The Russia-Ukraine crisis shakes up the cybercriminal ecosystem
Introduction
Since Russia launched a large-scale military invasion of Ukraine on February 24, 2022, many threat actors surged to carry out a wide range of cyberattacks against both sides. Some well-known threat groups have also shifted their attacks or increased their intensity to focus their efforts against Russia or Ukraine. Although the attacks are mainly directed towards these countries, attackers have also targeted other countries playing a significant role such as Belarus or the United States to support the Russian or Ukrainian side. Said attacks usually have a political nature, but the cybercommunity also witnesses the proliferation of opportunistic targeting amidst the chaotic environment of the Russia X Ukraine crisis.
Blueliv analysts have been tracking the state-sponsored, hacktivist groups, and cybercrime threat actors involved in different levels in this conflict. In this article, we will highlight the most relevant threat actors and attacks that took place in late February 2022, categorizing threat actors according to their political alignment. The repercussion of political side-picking certainly has not gone unnoticed: for some groups, such as the famed “Conti” group, it has sparked dire consequences that led to its public exposure. Therefore, the consequences of political side-picking in the underground cyber scenario have not been restricted to attacks against public and private organizations, but they also came in the form of attacks against underground forums and groups.
A rather pressing initial remark is that nation-state activity could be disguised behind the image of hacktivist-style activity, so some newborn hacktivism groups could be actually part of a nation-state false flag operations. Blueliv analysts keep monitoring all analyzed groups and clusters of activity.
Furthermore, we have followed the activity of major underground forums to verify if forum administrators and members have been taking part in the conflict, discussing about it, or deciding not to get involved. The observation of adopted postures in underground forums may provide interesting angles of analysis about threat actors’ behavior patterns, interests, alignment, and activities.
Russian side
UNC1151/Ghostwriter/TA445
“Ghostwriter” is a Belarus-state-sponsored group known for its history of alignment with Russia’s strategic agenda. The group has been conducting disinformation and phishing campaigns since 2017 against NATO-linked targets and on Belarus’ neighboring countries, and since early 2022, Ghostwriter has been conducting different campaigns against Ukraine. In January, Ghostwriter was accused of being responsible for the defacement of multiple Ukrainian government websites.
In February, the Ukrainian CERT accused Ghostwriter of targeting the Ukrainian Armed Forces personnel in a phishing campaign. According to CERT-UA, after the initial phishing emails targeting ‘i.ua’ and ‘meta.ua’ accounts, these accounts are used to send further phishing emails to the email addresses contained in the original accounts’ address books.
Additionally, Facebook’s parent company, Meta, announced on February 26, 2022, that it has seen an increased targeting of Ukrainian individuals – with special emphasis on prominent Ukrainian figures such as military personnel and public figures – by Ghostwriter on its platform. For that reason, the social media company blocked phishing domains used by Ghostwriter from its platforms to enhance users’ security. Meta’s security team has also removed over 40 fake accounts, groups, and pages across Facebook and Instagram for inauthentic coordinated behavior – meaning that these Ghostwriter coordinated accounts aimed to spread disinformation and create a chaotic environment to disrupt the public conversation and perception about the Russia-Ukraine crisis.
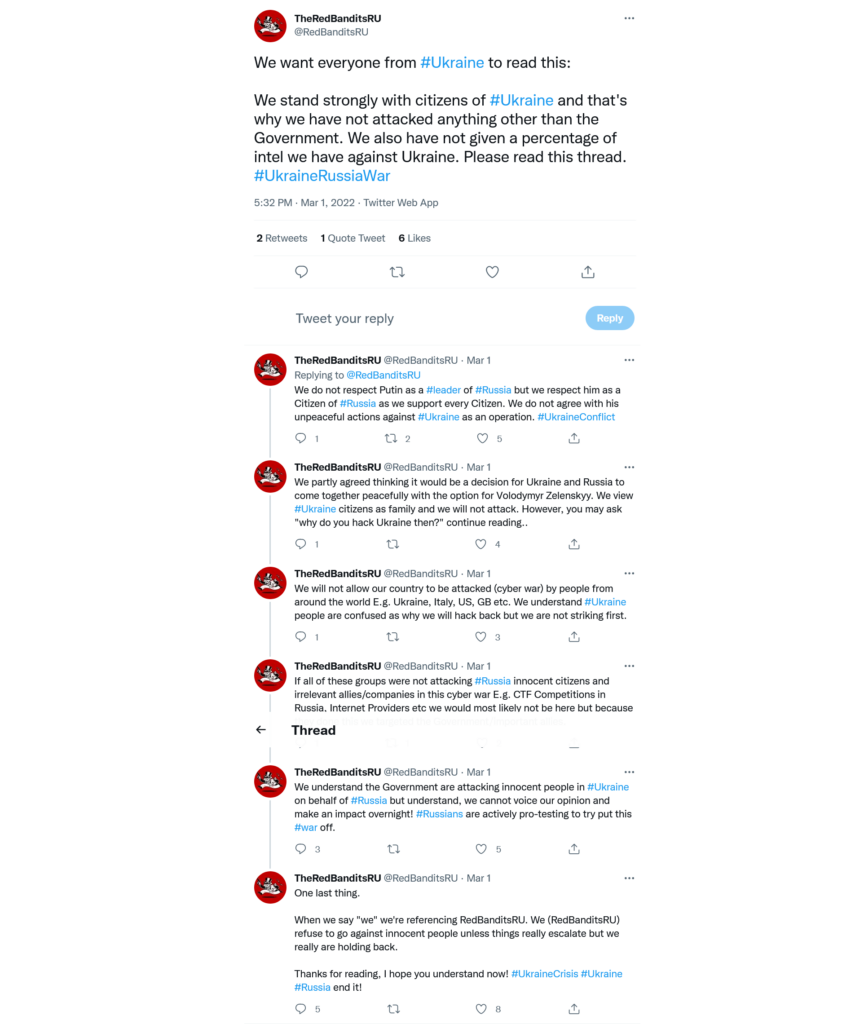
The Red Bandits
“The Red Bandits” is a threat group active on Twitter since February 22, 2022, but as they stated their previous account was deleted, they may have been active for a longer time. They self-describe on their Twitter bio as a “Cyber Crime Group from #Russia” and they have launched several attacks towards Ukraine to support the Russian military. A representative of The Red Bandits told the BBC he wants to “help beat Ukraine from behind my computer whilst they die in the streets” and they are a team of six hackers.
