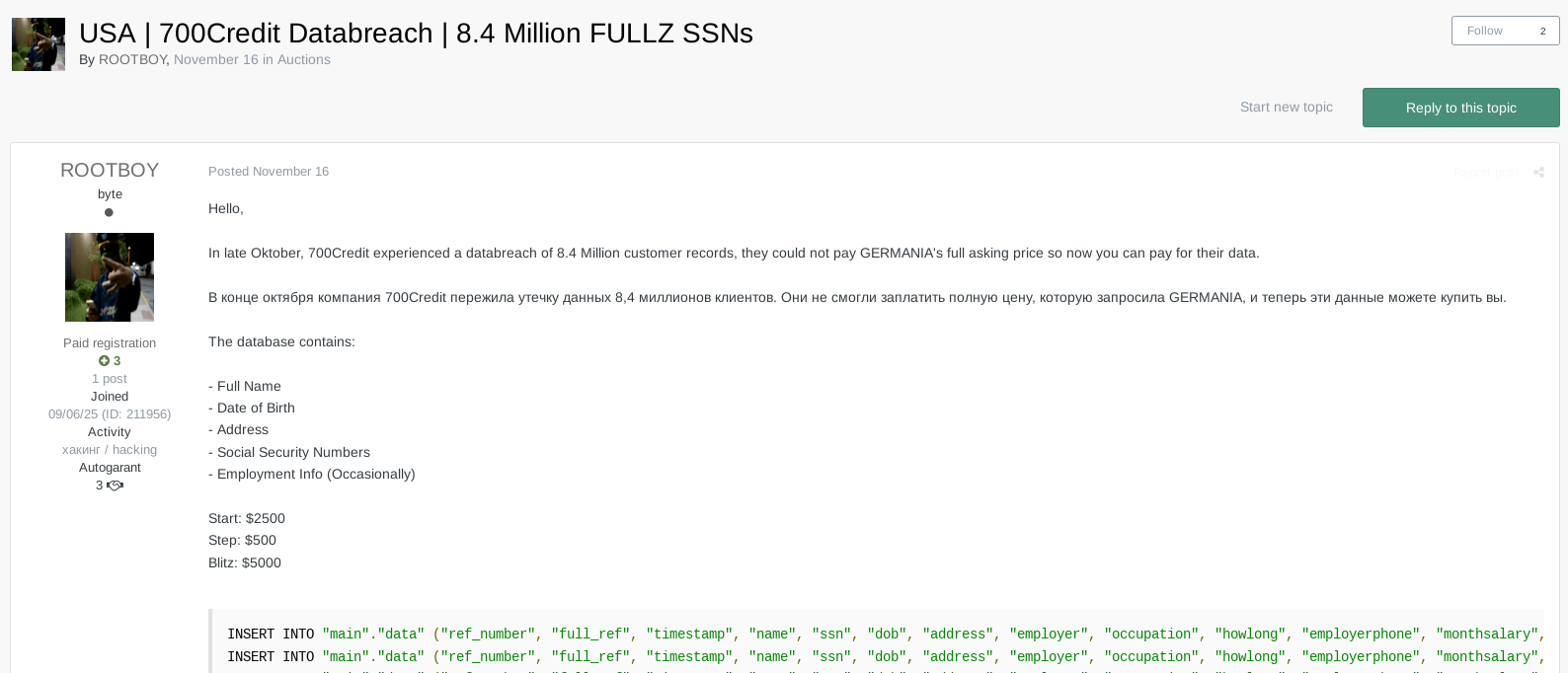
Exploit forum post advertising the alleged 700Credit database and record count.
In the same post, ROOTBOY stated that the data was being sold after a failed extortion attempt. The seller referenced a payment demand issued under the name GERMANIA, which appears to be an alternate identity used by the same actor based on linked Telegram accounts.
Later that same day, another forum user using the handle, onetime, initiated an auction thread for the dataset on Exploit. According to follow-up comments from the seller, the auction concluded within hours. While there is limited publicly available information on the buyer, the rapid progression from listing to auction close strongly suggests the data was sold.
