Introducing Social Media and Data Leakage to Outpost24’s EASM platform
Digital Risk Protection (DRP) lets organizations proactively identify and mitigate external threats that emerge from their digital footprints. This can span public sources as well as deep and dark web channels. DRP is a key element of Outpost24’s external attack surface management (EASM) platform, so we’re pleased to announce two new integrations have been added: Social Media and Data Leakage.
These new DRP modules will help cybersecurity teams to:
- Respond faster to threats and incidents as they emerge on social media.
- Detect leaked documents before they become a problem.
- Protect their company’s reputation and reduce the risk of phishing or fraud.
- Prevent confidential information from spreading by catching issues early.
Combined with the Leaked Credentials and Dark Web modules, Social Media and Data Leakage empowers the Outpost24 EASM Platform with automated threat intelligence data. This level of monitoring enhances customers’ insights into their attack surface and lets them react to external threats quickly. Let’s walk through how each of the new modules work.
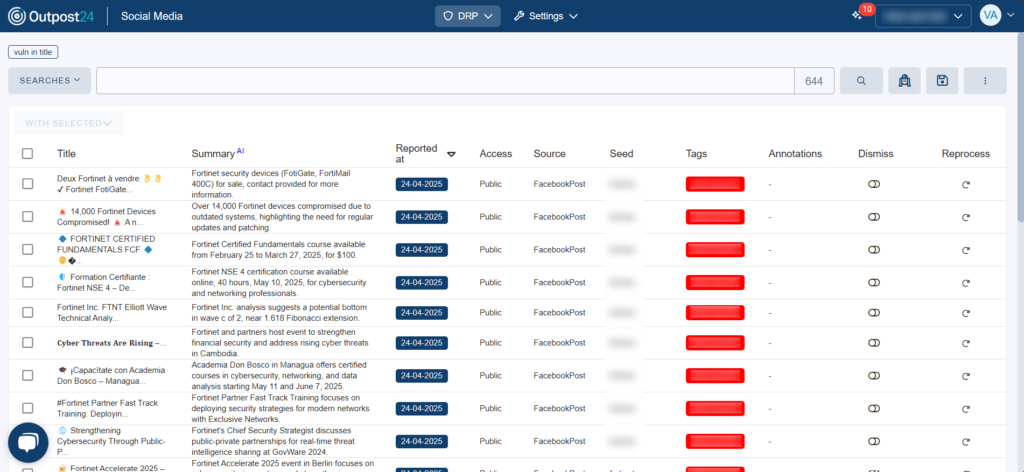
Social media: React quickly to risks
Your organization’s presence on social platforms is part of your attack surface. Threat actors are lurking around, looking to launch attacks against companies, and using information they find on social profiles. Your social media profile is going to be one of the first ports of call for threat actors planning an attack. They may also attempt to impersonate you or your employees on social media, including the unauthorized use of brands, logos, and assets.
Some use cases for Outpost24’s Social Media DRP module include:
- Social media impersonation of senior executives: This tactic is often used by threat actors to launch phishing or scam campaigns. By monitoring your Twitter, LinkedIn, Facebook, and other social media profiles through our Social Media module, you can react to these threats before they materialize.
- Proactive detection of threats: Breaches, leaks, and other incidents and discoveries are often publicized on social media channels first. Having ready access to this information as soon as it becomes available is critical for security teams to be able to react.
- Proactive detection of internal leaks: Sometimes employees share confidential information either by mistake or on purpose in their LinkedIn posts or tweets. Keeping tabs on social media helps security teams notice these potential leaks and react before they become a problem.
