
Pulled Pork and Watermelon: Why Integrated Cybersecurity Depends on Unlikely Synergies
Learn how a more integrated cybersecurity environment can enable stronger defense with advice from Outpost24 experts.
Read moreContinuously identify, prioritize, and reduce vulnerability exposure across your network and cloud environments using threat-intelligence-driven risk scoring and automated workflows.
Risk-Based Vulnerability Management
Risk-based vulnerability management built for real-world exploit activity, continuous exposure detection, and measurable risk reduction.
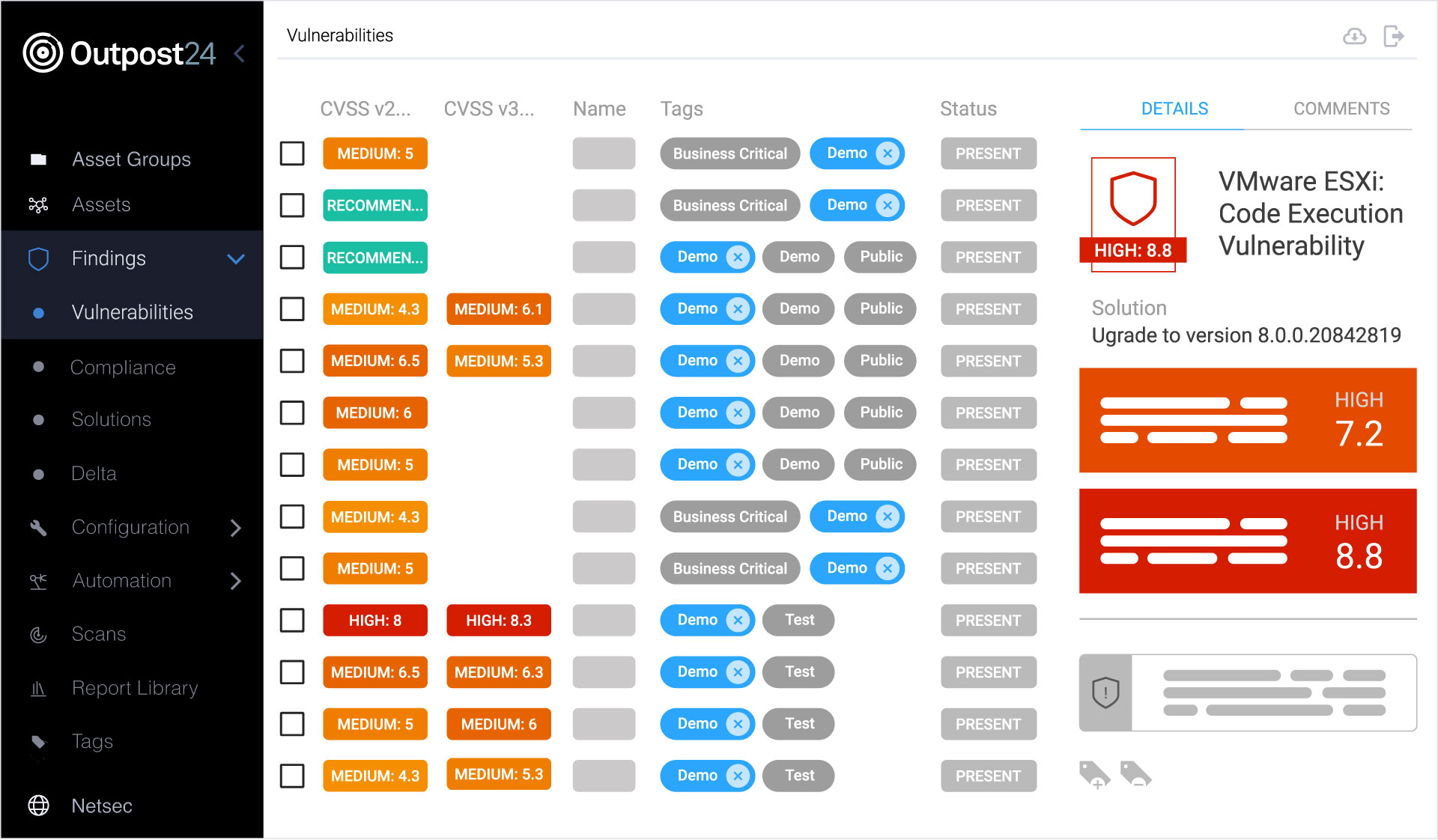
Prioritize vulnerabilities using Outpost24’s Farsight risk scoring, combining real-world exploit intelligence with CVSS, EPSS, KEV, and asset context to focus remediation where it matters most. Understand which vulnerabilities pose the greatest risk based on exploit activity, asset criticality, and threat context, enabling faster, more confident remediation decisions.
