Traffers and the growing threat against credentials
The Rising Threat of Traffers report, compiled by Outpost24’s Threat Intelligence team, KrakenLabs, provides a deep dive into the credential theft ecosystem, and encourages organizations to evaluate their security measures against these evolving threats.
In recent years, the theft of credentials has evolved into a highly professionalized cybercriminal activity. The number of Initial Access Brokers (IABs) skyrocketed, ransomware groups multiplied, malware prices increased, and Traffers have emerged.
Traffers are organized groups of cybercriminals specializing in credential theft using malware, most commonly stealers. To spread the malware as far and wide as possible, they have formed an industry-like structure of product and service providers, as well as dedicated marketplaces, in the form of Telegram channels, to facilitate the sale of those credentials.
Outpost24’s Threat Intelligence team, KrakenLabs, has been monitoring several Traffers groups, gathering information from forums and Telegram channels, as well as obtaining and analyzing malware samples from different sources. Our most robust findings are shared in our Rising Threat of Traffers report, which can be downloaded free from here.
Here are some highlights from our research, focusing on understanding how these teams operate, and their influence in the credential theft market.
The anatomy of a Traffer organization
Traffer teams are sophisticated operations with a pyramid-like structure. At the top, you will find the “administrators”, who make the initial capital investment to start the group. The administrators are responsible for developing and testing malware, setting up infrastructure, and recruiting members to join their team. Moving down the pyramid, you will find the “Traffers,” often younger people with basic computer knowledge, and little experience in this sort of operation. These recruits are trained in various malware and credential-stealing techniques and integrated into the operations.
Infection techniques and malware delivery strategy
The main goal of the Traffers teams is to deliver their stealers onto a target system. These groups predominantly use social engineering tactics to achieve this objective. The following shows what the work chain of Traffers looks like.
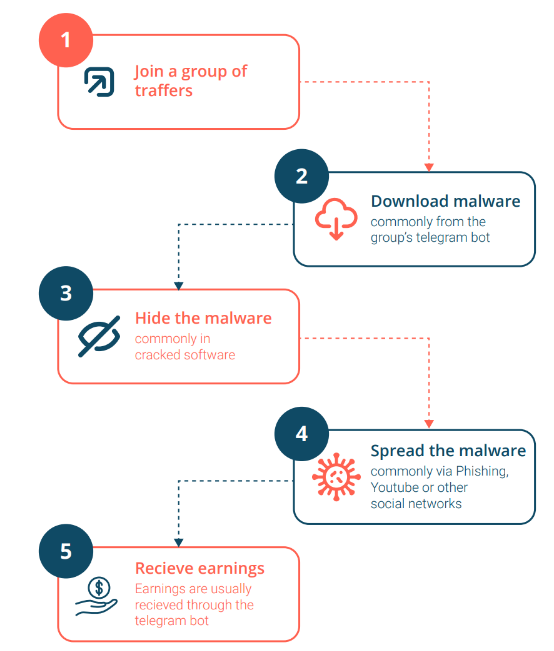
A recruit finds a group of Traffers in an underground forum, and contacts the administrator to join the group. Once they are in the group, they download the malware, and work on infecting as many devices as possible. A common way of doing this is through YouTube videos or Google ads to fraudulent content.
Once the malware is deployed, it will start searching for valuable data on infected systems. These include credentials, browser history, files, system information (like Windows version and serial keys), e-wallet information, Wi-Fi passwords, etc.
They then upload the stolen data to dedicated log clouds, specific Telegram channels, where buyers can subscribe and buy the stolen logs. As observed by Outpost24’s KrakenLabs, the subscription fees range from US$35/week to US$80/month and up to US$666 for lifetime access.
The growing threat of Traffers
Traffers use the established technique of malware infection to harvest credentials and profit from them, but the scheme through which they achieve their goals, and their overall structure is innovative.
The development of this cybercriminal segment follows the maturing of other cybercriminal niches. With the growing trend of the “as-a-service” model, information has become a commodity, rather than shared for free in forums. Criminal groups are willing to pay for services, which means that they will try to profit from them as much as they can.
Outpost24’s KrakenLabs will continue to monitor these groups, their activities, and how they impact the security landscape. We are committed to providing our clients with up-to-date information about emerging threats, and helping them stay ahead of the curve in defending against them.
Download the report for practical advice on how you can protect business credentials, and avoid malware infections, in the way it is done by Traffers teams.

