SAST, DAST, or SCA: Which is best for application security testing?
According to Verizon’s 2025 Data Breach Investigations Report, there has been a 34% rise in attackers exploiting vulnerabilities to gain initial access and cause security breaches in the past year. As a result, enterprise security teams are looking more closely at how security controls can be integrated to DevOps without impacting productivity.
DevOps is central to delivering new products and driving revenue, which often puts the focus on speed and quality rather than security. However, the rise in application-layer attacks underscores the need to address security earlier in the development process to avoid costly breaches.
The introduction of DevSecOps supports this shift by helping teams embed security in an automated, scalable way that aligns with agile development. But with so many automated security testing tools (SAST, DAST, SCA) on the market, it’s important to understand the differences and when to use each one to ensure robust Application Security.
In this blog we’ll explain the different automated application security testing tools that are commonly used in the agile development cycle, and when you should use them to ensure a secure Software Development Life Cycle (SDLC).
What is the difference between SAST, DAST and SCA?
The most popular application security testing tools businesses implement in their development cycles are Static Application Security Testing (SAST), Software Composition Analysis (SCA) and Dynamic Application Security Testing (DAST). Knowing the differences and when to use them is crucial to enhance your DevSecOps.
Static Application Security Testing (SAST)
As development speed increases and DevOps embrace new agile methodologies and technologies, it’s crucial to identify vulnerabilities early in the software development process. Static Application Security Testing (SAST) supports this need by analyzing source code, bytecode, or binaries without requiring a running application. This “white box” testing approach integrates seamlessly into CI/CD pipelines, enabling fast, automated scans without slowing down development like manual reviews or penetration tests might.
SAST solutions scan code line-by-line to detect common security weaknesses (including those listed in the OWASP Top 10 and the CWE Top 25) during development. By identifying and addressing vulnerabilities early, developers can remediate issues before they reach production. This empowers teams to “shift left” and adopt secure coding practices from the start, building security into the development lifecycle without sacrificing speed.
Advantages of SAST:
| Disadvantage of SAST:
|
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) analyzes applications in their running state, simulating real-world attacks to uncover vulnerabilities from the outside in (known as “black box testing”) . Unlike SAST, DAST doesn’t require access to source code. Instead, it scans live web applications by crawling pages, probing endpoints, and testing inputs and outputs to identify security issues — much like an automated penetration test.
By mimicking attacker behavior, DAST is effective at detecting exploitable vulnerabilities and business logic flaws that may not be visible in static code analysis. However, because DAST occurs later in the Software Development Life Cycle (SDLC), its findings often surface close to release. This can place pressure on DevOps teams to fix issues quickly, potentially creating friction between development and security functions.
Advantages of DAST:
| Disadvantage of DAST:
|
Software Composition Analysis (SCA)
Getting new features out to market fast almost always means developers don’t write all of their own code, instead relying on open-source components to speed up delivery. While this accelerates innovation, it also introduces security and compliance risks that must be actively managed. That’s where Software Composition Analysis (SCA) comes in.
SCA tools scan codebases to identify open-source components, flagging known vulnerabilities, deprecated dependencies, and license compliance issues. This visibility allows DevOps teams to manage security exposure proactively and ensure legal compliance across their software supply chain.
Many modern SAST solutions now include SCA capabilities, working together to detect weaknesses in both proprietary and open-source code. SCA can also extend to containerized environments, scanning images and registries (e.g., Docker Hub) for publicly disclosed vulnerabilities, whether in the base image or hidden dependencies.
With open-source components now found in 97% of commercial applications, identifying software supply chain vulnerabilities early — across cloud and on-prem environments — is essential to minimize application risk. High-profile incidents like the Equifax breach have shown just how dangerous unpatched open-source components can be.
SAST, DAST or SCA? How to choose the best application security testing tools
As we’ve shown in this blog, there are many different options available for addressing application security risks in the CI/CD pipeline, making it difficult to know what’s best to protect your applications. That’s why it’s important to understand how each Application Security Testing (AST) tool should be used across the development lifecycle to optimize your application security controls.
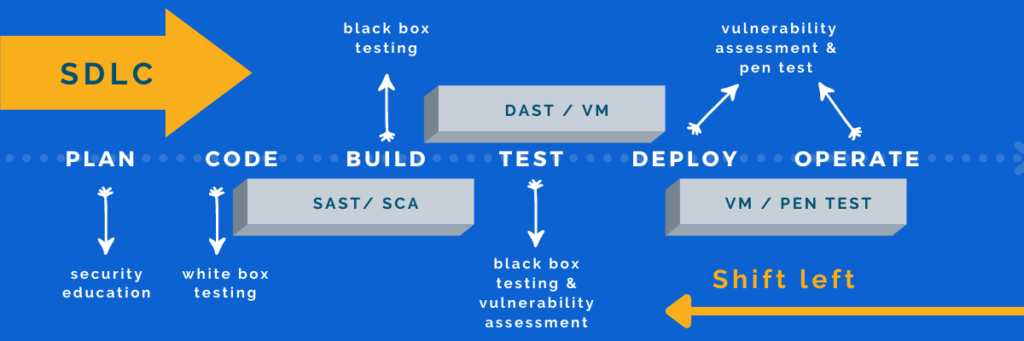
The next step is to align application security testing with your development model.
Commercial-off-the-shelf Applications (COTS)
Commercial-off-the-shelf (COTS) applications and outsourced development offer enterprises a cost-effective, efficient way to meet business needs without building software in-house. However, relying on third-party vendors raises an important question: can you be certain the software is secure before it reaches your environment?
When dealing with critical business applications — especially when source code isn’t accessible — black box testing becomes essential. Techniques like DAST and penetration testing are ideal for evaluating the security of running applications. These methods help identify critical vulnerabilities before deployment and support ongoing monitoring to ensure long-term compliance and protection.
By validating third-party software through external testing, organizations can gain greater confidence in their application security and reduce the risk of introducing unknown threats into their environments.
Internal development and software customization
For businesses who have the resources and infrastructure to create applications in-house, embedding security throughout the SDLC is essential to defend against common vulnerabilities like Cross-Site Scripting (XSS) and more. Security shouldn’t be an afterthought — it needs to be built in from the start.
To achieve true DevSecOps, equip development teams with SAST and SCA tools during the code and build stages to catch security flaws and open-source risks early. Before deployment, apply DAST to simulate real-world attacks and validate application behavior from an external perspective.
After deployment, security efforts shouldn’t stop. Regular penetration testing and vulnerability assessments help ensure that the application environment remains secure with every new release. This layered approach creates a robust security posture that supports both agility and risk management.
Strengthen application security with PTaaS
With cyberattacks on web services continuing to rise, organizations must secure their applications across the entire Software Development Life Cycle. Modern development teams need solutions that support speed, agility, and continuous security, without slowing down delivery.
Penetration Testing as a Service (PTaaS) is a cloud-enabled approach that lets you proactively find and fix application vulnerabilities and protect your digital assets, in both pre-production and production environments.
Outpost24’s PTaaS solution, SWAT, takes this a step further. It blends automated, continuous vulnerability scanning with the depth and precision of manual penetration testing. All results are peer-reviewed and available to view in real-time via our portal, giving development teams immediate visibility and actionable guidance without waiting for static reports or lengthy onboarding.