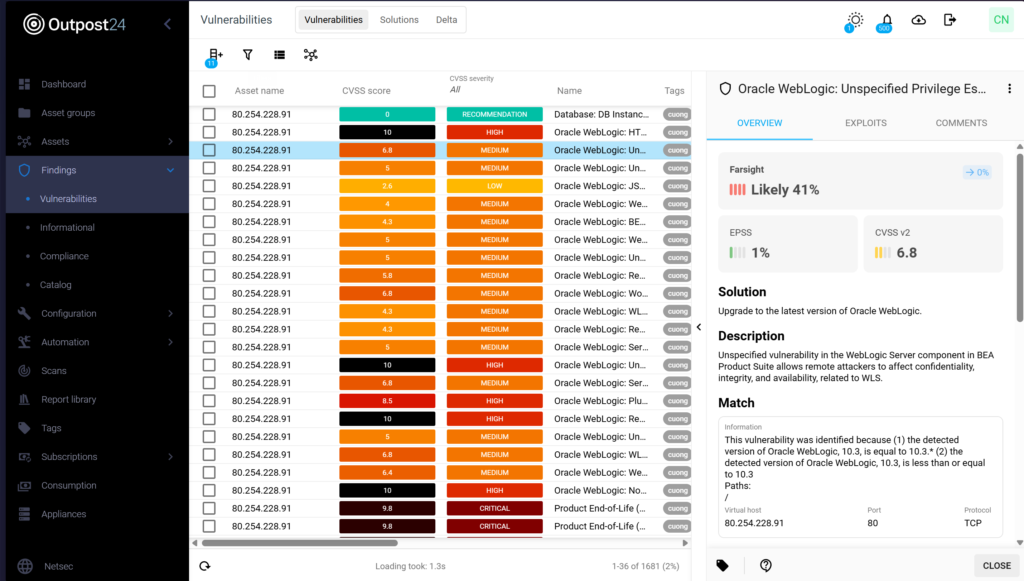
Maintain continuous visibility across your network and cloud environments with ongoing vulnerability discovery and scanning-less detection. Instantly identify newly disclosed vulnerabilities without waiting for the next scan cycle.
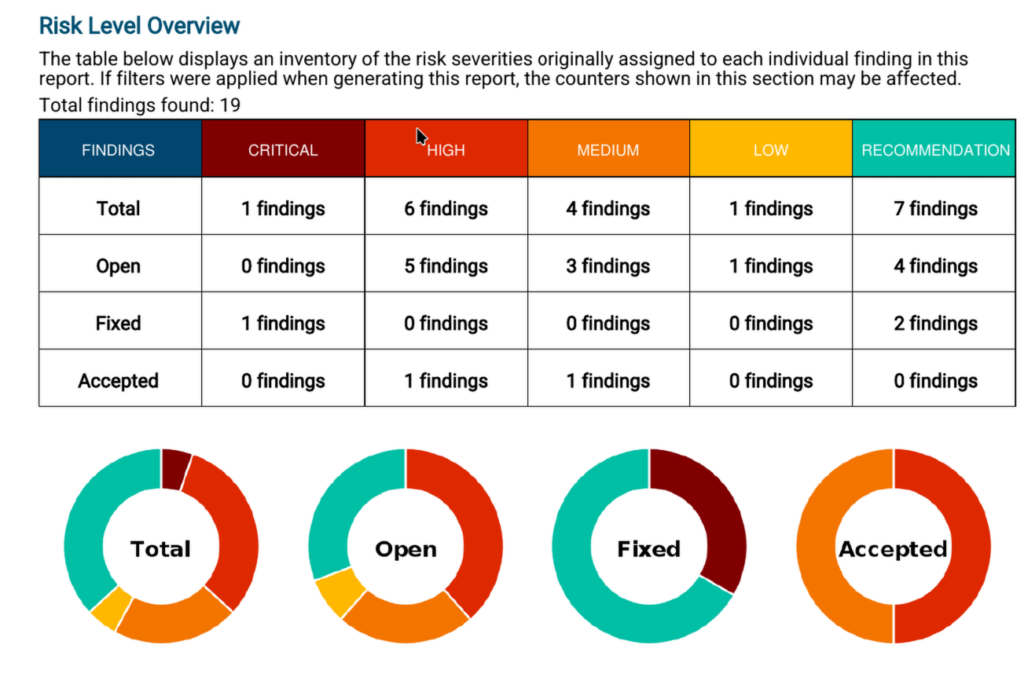
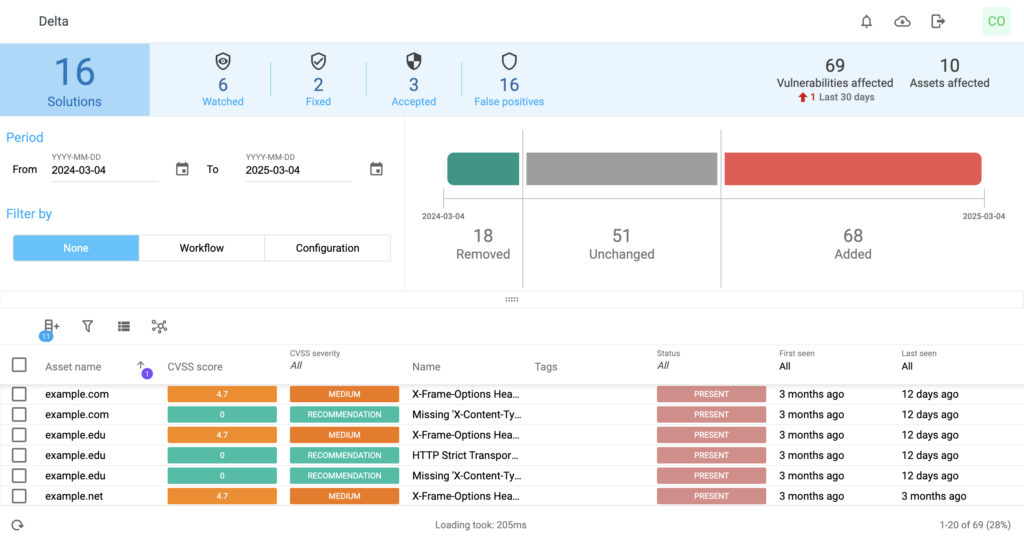
Demonstrate remediation progress and validate security improvements using solution and delta-based reporting. Track risk reduction over time and provide clear, actionable insights for security teams and leadership.
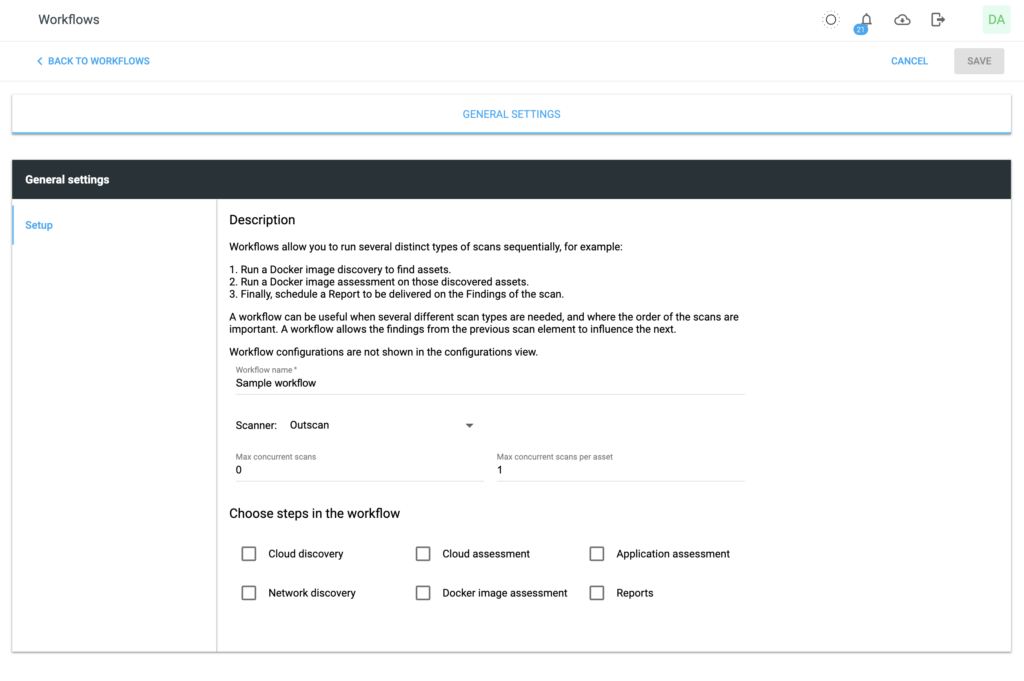
Streamline vulnerability management with automated workflows, notifications, and integrations with tools such as Jira, ServiceNow, Slack, and SIEM platforms, reducing manual effort and accelerating remediation.