On February 22, 2022, they announced they hijacked the National Police of Ukraine dashcams. On the same day, they allegedly breached into the Ukraine government mailbox and sent some phishing emails to government workers. According to the attackers, they extracted from an unspecified data breach a list of 500,000 emails to target. Furthermore, the threat group has also taken down Ukrainian (.ua) domains with distributed denial-of-service (DDoS) attacks such as the “ca.mil.gov[.]ua” domain, belonging to the Armed Forces of Ukraine.
By March 1, 2022, The Red Bandits provided more information on their political views, positioning themselves against war. However, they justified targeting Ukraine stating the following:
we will not allow our country to be attacked (cyber war) by people from around the world E.g. Ukraine, Italy, US, GB etc. We understand #Ukraine people are confused as why we will hack back but we are not striking first.
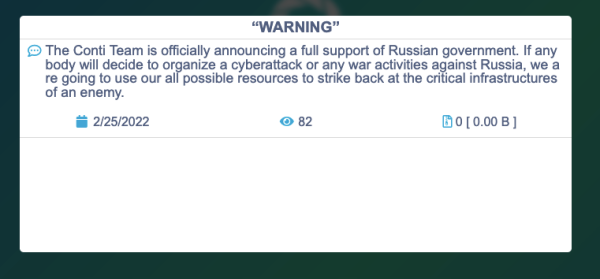
Conti Team
On February 25, 2022, the “Conti Team” announced its full support to the Russian military actions against Ukraine and also threatened to launch retaliatory attacks on critical infrastructures on those who try to organize a cyberattack “or any war activities against Russia.” The original message reads as follows:
This message was followed by another one using milder language and reading as follows:
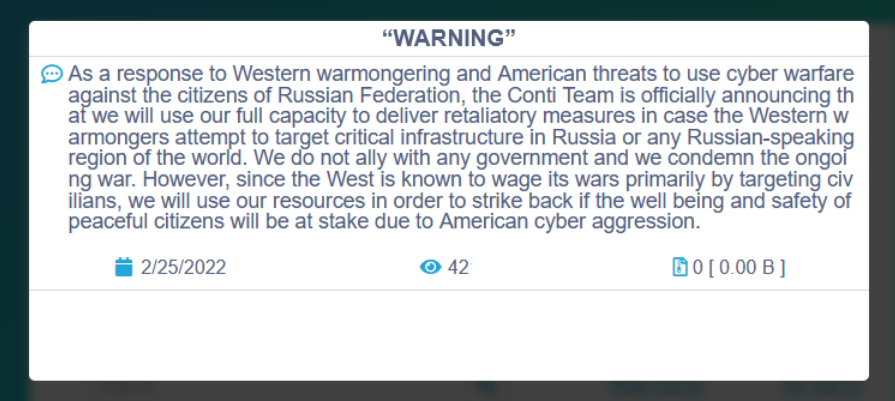
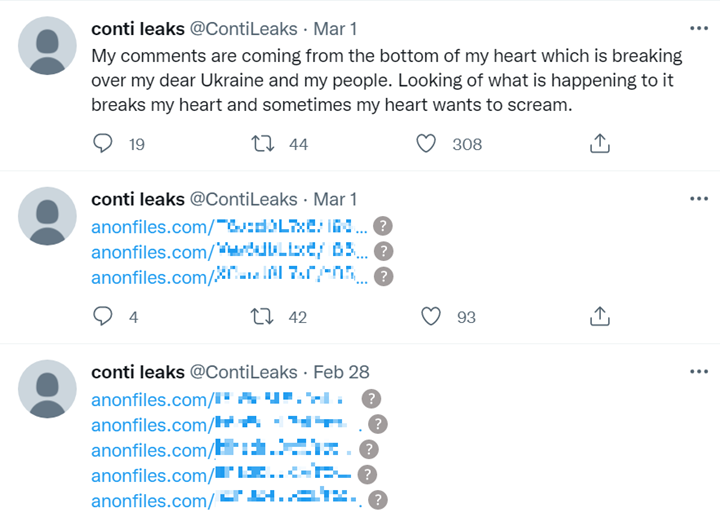
The group’s strong and immediate position received backlash from the underground cybercommunity. Two days later, an anonymous actor with access to Conti’s internal data leaked thousands of files on the web. Since February 27, 2022, the Twitter user @ContiLeaks, whose bio reads “fuck ru gov” and who is probably a Ukrainian national, publish the links for downloading the data – which includes raw files, conversations, structuring, Conti’s source code, amongst others – in their Twitter account. It is clear that the leak is a direct reaction to the ransomware group’s support of Russia in the conflict with Ukraine.
