The use of Fast flux to hide phishing and malware delivery websites
Fast Flux is a technique that was seen for the first time in 2007 – and that is still used today -which allows attackers to resist dismantling, the ability to hide the true command and control servers, phishing sites, malware or clandestine markets, and take on possible countermeasures and censorship.
The technique works by changing the DNS records of type A for a given domain very frequently. To accomplish this, the DNS record is given an exceptionally low TTL (time to live) so that the servers do not cache the domain. Usually, two or more IP addresses per domain are used to improve availability.
This technique is often used by malware creators in botnets and phishing sites and is used both on compromised servers – if they are accessible from the internet or its ports – or servers purchased for this purpose. Its main function is to serve as a reverse proxy to hide the real destination of the requested resource.
In this post we want to share details about a study that we have carried out on a Fast Flux network operated by the creators of the Ursnif malware. Our main objective is to shed some light on this type of network and what kind of activities are developed within. The domains shown in this post belong to the Ursnif botnet, which at the time of writing is still active thanks to the use of Fast Flux.
Also known as Gozi, IFSB, and Prapas, Usnif is a banking Trojan that among its multiple functionalities performs web injections on banking sites, theft of credentials, intercepts keystrokes, and more. In addition to Fast Flux, Ursnif has also made use of the Tor network and servers have been located on it, but in this post, we will focus on the Fast Flux network itself.
The domains
To better understand the operation of this network and obtain statistical data, we have automated certain processes to obtain the list of IP addresses for each Fast Flux domain. In addition, we have also listed the different operating systems (those that have been identified) and services running on each server, trying to locate common patterns between them. Fast Flux domains list:
- Fuck00001.com
- Vyefb543.ru
- gameclockersd.com
- goodwoodmood.at
- blackpass.info
- thefreshstuffs.at
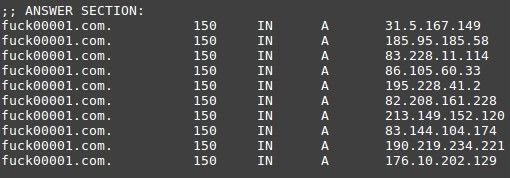
As we can see in the image, the domain “fuck00001.com” resolves to multiple IP addresses. This is quite common and helps to improve the availability and the resistance to failure. In this case, the TTL is configured at 150 seconds, after which the DNS cache is refreshed again to obtain in new IP addresses. Between the domains listed above there are markets dedicated to the sale of credentials and credit cards, also accessible from the Tor network. This can mean one of two things: the group also owns the markets where they sell the extracted data, or they are renting the network to serve other actors IPs. Searching for these markets, we can find other domains serving the same sites, and in this way we can discover new domains inside the network.
- blackpass.info
- blackpasqk3nqfuc.onion
- thefreshstuffs.at
- thefreshstuffs.mu
The proxies
To understand better how the network works, we did an analysis of the network extracting information like operating systems executing the proxy services, the ports opened, and the certificates used by the network.
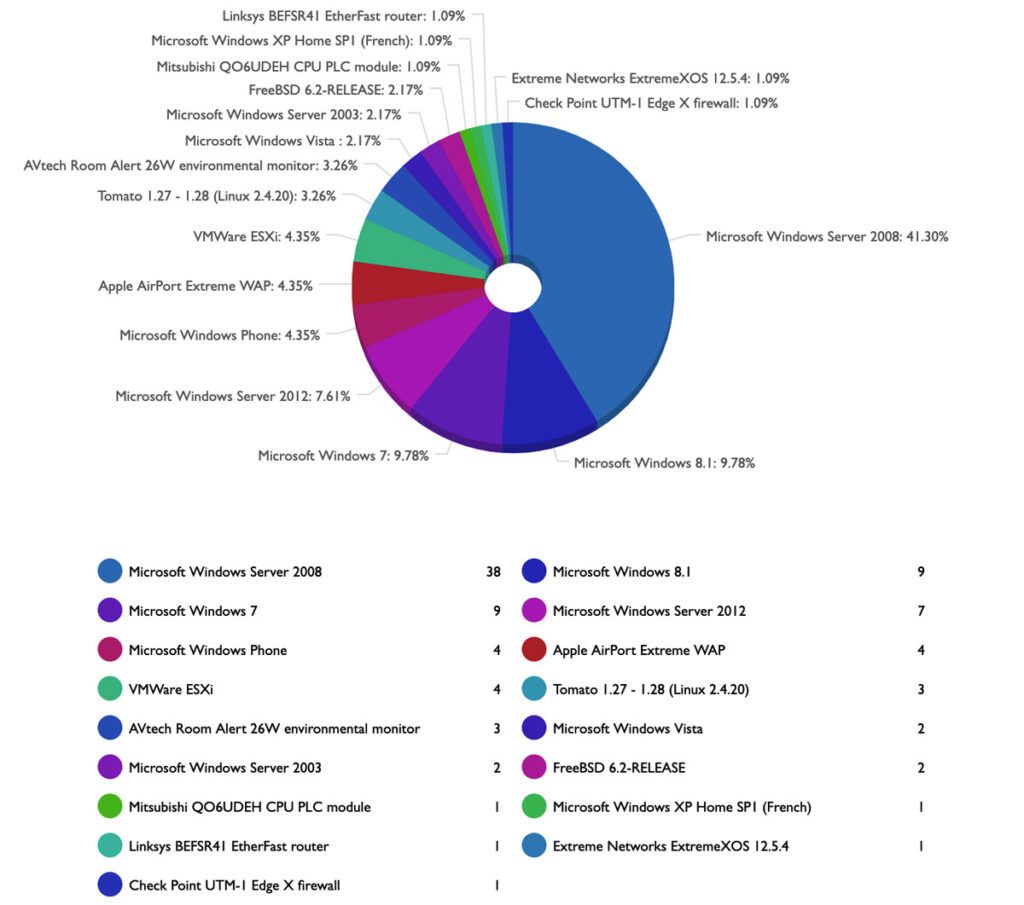