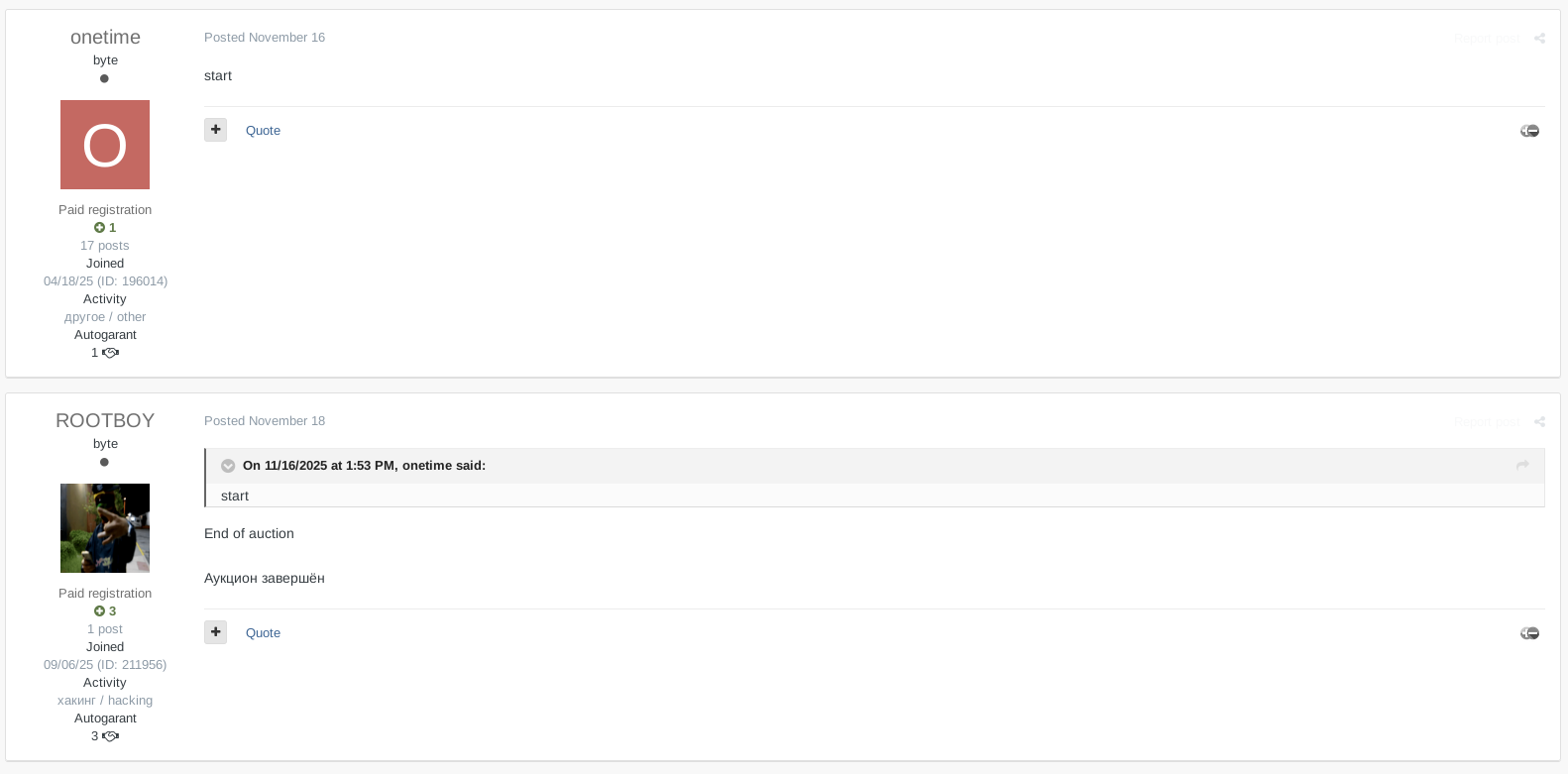
The exploit forum auction thread showing the start and end of the sale.
Following the conclusion of the auction, ROOTBOY removed the proof samples from Exploit and deleted the corresponding DarkForums post. This behavior is consistent with established underground tradecraft, where sellers routinely remove evidence after a transaction to reduce exposure, avoid moderation or law enforcement scrutiny, and preserve resale value.
