GraceWrapper: TA505’s post-exploitation enabler
Since its inception almost a decade ago and the MirrorBlast campaign, the threat actor group known as TA505 has continued to plague the financial, retail and restaurant sectors. Learn more about the GraceWrapper post-exploitation enabler and how its detection evasion technique works.
Be it selling compromised network access to malware operators to launching some of the most notorious spam campaigns in recent memory via the Dridex banking trojan, TA505 has proven time and time again that it is not content with its success as it continuously eyes the next big prize.
During its tenure, the group is believed to have ventured into ransomware operations. Most notably, it supposedly teamed up with the equally notorious ransomware-as-a-service group, the Locky gang, to distribute the destructive Trick banking trojan.
The group hasn’t slowed down since – in fact, it has gotten increasingly sophisticated and challenging to identify thanks to a vast and diverse array of tactics, techniques and procedures. Its most recent spam campaign, dubbed MirrorBlast, was launched at a wide range of industries and supported by a slew of new tools in the form of updated KiXtart loaders, the MirrorBlast loader itself, Rebol script stagers and a new and improved FlawedGrace RAT.
We took it upon ourselves to inspect the convoluted code and quickly discovered a new anti-detection component belonging to the Grace family. This new component, which we have dubbed GraceWrapper, appears to hinder RAT detection while also facilitating post-exploitation tool deployment in infected machines.
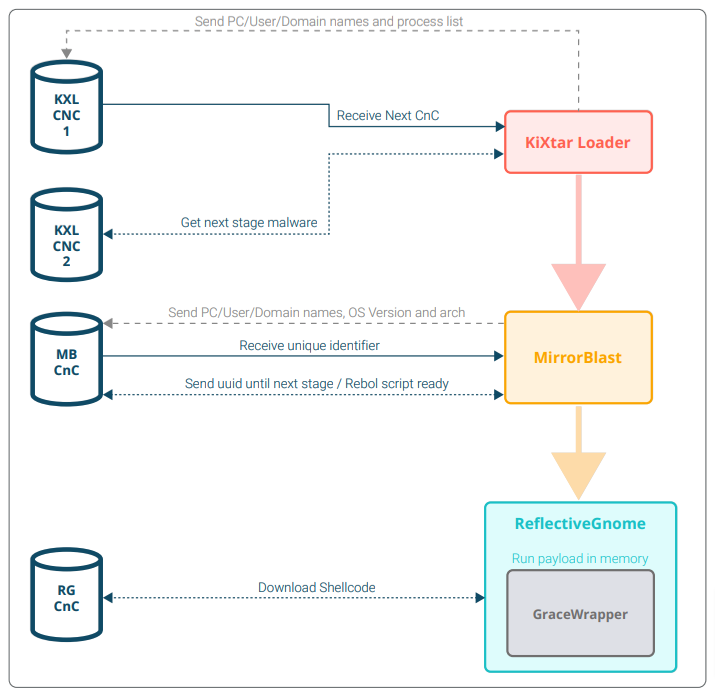
To better understand the latest member of the Grace family, we re-analysed the structure and technicality of the group’s MirrorBlast campaign as we studied the anti-analysis techniques (sleep function), obfuscation tactics, injection mechanisms, sleep functions and other surprisingly advanced functions present in the new component. We began to identify how TA505 was able to use its new downloaders to bypass detection systems and disguise the attribution of its attacks.
Our deep dive has proven that TA505 has not wavered in its mission to improve its intrusion techniques, protect and hide its tools and avoid the watchful eye of analysts and automated detection solutions alike. In doing so, the group has positioned itself as a strong enabler for post-exploitation tasks and a viable threat to modern businesses.
Not only has our research helped us pinpoint how long the Grace family has been in active development by the group, but it has provided sufficient insights and evidence to suggest that new and improved versions of the malware exist and are potentially active in the wild, right now.