Simplify your compliance and audit efforts. Outpost24 OutscanNX is designed to align with these common regulatory and industry requirements:
Risk-based vulnerability management is an informed approach to the prioritization and remediation of your attack surface vulnerabilities based on risks relevant to your business.
A risk-based approach to vulnerability management helps businesses understand threat context so they can prioritize remediations based on the highest risks posed, rather than wasting time and resources on vulnerabilities that pose little threat.
OutscanNX integrates with our cyber threat intelligence solution for advanced reporting, beyond CVSS scoring. Risk scores are based on exploitability, and adapted to new information and activities in the wild.
Yes, the reports can be exported to PDF, Excel, and XML. The report data is fully configurable and can be presented in both technical and business context, depending on the audience.
OutscanNX keeps you protected between scans, and minimizes your exposure windows for attacks with its unique scanning-less scanning technology. When a new vulnerability is discovered, OutscanNX compares it with the information from your last scan, and informs you if any systems could be affected.
Explore additional resources.

Please submit your information and a member of our team will be in touch to schedule a discussion. All fields are mandatory.
Check our latest research, blogs, and best practices to level-up your cybersecurity program.

Learn how a more integrated cybersecurity environment can enable stronger defense with advice from Outpost24 experts.
Read more


Last year, nearly 60% of cyber compromises were directly attributable to unpatched vulnerabilities – flaws that organizations knew about but hadn’t remediated in time.…
Read more


Outpost24’s security experts predict the emerging threats that will shape the cybersecurity landscape in 2024
Read more