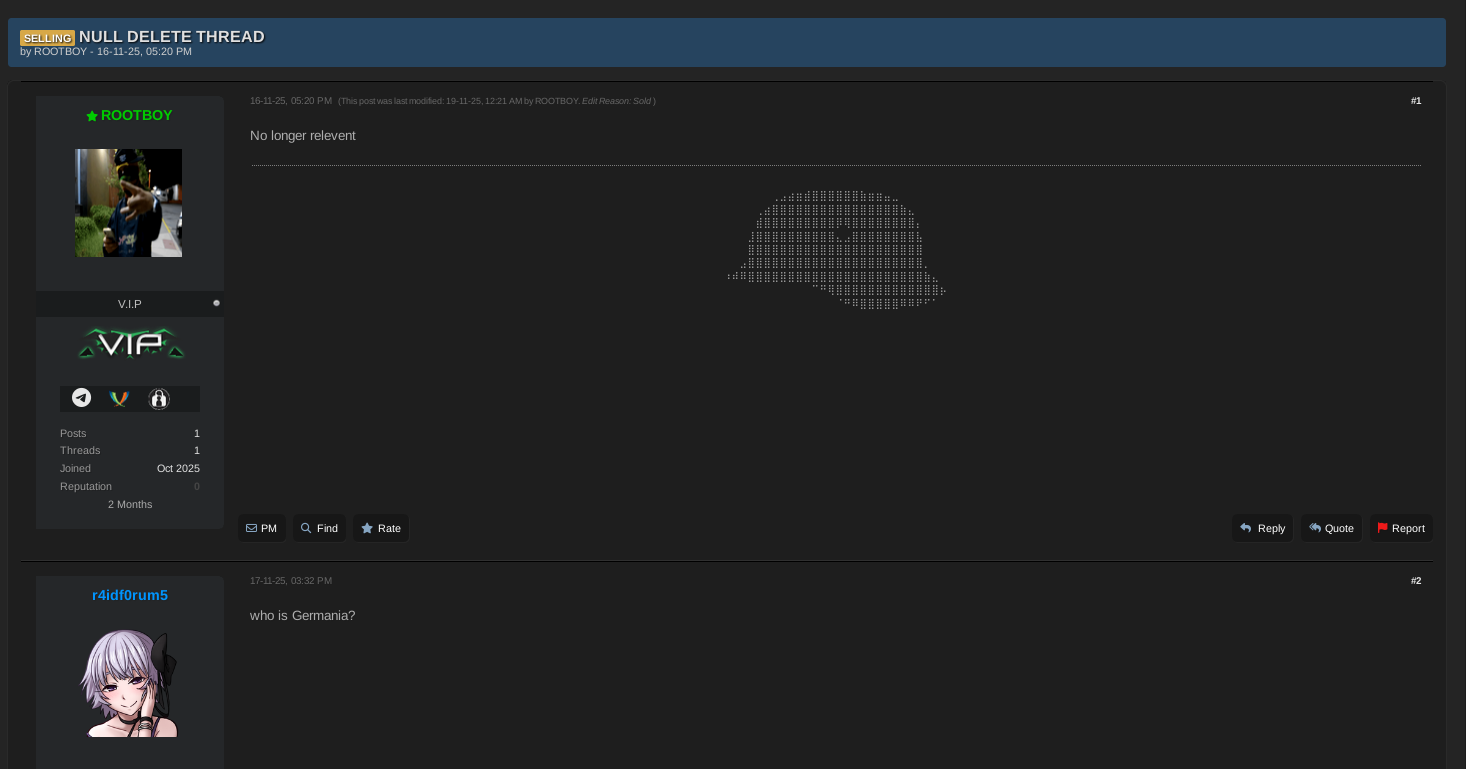
The deleted DarkForums post.