Ukrainian side
IT Army of Ukraine
On February 26, 2022, Mykhailo Fedorov, the Vice Prime Minister of Ukraine and Minister for Digital Transformation, announced they were creating an IT Army, sharing also a Telegram channel dubbed “IT Army of Ukraine“, stating they needed digital talent and they would give tasks to anyone willing to participate.
The first post on the Telegram channel provided a list of domains to be targeted with the message “We encourage you to use any vectors of cyber and DDoS attacks on these resources.“. These domains belong to Russian business corporations, banks, and governmental organizations. They also shared a list of news resources, YouTube channels, and bloggers that allegedly spread false information about the conflict, and asked supporters of the IT Army of Ukraine to flag the YouTube videos.
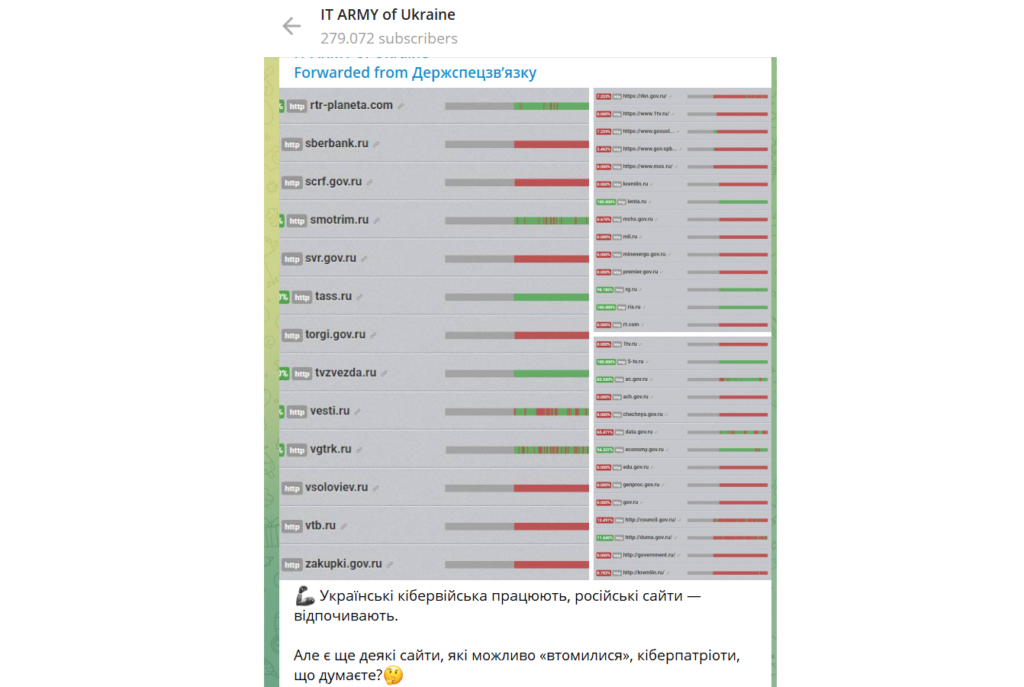
After they shared the targeted domains, they shared the following screenshots showing that a lot of Russian websites were down, likely due to a wave of DDoS attacks. They stated the following:
“Ukrainian cyber-troops are working, Russian sites are resting. But there are still some sites that probably got “tired”, what do the cyberpatriots think?🤔”.
Apart from Telegram, they manage the Twitter handle @ITarmyUA, which shares news updates on military operations, cyberattacks, etc., often using the hashtags #Anonymous and #OpRussia. It is interesting to note the Twitter account was created back in August 2018, although it has been inactive until Ukrainian officials announced the creation of the IT Army of Ukraine. Blueliv analysts could not find any previous mention to the account before February 2022.
Anonymous
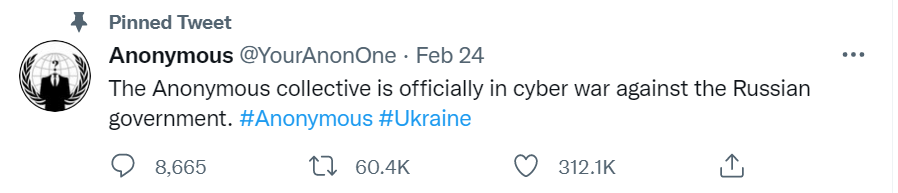
The popular “Anonymous” collective has been one of the first prominent to take a side in the conflict between Russia and Ukraine. On February 24, 2022, Anonymous declared via Twitter that they are officially in cyber war against the Russian government.
Additionally, representatives of the collective posted on RaidForums that they would be launching an offensive operation named #OpRedScare, which, alongside humanitarian aid operation #OpUkraine, aims to support the group’s task in favor of Ukraine.

On Twitter, they have mainly adopted the hashtag #OpRussia (Operation Russia) to spread their ideas, share targeted domains or IPs, and show their attacks, typically sites taken down with DDoS attacks and defaced websites with a manifesto.
The collective has been claiming the authorship of numerous attacks in the past week – from the Russian government’s websites taken down to infrastructure attacks – however, some of these have been also claimed by other groups and actors. While some groups have been partnering with Anonymous, some others have been vocal about their dissatisfaction with the collective’s behavior on claiming authorship for attacks not conducted by them.
