What to expect from a web application penetration test
In the digital age, web application penetration testing is one of the most critical elements of an organization’s vulnerability management program. In this blog post we will explain the role of penetration testing plays in protecting your organization against web-related exploitations
What is Web Application Security Testing?
According to the Open Web Application Security Project (OWASP):
“A security test is a method of evaluating the security of a computer system or network by methodically validating and verifying the effectiveness of application security controls. (…) Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.”
In other words, a penetration test is a process in which methodologies and techniques are used in an attempt to identify security weaknesses and flaws that could allow a malicious attacker to cause harm or gain unauthorized access to, the resources located in the targeted system (such as credit card information, sensitive personal data, etc.). Once the security flaws are identified, an analysis of the potential risks and vulnerability impact is provided alongside remediation measures.
This concept applies to the web environment; in this case, the targeted system is the web application, and the evaluation is performed in the context of the website and its associated services, rather than the infrastructure in which it is hosted.
The Cyber Security Landscape
The need for web application-oriented penetration testing is mostly driven by the change in the Security landscape. With more and more vulnerabilities being discovered in web-related products and services every year, organizations and vendors are required to keep their knowledge bases and IT infrastructures as up-to-date as possible to prevent their security status from falling behind.
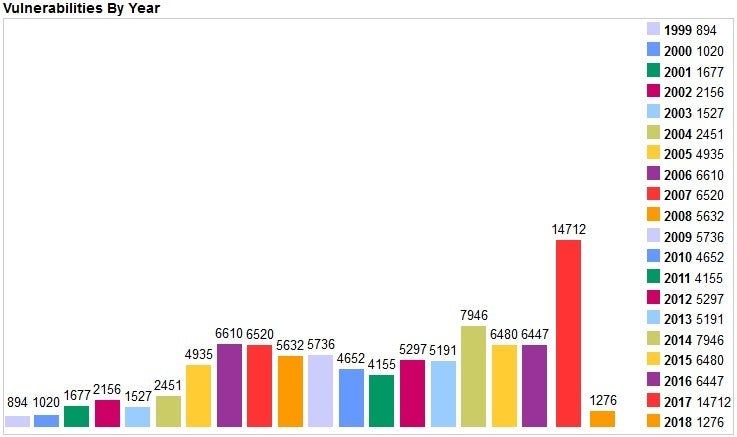
The numbers don’t lie: in 2017 the total amount of registered vulnerabilities has more than doubled its numbers on 2016, according to the Common Vulnerabilities and Exposures (CVE) database, skyrocketing from 6,447 registered vulnerabilities in 2016 to 14,712 in 2017 (Figure 1).
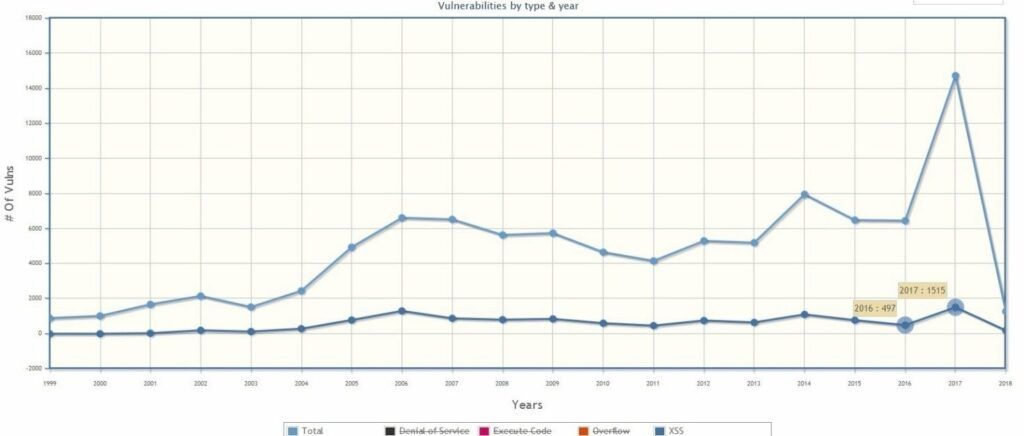
This is truer than ever for web applications. As the development and availability of new technologies such as APIs, IoT devices increased, the amount of potential risks and threats grows consequently. The total amount of published Cross-Site Scripting (XSS) vulnerabilities in the CVE database increased by 304.83%; from 497 registered in 2016 to 1,151 in 2017 (Figure 2).