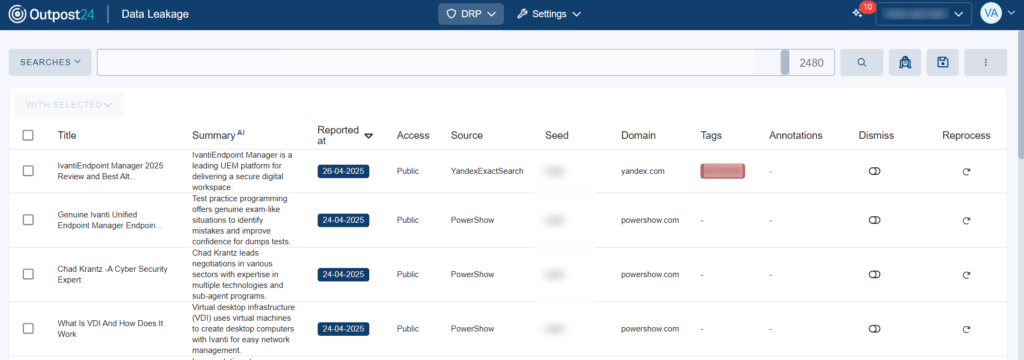
Data leakage: Monitor for serious breaches
Your organization’s sensitive documents are one of the most important assets to protect from the outside world. They contain information on your employees and third parties that are golden targets for threat actors. Equally, your source code could be leaked on the internet, deep web or P2P networks, either intentionally or not.
Some use cases for Outpost24’s Data Leakage DRP module include:
- Detect potentially leaked documents: This is a key pain point for many organizations. Often users use unauthorized or misconfigured applications to share documents with customers or other colleagues, without realizing that the information within could become public domain. The Data Leakage module detects such documents from many sources, including document repositories, and allows you to mitigate the issue.
- Detect potentially leaked source code: Source code is often reused across applications, including authentication information. With our Data Leakage module, we can detect potential leaks related to code, that could reveal potential internal information to an attacker. This could include intellectual property, or even the attached authentication tokens present in the code. The Data Leakage module searches in all main code repositories to detect these leaks and informs you so you can react appropriately.
Threat intelligence expertise and automation
Our Digital Risk Protection modules in the EASM Platform are fueled by exclusive sources and advanced threat intelligence, unique in the market. On top of that, the solution saves you a lot of time by automating the continuous detection of threats and alerting relevant stakeholders.
This is where Outpost24 can make the difference:
- Access to private and exclusive sources: We go beyond just surface-level monitoring. Our platform taps into hard-to-reach and private sources that most competitors can’t access, giving you deeper visibility into potential threats and leaks.
- Strong automation capabilities: Unlike other solutions that require a lot of manual work, our platform automates the detection and alerting process across various threat vectors—reducing analyst workload and accelerating response times.
- Powered by advanced threat intelligence: Our solution is built on top of rich, real-time threat intelligence, enabling more accurate detection, prioritization, and context around each alert.
EASM and DRP combined
The addition of the Social Media and Data Leakage modules completes the extensive Digital Risk Protection integration in Outpost24’s EASM platform. The combination of attack surface data and threat intelligence in a single platform, offers a full overview of external threats and risks facing your organization, empowering prioritization and proactivity.
The Digital Risk Protection modules in Outpost24’s EASM Platform include:
- Credentials: Find actionable intelligence around leaked, stolen, and sold user credentials. We locate them in real time on the open, deep, and dark web, along with information about relevant malware used to steal the information. Outpost24’s sinkholes, honeypots, crawlers, and sensors are continuously searching for your stolen credentials from leaks, on forums, and in real-time from targeted malware. This helps eliminate serious attack vectors and fraudulent actions in minutes rather than weeks or months.
- Dark Web: Boost your awareness of what’s going on in the underground. Get visibility over malicious activities targeting your organization and proactively prevent future attacks. Gain an advantage by putting an eye on the enemy camp: become better informed about criminals targeting your organization; proactively prepare countermeasures.
- Social Media: Monitor and check your organization’s digital footprint across Web 2.0 repositories, including blogs, forums, websites, and social networks. Find websites not authorized to use your brands and assets claiming partnership affiliation assets and more, so you can take proactive steps to shut them down.
- Data Leakage: Discover if your organization’s sensitive documents and source code has been leaked on the internet, deep web or P2P networks, intentionally or not, such as with shared internal documents with poorly-secured file sharing providers.
Get a free attack surface analysis
Interested to get a comprehensive view of your attack surface risks, including leaked and stolen credentials, dark web mentions, social media risks and data leakage? Book your attack surface analysis here.