Belarusian Cyber Partisans
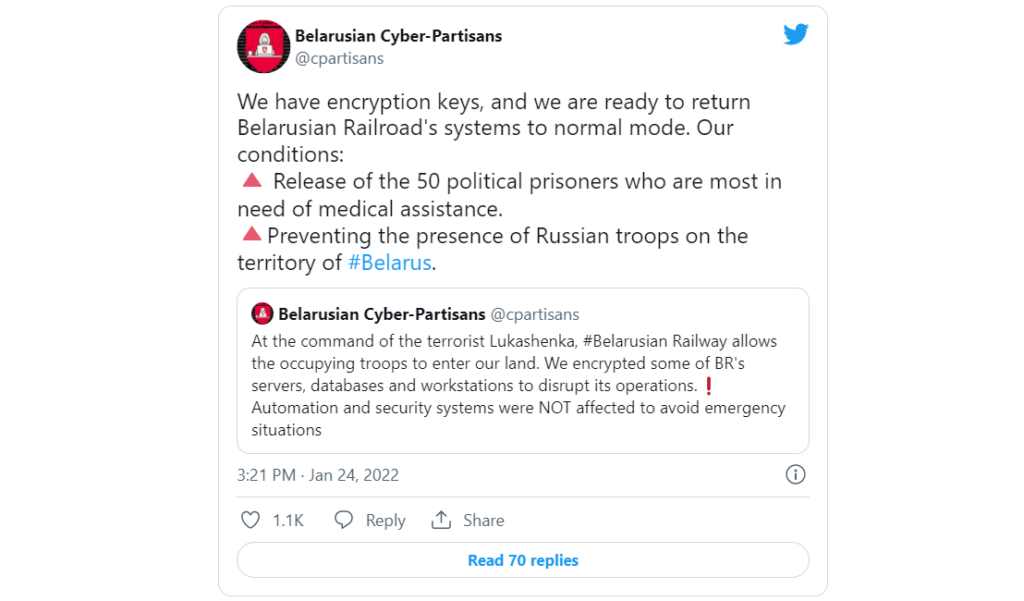
The “Belarusian Cyber-Partisans” is an activist group that has launched a ransomware attack against the Belarusian railway system in January 2022 as a way to raise awareness against the Russian troop movement through Belarus and the country’s President Alexander Lukashenko. This ransomware attack disrupted ticket sales and the railway’s operations, including the majority of the railway’s servers, databases – some of which were reportedly destroyed – and workstations – excluding automation and security systems which were not affected to avoid emergency situations. The group requested the release of 50 political prisoners in need of medical assistance as well as moving Russian troops out of the country. The group’s original post on Twitter reads as follows:
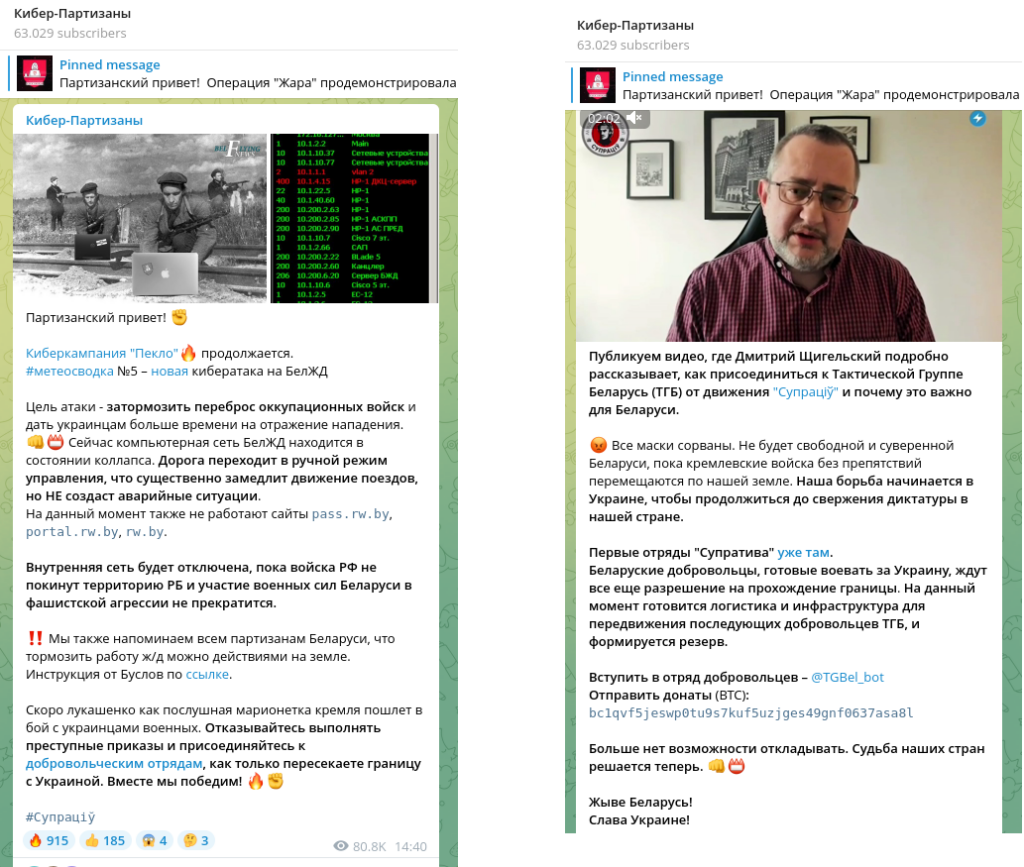
In February 2022, the group launched another campaign called “Inferno” targeting the Belarusian Railway and the Community of Railway Workers of Belarus in order to “slow down the transfer of the occupying troops and give the Ukrainians more time to repel the attack”. Their statement on a Telegram channel reads as follows:
The road switches to manual control mode, which will significantly slow down the movement of trains, but will NOT create emergency situations. At the moment, the sites pass.rw.by, portal.rw.by, rw.by also do not work. The internal network will be disabled until the Russian troops leave the territory of the Republic of Belarus and the participation of the military forces of Belarus in the fascist aggression stops.‼️
The group provided a Bitcoin wallet address to support Ukrainians and urged their followers to become volunteers of the Tactical Group Belarus (TGB) from the Supratsi movement.