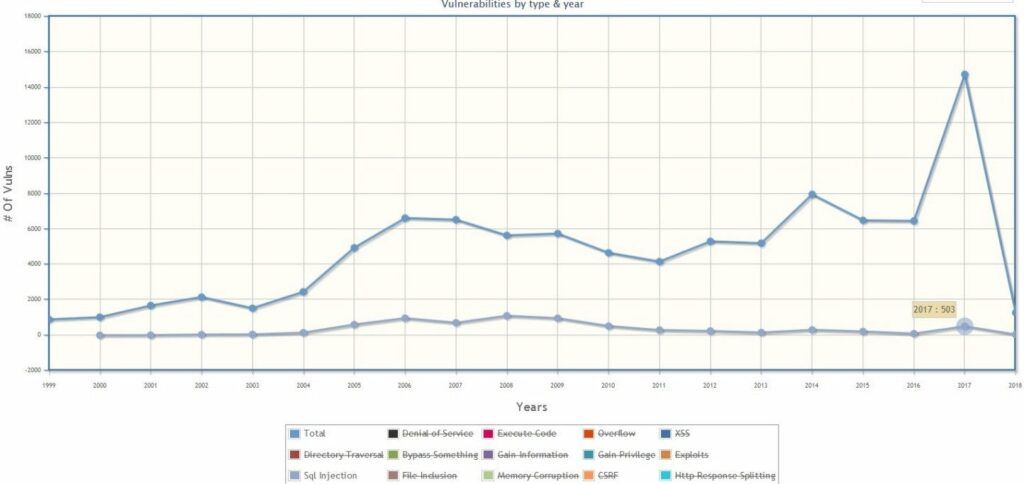
As for SQL Injection (SQLi) vulnerabilities, the increase was of an astonishing 535.12%, jumping from 94 in 2016 to 503 in 2017 (Figure 3).
These examples show a growing trend for two of the most critical threats to Web Application Security in the OWASP Top Ten 2017, a widely-known security awareness document with the ranking of the most critical risks for web applications.
Both Cross-Site Scripting and SQL Injection vulnerabilities have been sensationally exploited in malicious attacks. In 2014, Twitter had to shut down their TweetDeck service as attackers discovered a Cross-Site Scripting vulnerability that left millions of user accounts open for a hijack.
Similarly, attackers were able to steal personal data belonging to thousands of World Trade Organization officials around the world through a SQL Injection flaw in the WTO website in 2015.
Security Lifecycle
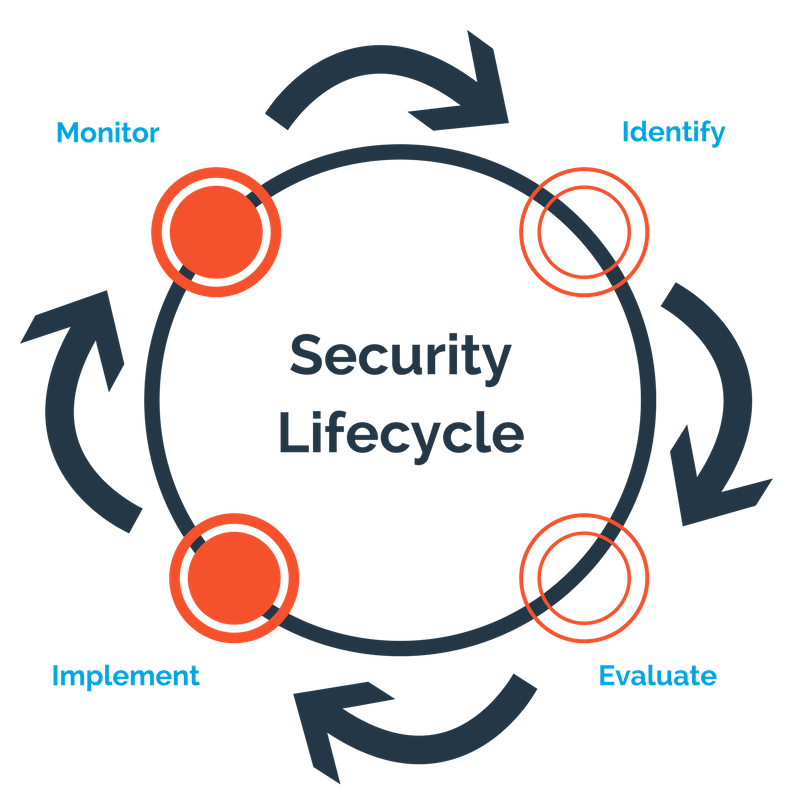
With these in mind, the idea of security can no longer be viewed as static, rather, a continuous process that needs to be maintained over time
Identify potential risks and security flaws within the web application’s context
Evaluate the vulnerabilities existing in the web application by performing a security test
Implement the security fixes and technical remediation required to mitigate the identified vulnerabilities
Monitor the effectiveness of the implemented fixes and the security compliance of newly implemented features and components.