Despite the deletion this information can still be found from other sources, as seen in the images below:
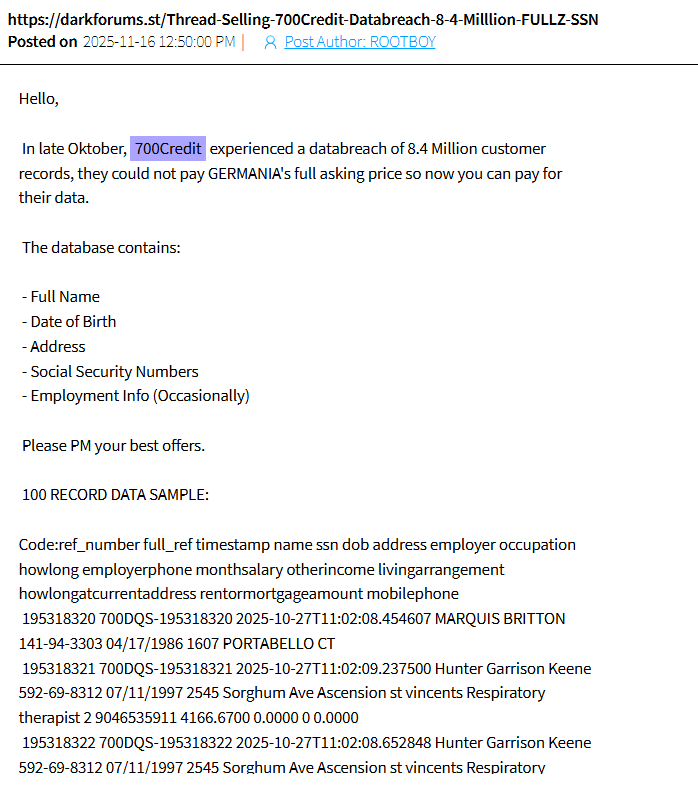
Original Darkforums post auctioning 700Credit data (fragment).
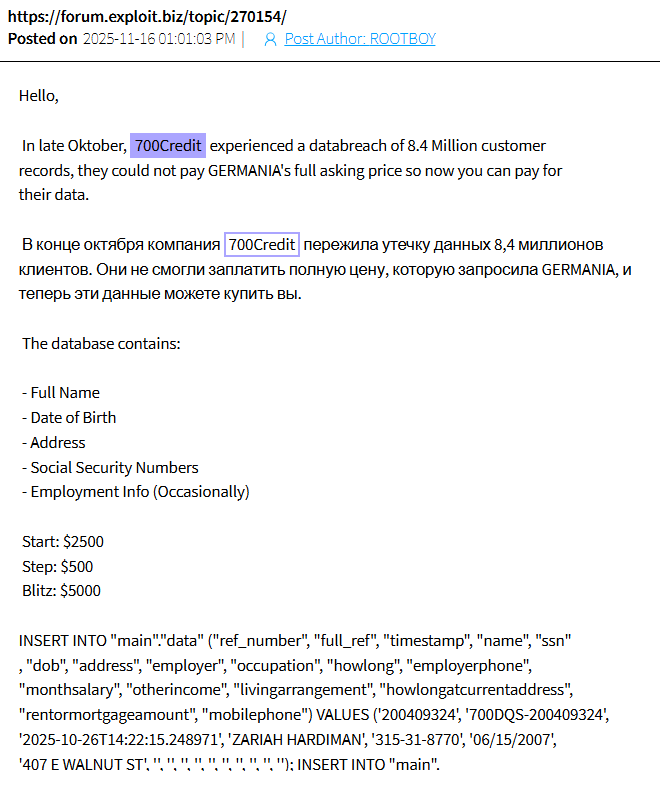
Original Exploit post (fragment).
ROOTBOY activity and actor profiling
Although ROOTBOY presents as a relatively new identity, their activity suggests familiarity with underground data markets rather than a first-time seller.
ROOTBOY joined the Exploit forum on September 6, 2025. Since then, they have advertised two databases containing U.S. citizen data, including the 700Credit dataset, and have participated in the auction of another dataset. Their DarkForums account was created on October 8, 2025, and the 700Credit thread appears to be their only post there at the time of writing. The profile includes a signature image resembling a military helmet, a motif commonly used in underground forums to signal experience or posture rather than attribution.
ROOTBOY’s DarkForum profile.