Belarusian volunteers ready to fight for Ukraine are still waiting for permission to pass the border. At the moment, logistics and infrastructure are being prepared for the movement of subsequent TGB volunteers, and a reserve is being formed. Join the volunteer squad.
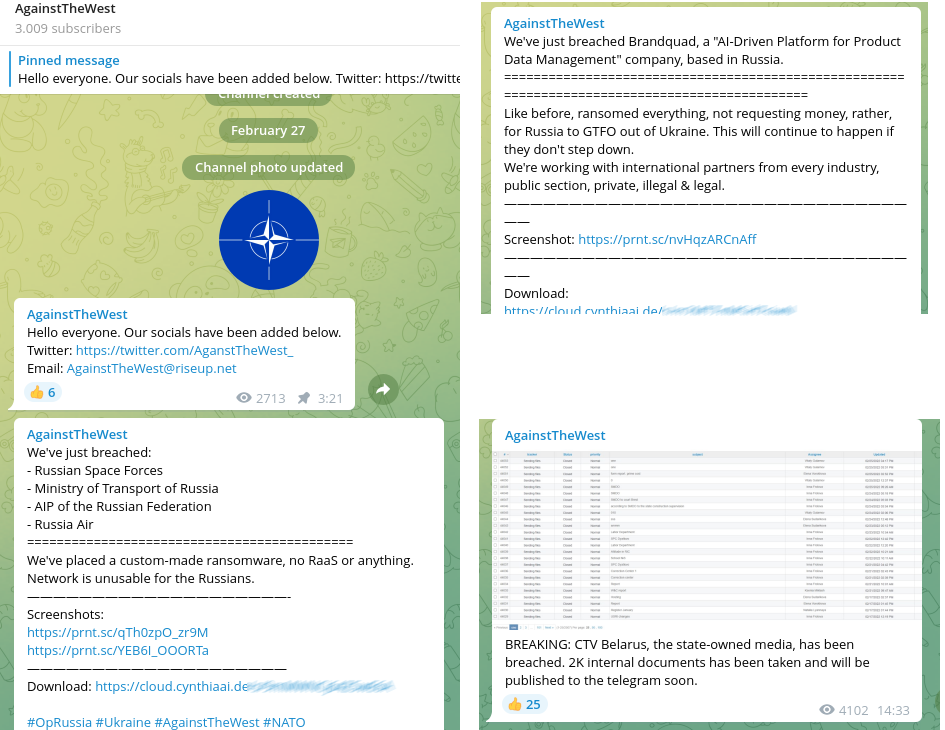
AgainstTheWest (ATW)
“AgainstTheWest” is a malicious threat actor group that has targeted Chinese public and private organizations. It has been active since at least 2021 and it is allegedly a pro-Taiwan hacktivist group and one that is passionately against human rights abuses.
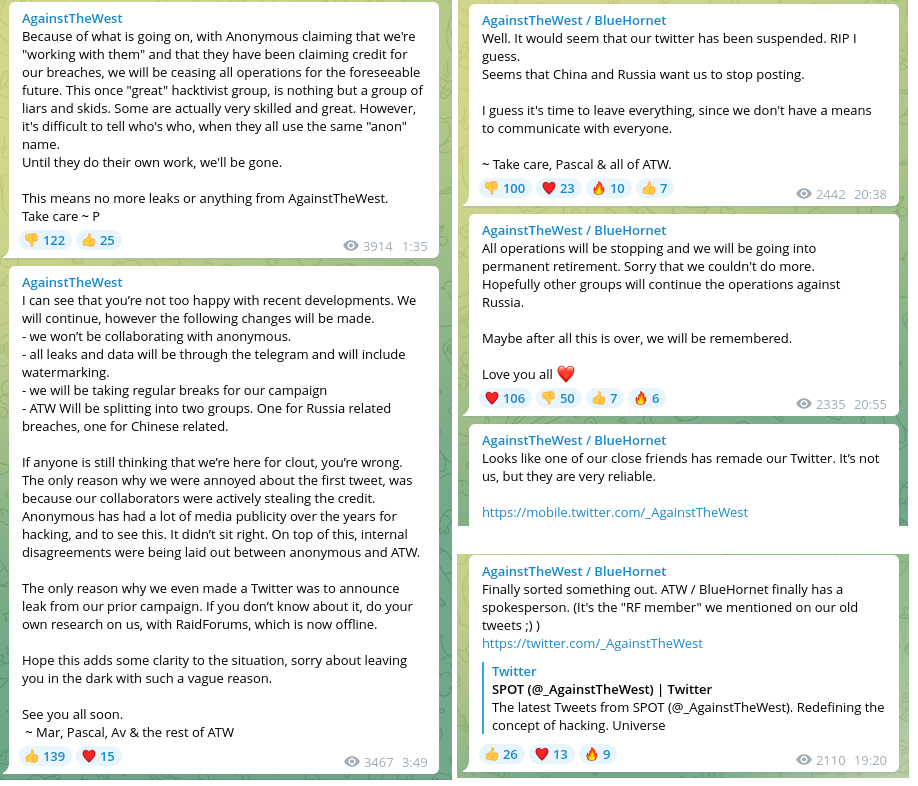
Given the group’s previous activities, it comes as no surprise that they have started to also attack Russia to support the Ukrainian resistance in the ongoing conflict. ATW have re-emerged on Twitter on February 27, 2022, and also posted on their Telegram channel that they have breached the Russian Space Forces, the Ministry of Transport of Russia, AIP of the Russian Federation, and Russia Air but also private organizations such as Brandquad and the Belarusian state-owned media called CTV Belarus. They also announced their collaboration with international partners from “every industry, public section, private, illegal & legal”. While starting as a resistance against China, the group stated that it now has two divisions – one that is concerned with attacking China and one – Russia. However, from a post on March 2, 2022, on their Telegram channel, it becomes clear that ATW are not happy with “Anonymous” taking credits for breaches, and for this reason, ATW decided to step down.