These phases are executed continuously to identify, evaluate and mitigate newly discovered vulnerabilities that may affect an organization’s web applications. This allows organizations to maintain continuous control of the security status of the web application and to implement security updates when required, therefore heightening the security status of their websites and maximizing the value of performing security tests.
How a Web Application Penetration Test is Performed
Security testing is performed following a given methodology; this is, a set of guidelines, rules, and phases that should provide a clear framework which the tester can use to ensure he or she is conducting an accurate and thorough test. There are several different methodologies that testers can follow when performing a penetration test. These include, but are not limited to, the OWASP Testing Guide, Penetration Testing Execution Standard (PTES) and others.
At Outpost24, our tests are performed by experienced and qualified ethical hacking experts, following the Open Source Security Testing Methodology Manual (OSSTMM) by ISECOM when applicable as well as best practices for ISO27005, PCI DSS and NIST standards. Web application security testing is done by using both automated web application assessment tools and manual testing, which ensures all vulnerabilities identified are also manually checked and verified as a result. During the test, our pentesters use web proxies to intercept and analyze the traffic between the web server and the client, amongst other tools.
Phase 1: Discovery and Crawling
Exploring the web application to gather information about the website, its features, and functionality is required to gain a full picture of the web environment. This phase is performed using web application assessment tools, web proxies, and web browsers, and the exploration scenarios vary depending on the scope of the assessment.
Phase 2: Vulnerability Assessment
This phase consists of using a wide variety of techniques and tools to simulate several attack scenarios in a controlled way, attempting to identify and exploit vulnerabilities present in the web application with different approaches. These simulated attacks can be conducted as a privileged user, normal user, non-registered visitor, etc.
Simulated attack scenarios include, for example, unauthorized access to parts of the website only available to authenticated users or users with proper privilege rights, attempts to retrieve sensitive information that should only be accessed by a specific group of users or trying to modify the content of the site in an attempt to deceive or trick a victim.
These testing scenarios include, but are not limited to, the OWASP Top Ten 2017 and Web Application Security Consortium’s Threat Classification. Additionally, the status of the web server hosting the targeted application is also checked for possible misconfigurations, which can result in security flaws that could be exploited by an attacker.
Phase 3: Analysis and Reporting
In the final phase, the pentesters analyze the collected data, gather the necessary evidence of their activities (such as proof-of-concept pieces of code, screenshots and custom developed scripts), and generate a report of the test results. The report provides valuable insight on the vulnerabilities found, explains what the risks are and their impact on the web application and/or the users, alongside a numeric risk score that represents the severity of the vulnerability.
For remediation purposes, the report also includes recommendations on how best to prioritize and fix the vulnerabilities found during the security testing.
Improving Web Applications Security Status
As the number of published vulnerabilities and web-related attacks continues to grow, regular security testing is essential for organizations to maintain their security status and protect their critical business assets from cybercriminals.