Application Pen Testing as a Service (PTaas)
Elevate your security with SWAT, our comprehensive and continuous Pen Testing as a Service (PTaaS) solution. Automatically and continuously monitor your internet-facing web applications for the latest vulnerabilities, ensuring continuous protection, zero false positives and results verified by our certified pen testers.
About PTaaS with SWAT
Test your apps in real-time for the latest vulnerabilities. SWAT delivers continuous monitoring of internet facing web applications via a SaaS delivery model. The solution can be fully customized to your needs, minimizing unnecessary load, or risk to any sensitive environments. Most vulnerability findings are produced by our in-house testing team, and peer reviewed by a senior pen tester. You can also interact directly with our security experts for validation and remediation guidance, all via the portal.

Human-led Pen Testing
Our highly skilled and experienced pen testers will give you the most accurate view of your vulnerabilities including business logic errors and backdoors that automated scanners missed.

Automated scanning
Our application security scanner provides a good balance of speed to results and keeps your business moving forward with continuous monitoring.

Context-aware risk scoring
Prioritize your remediation efforts based on the vulnerabilities that pose the highest risks to your business.
How PTaaS works
Pen testing is an effective way to detect flaws in your application before they turn into a serious threat. But traditional pen testing delivery takes weeks to set up, and the results are point in time. This leaves critical application vulnerabilities exposed longer, while the average time for a threat actor to weaponize a new vulnerability gets shorter.
A new wave of automated pen tests conducted through a SaaS delivery model can fix this problem. PTaaS provides you with a view into your vulnerability finding in real-time via a dedicated portal. By switching to a PTaaS solution, such as Outpost24’s SWAT, you can achieve a deeper level of security monitoring and risk detection.
Outpost24 named Challenger and Fast Mover in the 2025 GigaOm Radar for Penetration Testing as a Service (PTaaS)


SWAT features
- Meet compliance requirements for ISO, PCI, SOC2, HIPAA, CREST, and NIST
- Strong focus on business logic flaws and new or unknown vulnerabilities
- Customized testing based on your specific needs and scope (whether it be avoiding certain sensitive areas or using specific data input)
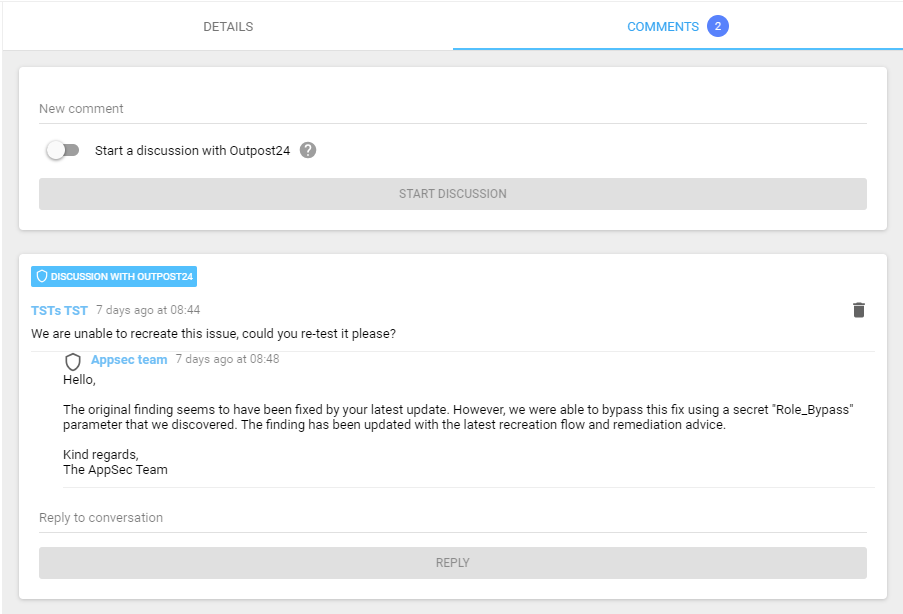
- Direct communication channel between your developers and Outpost24’s pen testers
- Re-testing and remediation validation
- Change detection and unlimited verification of applied fixes
- Continuous monitoring and real-time insights of your vulnerabilities in a single UI
- Zero false positives
- DevOps integration
- Configurable notifications (e.g. if a high-risk finding has been found)
Continuous Pen Testing with SWAT
Continuous penetration testing as a service with our SWAT solution offers organizations a dynamic and ongoing approach to application security, ideal for fast-paced DevOps environments. Unlike traditional pen testing, which is periodic and reactive, PTaaS allows tests to be triggered whenever needed, providing better control over costs and more frequent assessments. Outpost24 takes this further with a hybrid model that combines human-led penetration testing with automated scanning. This fusion enables continuous monitoring and proactive vulnerability detection, ensuring your applications stay secure while minimizing delays in your development cycle.

PTaaS with integrated attack surface management
With CyberFlex, our certified pen testers will analyze your application’s attack surface and provide in-depth insights, helping you prioritize critical threats and ensuring an impenetrable appsec program for complete security peace of mind.
Just some customers who trust us
Frequently Asked Questions
PTaaS is a comprehensive security solution that uses automated and continuous testing to identify vulnerabilities in your critical applications, ensuring real-time insights and faster remediation. Our service, fully customizable and backed by EU-based and certified pen testers, provides accurate, in-depth findings verified by our in-house Appsec team and all accessible through a user-friendly portal.
PTaaS differs from traditional penetration testing in that it offers continuous, automated security assessments and real-time insights, whereas traditional penetration testing is typically a one-time or periodic manual process. PTaaS also provides ongoing support and customizable solutions, ensuring that your security measures stay up to date with the latest threats.
Outpost24’s PTaaS offers extensive and custom manual testing, with the option to automate scans for continuous monitoring. Unlike traditional pen testing delivery, Outpost24’s findings are delivered in real-time via a dedicated portal that also connects you directly with our security experts.
PTaaS allows agile organizations to expedite remediation during testing, and includes continuous monitoring to minimize your application attack surface. Outpost24’s approach to PTaaS also guarantees zero false positives, as findings are produced and verified by security experts.
Yes, Outpost24 will verify the effectiveness of your remediation beyond the test length.
Our risk-based approach helps you prioritize remediation efforts based on the highest risks posed to your business.
Yes, the reports can be exported to PDF, Excel, and XML. The report data is fully configurable and can be presented in both technical and business context, depending on the audience.
PTaaS eliminates the need for frequent vendor rotation by streamlining the pen testing process. Traditional pen testing often involves onboarding new vendors, which can be both time-consuming and costly. Some organizations choose to rotate vendors in order to benefit from different testers’ specializations and expertise, as each tester may uncover vulnerabilities that others might miss. However, with PTaaS, this concern is effectively addressed. Outpost24’s PTaaS offers a larger pool of skilled testers and encourages creative testing, ensuring a fresh perspective on your web application security. Our experts are always on standby to address any problems that arise, providing comprehensive coverage and eliminating the hassle associated with vendor rotation.
Success Stories
Success stories and real-world examples of how SWAT is helping businesses improve their security posture, without slowing down development.
Request A Live Demo
Please fill in your information to submit a demo request. All fields are mandatory.