On March 3 and 4, 2022, the group stated on their Telegram channel that “Pascal”, the main member of the team has decided to stay a rebranding and will be the only one operating it. The actor also added that some name will take place and suggested “HornetTag”, “Wasps”, and “Blue hornets” as possible new names. They also commented on Telegram that they would begin posting their messages and activities on a forum supposedly called ‘Darknet World’ which was suggested to be the “alternative to Raidforums right now”.
Network Battalion 65′ (NB65)
The “Network Battalion 65’” (abbreviated as “NB65”) is a new hacktivist individual or group that surfaced on Twitter on February 26, 2022. They claimed to support the Anonymous hacktivist collective in their operations with the following Twitter post:
#Anonymous is not alone. NB65 has officially declared cyber war on Russia as well. You want to invade Ukraine? Good. Face resistance from the entire world. #UkraineWar.
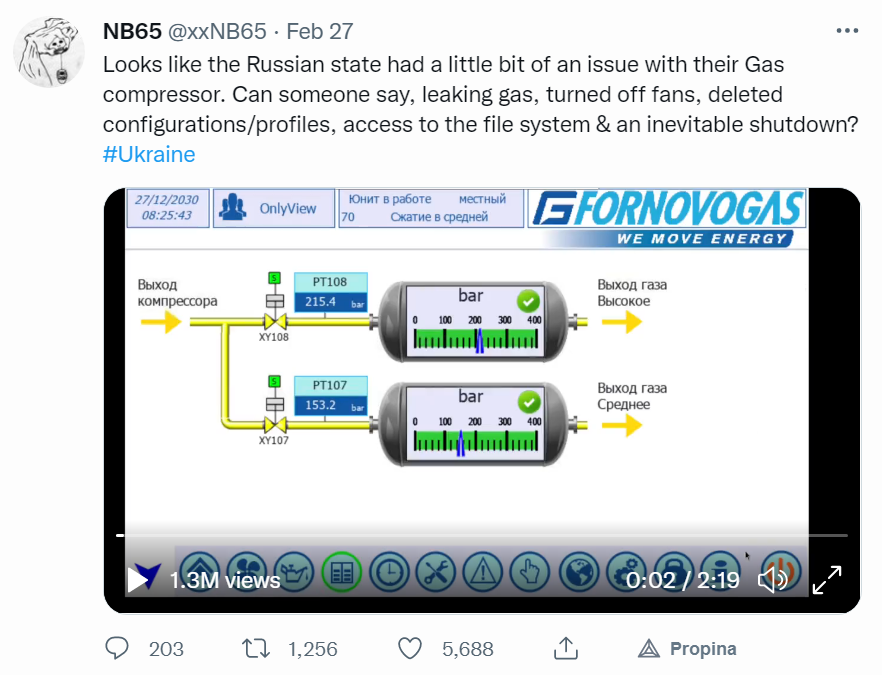
On February 27, 2022, the Network Battalion 65′ claimed they gained access to a gas control system in Nogir, North Ossetia, Russia, manufactured by the Italian firm Fornovo Gas. The impact of the attack has not been confirmed as there is no statement by the affected organization.
They also allegedly breached the Russian Nuclear Safety Institute of the Academy of Sciences (IBRAE), publishing a 2GB leak. The media collective Unicorn Riot analyzed the contents of the leak and although they could not confirm if it originated at the Nuclear Safety Institute, they verified it contained many records on existing businesses and indexes of Business-to-Business (B2B) web servers.