ROOTBOY also advertises multiple off-platform communication channels, including TOX, Telegram, and Jabber. Notably, the TOX ID shared in ROOTBOY’s listings, 496187425B2944D73FBB17CAF3F9FD569B9ED3A08A497A8314CB4F27A51E65081ACEE1E22F21, has been linked to another underground identity, avtokz, active on the XSS forum.
The avtokz account joined XSS on July 9, 2025 and previously advertised the sale of a database belonging to another U.S.-based financial services company, Vantage Finance. In that case, the seller claimed the compromise occurred in April 2025, with the data listed for sale on July 14 and sold several days later on July 21. On the same day the sale reportedly concluded, Vantage Finance appeared on the Everest ransomware group’s data leak site.
While the timing is notable, Outpost24 Threat Intelligence cannot confirm that the Everest ransomware group purchased the dataset or was directly involved in that transaction. It is also worth noting that Vantage Finance had previously disclosed a separate breach in August 2024, which complicates attribution and reinforces the need for caution when correlating underground sales with ransomware group activity.
What this linkage does demonstrate is reuse of infrastructure and identifiers across multiple financial-sector data sales. This pattern is typical of commercially motivated actors who rotate aliases while maintaining persistent communication channels, allowing them to build reputation and move quickly between datasets.
At this stage, there is no evidence tying ROOTBOY to a named ransomware group in the 700Credit incident. The activity observed is consistent with independent data brokers operating within underground marketplaces, focused on rapid resale rather than prolonged extortion campaigns.
Security takeaways from the 700Credit data breach
This incident demonstrates how supply-chain attacks increasingly exploit trusted integrations rather than perimeter weaknesses. When third-party access paths fall outside continuous monitoring, attackers gain sustained dwell time. In the 700Credit case, the breach was not driven by exploitation or lateral movement, but by valid access being used at scale.
The attack also highlights the operational dependency between API security and credential governance. Persistent API access is underpinned by credentials, including service accounts, API keys, and long-lived tokens. When those credentials are exposed or insufficiently governed, attackers do not need to bypass controls. They reuse legitimate access and operate within expected request patterns until volume or velocity triggers detection.
Credential failures in these scenarios are rarely singular events. They emerge through accumulated weaknesses such as reused credentials across environments, tokens without expiration or rotation, and access that persists beyond changes in partner relationships. These conditions create stable access paths that attackers can abuse quietly over time.
For teams responsible for password security, identity management, and external risk, this breach raises uncomfortable but necessary questions.
- Do you know which APIs are exposed beyond your core environment?
- Are third-party integrations monitored continuously or reviewed only during periodic audits?
- Would you know if your data appeared in underground marketplaces?
- How quickly could you revoke or rotate credentials tied to external access paths?
Answering these questions honestly often reveals gaps not because teams are careless, but because environments have evolved faster than visibility and governance models.
How Outpost24 helps reduce exposure
The 700Credit data breach illustrates how supply chain incidents often stem from exposure outside an organization’s direct control, including inherited infrastructure, third-party integrations, and externally accessible application layers. Outpost24’s External Attack Surface Management helps organizations maintain continuous visibility into internet-facing assets, including shadow IT and partner-connected systems, so unmanaged exposure can be identified and addressed before it is abused.
When breaches move beyond initial access and into data theft or resale, understanding external threat activity becomes just as important. Digital Risk Protection provides ongoing monitoring of leaked credentials, underground marketplaces, impersonation attempts, and supplier-related risk. Used alongside attack surface visibility or on its own, this intelligence helps teams recognize when stolen data or access is being discussed or traded and respond earlier.
To further reduce risk, Outpost24 supports continuous validation of real-world exposure across applications, APIs, and access points. Outpost24’s Application Security, Penetration Testing-as-a-Service, and Red Teaming services test how attackers exploit trust relationships and credentials in practice.
Together, these capabilities help organizations address the same types of weaknesses exploited in the 700Credit incident before they can be leveraged at scale.
Let’s Talk
See your attack surface the way attackers do. Get in touch to schedule a personalized demo or trial of Outpost24’s integrated platform and start taking control of your digital exposure today.

