Threat Context Monthly: Green Nailao & UNC3886 – Briefing for March 2025
Welcome to the Threat Context Monthly blog series where we provide a comprehensive roundup of the most relevant cybersecurity news and threat information from KrakenLabs, Outpost24’s cyber threat intelligence team. Here’s what you need to know from March about espionage activities by threat actors Green Nailao and UNC3886.
Spotlight threat: Green Nailao – Growing links between ransomware operations and state-related activity
“Green Nailao” is a threat actor active at least since April 2024 targeting European organizations, including entities in the healthcare sector. They are believed to be a Chinese group due to their use of attack patterns and implants such as ShadowPad and PlugX, which are typically associated with threat actors of this origin.
Orange researchers observed them ultimately distributing a relatively unsophisticated and poorly designed ransomware strain dubbed NailaoLocker, which could lead to the hypothesis of a financial motive. However, in the observed attacks, Green Nailao has been seen accessing files and creating ZIP archives, suggesting that data exfiltration is a key objective. This raises the likelihood that the ransomware component is merely a smokescreen to divert attention from their actual espionage activities. The lack of sophistication in NailaoLocker further supports this theory, as the encryption mechanisms are weaker compared to well-established ransomware families, making it a poor tool for financial extortion but an effective distraction for network defenders.
How Green Nailao operate
For gaining initial access, Green Nailao managed to exploit a 0-day vulnerability that had not been related to any other threat group prior to them. More specifically, they had been exploiting CVE-2024-24919, a critical vulnerability affecting Check Point Security Gateways that have Remote Access VPN or Mobile Access features enabled. This flaw allowed the group to enumerate and extract password hashes for all local accounts, providing an initial foothold in targeted networks. Once inside, they carried out network reconnaissance, lateral movement via RDP, and privilege escalation using legitimate binaries side-loaded with malicious DLLs to deploy their payloads.
Green Nailao is the latest addition to a list of likely state-sponsored activity tied to ransomware distribution. Their approach follows an emerging pattern where espionage-motivated actors integrate ransomware into their operations, either as a diversionary tactic or as an additional means of disruption. This trend underscores the need for organizations to not only focus on ransomware mitigation strategies but also to consider the broader implications of data exfiltration and cyber espionage when responding to such threats.
Spotlight threat: Juniper routers exploitation – Chinese espionage group UNC3886 deploys custom malware
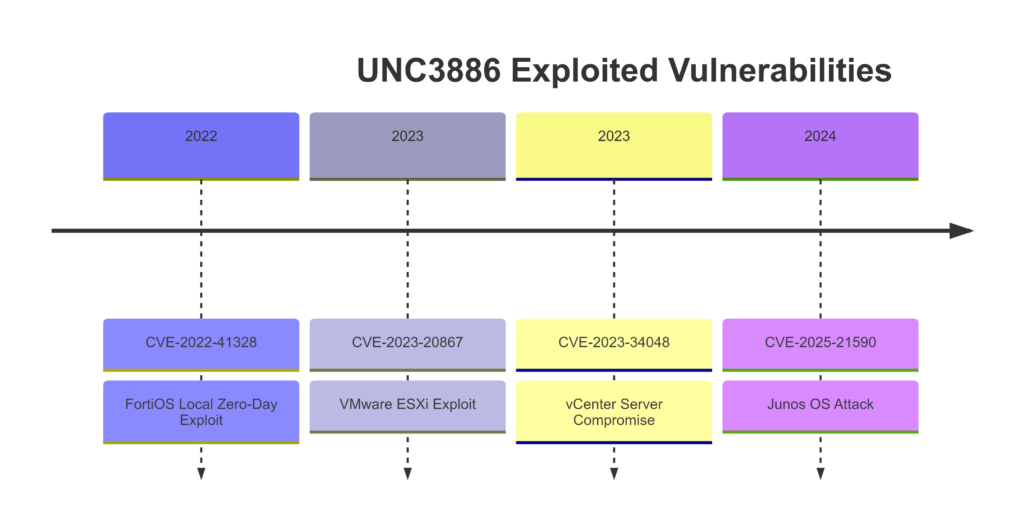
In mid-2024, the China-linked cyber espionage group “UNC3886″ initiated a sophisticated campaign targeting end-of-life (EoL) Juniper Networks MX Series routers running Junos OS. They exploited CVE-2025-21590, a newly tracked vulnerability that allows process injection to bypass Junos OS security mechanisms such as Veriexec, which is designed to prevent unauthorized code execution.
