Cyber Threat Landscape Study 2023: Outpost24’s honeypot findings from over 42 million attacks
What are the most common cybersecurity threats facing your business? The 2023 Cyber Threat Landscape Study provides valuable threat intelligence to help you implement the appropriate security measures against real threats.
The Outpost24 research team is sharing the results of the attack data from a network of honeypots deployed to gather actionable threat intelligence. Here are the key findings from the 42 million attacks that were registered (between January 1 – September 30, 2022):
- Brute force attacks were the most repeated with 73,860 total number of attacking IPs.
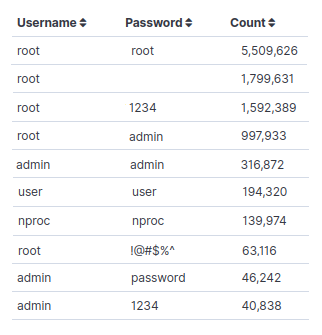
- The default credentials (username: root, password: root) was counted over 5.5 million times in brute-force attempts.
- Port 445 and 22 were the most targeted ports, this correspond to Windows and Linux remote administration services.
A honeypot is a decoy system (computer, network, or software), imitating a real system to attract malicious users, and collect information about how they operate. The collected information allows administrators to develop the right defenses on production systems, like blocking known attack IPs, specific network traffic, and geolocations, as well as understanding how hackers operate within a network and prevent their strategies.
Honeypot distribution
In order to get realistic and unbiased data from our honeypot infrastructure, the Outpost24 honeypots were evenly distributed across the world. This configuration increases the chance of being targeted by different bad actors with varying interests and toolsets. The distribution of the honeypot systems looked like this:
- North America: 3
- Asia: 6
- Europe: 8
- Oceania: 3
Every time one of the honeypots was targeted, the interaction details were processed and stored. This provided us with a daily log of the detected attacks, including: IP addresses, protocols, location of the attack origin, and how the attackers were trying to gain access.
Types of honeypots
The Outpost24 honeypots simulated different system scenarios, ranging from low to medium interaction, including:
- SSH Honeypot: Provides a log of the different shell interactions that an attacker performs on it, including the credentials used for brute force attacks.
- Database Honeypot: Simulates a database management tool to lure attackers to exploit vulnerabilities related to its software or infrastructure.
- Malware Honeypot: Emulates different services such as FTP, SMB or HTTP to learn how an attacker attempts to infect the service. This type of honeypot captures the entire infection process, from the initial malicious requests sent, to obtaining a sample of a specific deployed malware.
- Elasticsearch Honeypot: Mimics the Elasticsearch platform to know which RCE vulnerabilities an attacker can exploit. It also shows how vulnerable the database configuration is and whether it is possible for the attacker to obtain information about its status.
- Web Honeypot: Creates web pages with common vulnerabilities such as local file inclusion or SQL injection. This allows us to record the malicious payloads.
To obtain data from more complex attacks, such as privilege escalation or persistence techniques in a system, high-interaction honeypots can be used to represent an actual exploitable system in a controlled environment.
Analysis of captured data
Brute force attacks
Among the different attacks that have been recorded, one of the most repeated is the brute force attacks, in which the attackers attempt to log into the system by systematically guessing the credentials.
Credentials used in brute force attacks
Analyzing the stored data of the brute force attacks made it possible to analyze the credentials. It is common to find root, admin, and user as the most common username, and password, in brute force campaigns. Not surprisingly, there were also variations with the word password or incremental numbers as the password, indicating that these attacks are mainly after the low-hanging fruit.
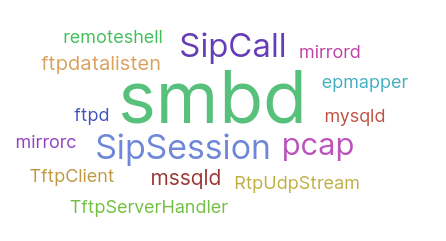
Targeted protocols
Honeypots can also collect information related to scanning services, malware samples or the actions taken in vulnerable web applications such as path traversal attacks. There are services that may be more vulnerable to be attacked than others, therefore, it is not surprising that service scanning is another of the actions that our attackers have executed the most. By analyzing the registered targeted ports, it was found that among all the attacks, ports 445 and 22 were the most common. In addition, it was also discovered which services are most exploited by intruders, with the SMBD filesharing protocol on top of the list.
Honeypot attack map
Attackers often use VPNs to conceal their real IP addresses. Yet, it is still interesting to analyze IP addresses to identify attack patterns, and the locations frequently used by attackers – whether real, or not. The top 5 countries with the most attack attempts registered against our honeypots are:
- Russia
- United States
- China
- Vietnam
- Germany
Actionable threat intelligence with Outpost24
Honeypots provide valuable information to administrators and developers, enabling them to model the behavior of their adversaries, and apply the necessary security measures to deal with real threats. For example, with the extracted credentials it is possible to apply password policies that block the use of vulnerable credentials, and decrease the chance of a successful login attempt.
Developing a network of honeypots, tailored to mimic a specific environment, with the goal of gathering actionable threat intelligence, is resource intensive – to say the least. With Blueliv Threat Compass by Outpost24 you can easily identify the latest cybercriminal trends, and threats relevant to your organization.