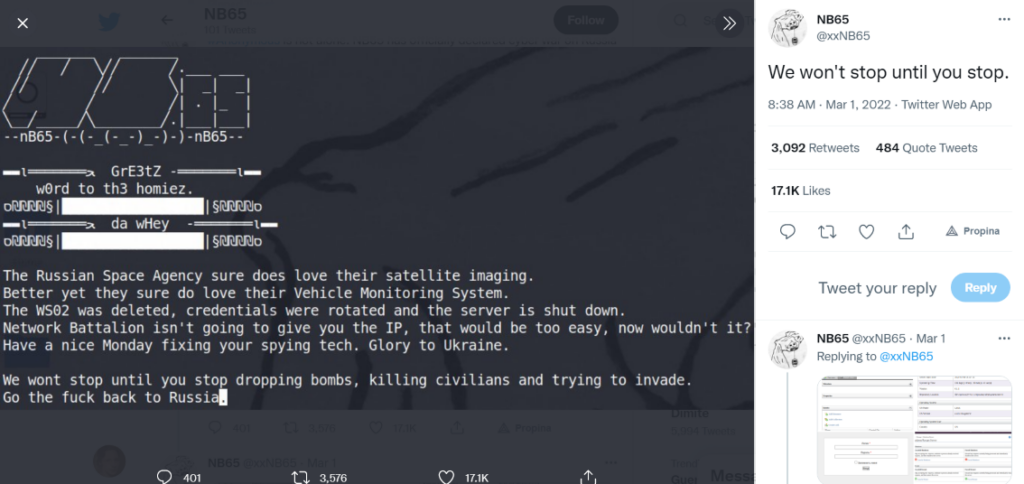
On March 1, 2022, NB65 claimed they accessed the Russian Space Agency Roscosmos, deleted it, rotated the credentials, and shut down the server. However, Dmitry Rogozin, the director general of Roscosmos, denied the attack with the tweet “The information of these scammers and petty swindlers is not true. All our space activity control centers are operating normally.”
Underground forums position
RaidForums
On February 25, 2022, RaidForums’ administrators started a thread in which they condemned Russia’s actions and decided to take actions against Russia-linked users.
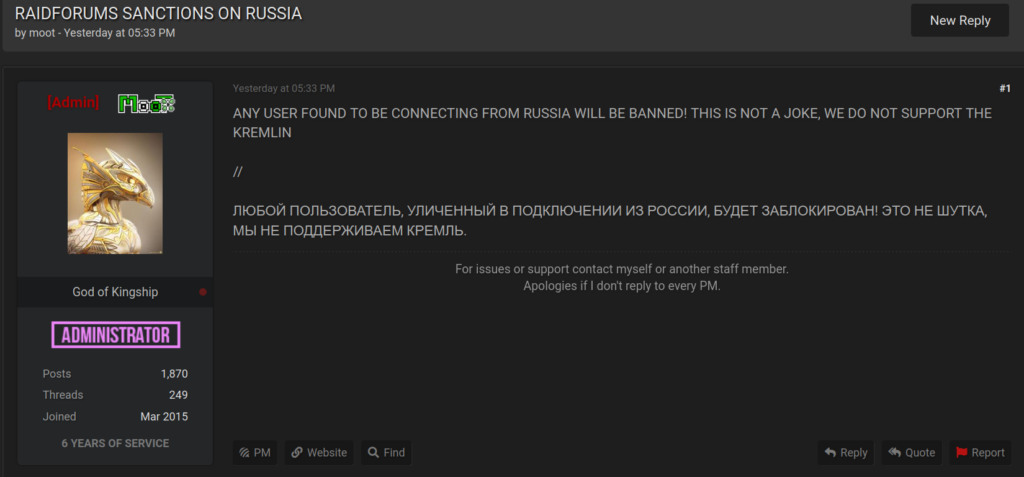
Interestingly, weeks before the start of the Russian military operation in Ukraine, Blueliv analysts observed a more prominent flux of offerings of Ukrainian databases and accesses in RaidForums. This opportunistic inflow of offerings also came along with an increase in the number of new forum members, who probably only registered in the forum to avail of from the vulnerable times to take profit from the situation. However, with the official position taken by RaidForums’ administration team, activities potentially linked to the conflict could have been banned. It could have been the case if RaidForums had not been targeted a few days later. The forum’s domain was seized and a phishing page replaced it. It is yet not clear to the cybersecurity research community what actually happened with the forum, but the timing of the takedown suggests that it may have to do with the admin team’s side-picking in the conflict.
Russian-speaking top-tier forums
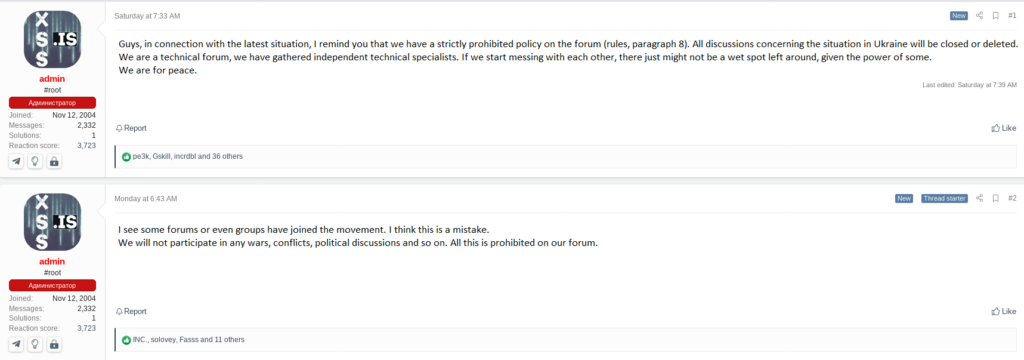
In opposition to the Ukraine-aligned position adopted openly by RaidForums, Blueliv analysts were left wondering about what could possibly be the reaction of the Russian-speaking underground forums, especially top-tiers forums. Conducting research on the main Russian-speaking forums showed us less vigorous positions adopted by forums and forum members in this other part of the underground cybercriminal realm. XSS was the forum that adopted the most emphatic position in regards to the ongoing conflict: following the forum rules disposition, paragraph 8 states that no political discussion is allowed in the forum. Therefore, no discussions regarding the conflict would be tolerated in XSS. Finally, one of the forum administrators states that XSS would not be taking sides and that the forum is a place for technical discussions.