Leveraging their deep understanding of network device internals, the group deployed custom backdoors based on the open-source TinyShell framework. These backdoors were meticulously designed to maintain long-term, covert access to the compromised routers, including capabilities to disable logging mechanisms on the compromised devices, thereby enhancing their stealth and persistence, underscoring UNC3886‘s strategic focus on persistent espionage.
The campaign highlights a concerning trend wherein espionage-motivated adversaries compromise routing devices, granting them sustained, high-level access to critical network infrastructure. Such access not only facilitates intelligence gathering but also poses potential risks for disruptive actions.
How do UNC3886 operate?
UNC3886‘s operations primarily target the defense, technology, and telecommunications sectors in the U.S. and Asia, aiming to infiltrate high-value organizations for intelligence collection and long-term access. Their ability to maintain persistence within compromised networks suggests a broader strategy of embedding themselves within critical infrastructure, potentially positioning them for further exploitation or strategic cyber operations.
This is not UNC3886’s first use of zero-day vulnerabilities to compromise infrastructure. Previously, they exploited CVE-2023-20867, which enabled unauthorized remote execution on VMware ESXi hosts, allowing them to gain deep access into virtualized environments. Additionally, they leveraged CVE-2023-34048, a high-severity VMware vCenter Server vulnerability, to expand their reach within compromised environments. Their ability to identify and exploit high-impact vulnerabilities before they are publicly disclosed underscores their advanced technical capabilities and suggests an organized and well-resourced effort to compromise key infrastructure.
KrakenLabs observed highlights
Vulnerability
Critical PHP-CGI vulnerability: GreyNoise reports widespread exploitation of CVE-2024-4577, a critical PHP-CGI vulnerability patched in June 2024. Initially observed in attacks on Japanese organizations, the threat has expanded globally, with Germany and China among the most affected regions. Over 1,000 unique IPs have been detected attempting exploitation, and at least 79 exploits are publicly available. Learn more →
Trend
Trojan steals facial recognition: GoldPickaxe.iOS is a new mobile iOS trojan capable of collecting facial recognition data, identity documents, and intercepting SMS. Threat actors would be feeding the stolen biometric data to AI-driver face-swapping services to create deepfakes and then combine those with the ID documents to intercept SMSs. This allows them ultimately to gain unauthorized access to the victim’s banking account. Learn more →
Supply chain
GitHub Action compromised: A supply chain attack on the GitHub Action tj-actions/changed-files compromised 218 repositories, potentially exposing secrets such as GitHub tokens, DockerHub, npm, and AWS credentials. While only a small percentage of the 23,000 projects using the action were affected, some are highly popular, increasing the risk of further supply chain attacks. Learn more →
Emerging threat
Fake document converters: The FBI warns that cybercriminals are using fake online document converters to deploy malware, steal sensitive data, and even install ransomware. Researchers found malicious sites like docu-flex[.]com and pdfixers[.]com distributing malware-infected executables. Some scams use Google ads to spread threats like Gootloader, used to infiltrate corporate networks. Learn more → / and more →
AI-Powered Fake GitHub Repos: New malware campaigns are using AI-generated fake GitHub repositories to distribute SmartLoader, which acts as a loader for Lumma Stealer and other malicious payloads. Disguised as gaming cheats, cracked software, and system tools, these repositories deceive users into downloading ZIP files containing obfuscated Lua scripts that execute malware. Learn more →
Ransomware
Akira exploits webcam: To circumvent an Endpoint Detection and Response (EDR) tool, the “Akira” ransomware group has been observed compromising its victim through a vulnerable IoT device. Through an internal network scan, they identified a vulnerable webcam running a lightweight Linux operating system that supported command execution. Akira then deployed their Linux-based ransomware and, as the device was not being monitored, the security team was unaware of the increase in malicious Server Message Block (SMB) traffic from the webcam to the impacted server. Learn more →
What’s new in Threat Context this month?
Threat actors: M_A_G_A, Suicid, Siphoning Hemlock, barnaul, Magouilleur, LabInstalls, Kzoldyck, Injectioninferno, SilkSpecter, CoderSharp, BlackAPT and more!
Tools: FleshStealer, MintsLoader, Rugmi, Hannibal Stealer, Kematian Stealer, CloudChat and more!
Add threat intelligence to your organization
Outpost24’s External Attack Surface Management (EASM) platform gives users access to threat intelligence powered by our human-led team, KrakenLabs. Get in touch to learn more.