Another interesting public statement was made by the forum representative of the ransomware group “LockBit” on XSS:
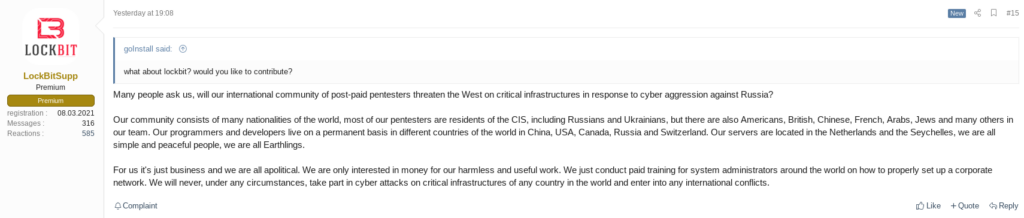
XSS has been the most vocal forum about the conflict so far – even if they have simply emphasized their official neutrality and highlighted the prohibition of political topics in the forum. Other major Russian-speaking forums, such as Exploit, have not been so energetic in this regard – Blueliv analysts could identify a few polite conversations about the topic on the forum. Yet, in Exploit’s forum rules, guidelines are restricted to the prohibition of “the propaganda of racial, national, political and religious hatred”. One hypothesis for the low involvement of forum members in war conversations is that, due to the relevance of Exploit, threat actors may not want to damage their reputation by getting involved in political conversations. Blueliv analysts checked other major forums such as BHF and RAMP, but did not locate conversations about the topic on these forums. BHF has strict prohibiting policies regarding a wide range of political topics, therefore the lack of posts about the Ukraine crisis does not come as a surprise. RAMP, on the other hand, does not have strong policies on the matter, but the conflict does not seem to have sparked conversations in the forum.
The underground scenario so far demonstrates that few forum and forum members are willing to take sides in this political conflict. Ultimately, taking sides could signify becoming targets, and that could have devastating effects on the businesses and security of the forums and its members. Whatever their reasons might be – indifference, a (questionable) sense of ethics, or profit over all matters – the fact is that major forums and its members are not (openly) getting involved in the ongoing conflict.
Conclusions
Nowadays, cyberwarfare plays an important role in wars, supporting traditional military operations with cyberattacks targeting critical infrastructure systems, which are extremely important to maintain access to Internet and phone communications, food supplies, water, energy resources, and more. The displayed Russian capabilities, which include a forceful combination of military and cyber capabilities, result in warfare conduction categorized under the scope of the new types of warfare or non-linear wars. Few nation-states are able to match the Russian combined capabilities and warfare doctrines; therefore, the Ukrainian call for the support of the underground cybercommunity on their cyberwar against Russia does not come as a surprise.
Another important aspect of hybrid warfare are the disinformation campaigns, influencing public opinion with fabricated news, manipulated information, and purposely reporting incomplete or partial information.
Russian nation-state APTs have demonstrated high technical capabilities in both espionage-focused and disruptive operations such as the infamous 2015 attack on Ukraine’s electric power grid attributed to Sandworm, causing a blackout in Kyiv. More recently, suspected Russian state-sponsored activity has targeted Ukraine with data-wiping malware; WhisperGate in January 2021, followed by HermeticWiper and IsaacWiper a month later.
This article aimed to provide information on the main activities and actors in the current cyberwar scenario. Certainly, these are not exhaustive and the scenario is rapidly evolving. The Russia-Ukraine crisis highlights the growing relevance of the cyber domain to geopolitical conflicts: not only military soldiers are fighting wars, but every citizen can take part in the unfolding of political conflicts – for the good and the bad.
References
- Hacktivism and State-Sponsored Knock-Offs | Attributing Deceptive Hack-and-Leak Operations
- Suspected state front FreeCivilian publishes Ukrainian government data after DDoS and wiper attacks
- ‘Hybrid Warfare’: One Term, Many Meanings
- Anonymous hacks Russian website, Linux terminal, and nearly ignites gas control system
- Conti ransomware group announces support of Russia, threatens retaliatory attacks
- Cyber lures and threats in the context of the war in Ukraine
- Twitter Account Belarusian Cyber-Partisans
- Belarusian activists launch ransomware attack in protest of dictatorship, Russian troop surge
- Details emerge on hack of Belarusian Railways and the group behind it
- Twitter Account Belarusian Cyber-Partisans
- Hackers are trying to topple Belarus’s dictator, with help from the inside
- Hacks in Wartime: Railroad & Radio Jamming, Industrial Systems Targeted Amid Russia-Ukraine War
- Roscosmos Head Rejects Anonymous Claim That Russian Satellites Were Hacked
- Russian vigilante hacker: ‘I want to help beat Ukraine from my computer’
- Twitter Account Anonymous Collective
- The Ukraine crisis: how to respond?
- Ukraine suspects group linked to Belarus intelligence over cyberattack
- Twitter Account ContiLeaks