Most of the machines forming the Fast Flux network are Windows. They are probably dedicated / virtual servers that are hired for this purpose. Usually, the servers are rented VPS offered by bulletproof providers that allow their clients to host any type of content or use them to carry out any type of operation regardless of their legitimacy. These kinds of servers made the services harder to dismantle, because the process to be able to interpose an abuse or DMCA report is quite tedious and usually ignored. We also see some other Linux and router OS, because some of the machines conforming to the network are compromised legitimate networks in which the router has UPnP enabled for dynamic port opening through NAT or, in its absence, they perform the needed operations to enable the opening of said ports so that they are publicly accessible via the internet. All this can be observed in the following image, where we have identified almost 155 machines proxying the connection to the domain “fuck00001.com”.
Top identified OS used
Between the machines in the network, the most common ports used by the Fast Flux network are the ports 80 and 443. These ports are used publicly, ,as a reverse proxy service, because they are the most commonly used ports on the Internet for web browsing, and therefore it’s easier for them to go unnoticed. When a request is received at one of those two ports, they are internally redirected to another reverse proxy, creating a mesh of redirects until they arrive to the end node that serves the site. This is how the end node that provides the service is kept hidden, offering greater resistance to avoid being taken down.
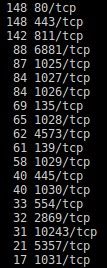
Top open ports used in the Fast Flux network
In the analysis of the ports, we can see port 811, which is quite common in this type of network. Checking the certificates used by the services behind these ports we can see that both 443 and 811 are providing access to the same service, so they perform the same reverse proxy function. On the other hand, the hash of the SSL certificate of port 4573 is different, meaning that it is being used for other things, maybe to control the network, communicate information between nodes, or another function entirely.
In the following images you can see the amount of servers which have the same SHA-1 hashes of the SSL certificates in the different ports:
443

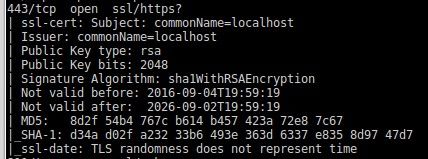
Port 443, and 143 using the same certificate, with details in the second image
811
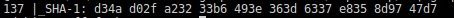
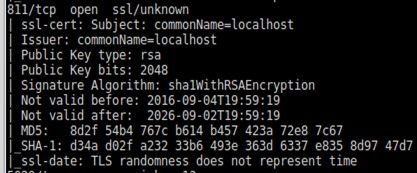
Port 811, and 137 using the same certificate, with details in the second image
4573

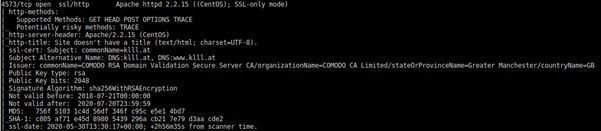
Port 4573, and 58 using the same certificate, with details in the second image
The executable
Based on the Fast Flux domains found and an exhaustive search using the VirusTotal Graph tool, we came across a sample that seemed to be in charge of “dropping” the reverse proxy server that makes up the Fast Flux network.
The dropper performs several checks before installing the reverse proxy. Among them, it checks the hardware it runs on, comparing it to the following list, which is encoded within the body of the malware:
- Common KVM processor
- Common 32-bit KVM
- Virtual CPU
- Intel Celeron_4x0 (Conroe/Merom Class Core 2)
- Westmere E56xx/L56xx/X56xx (Nehalem-C)
- Intel Core 2 Duo P9xxx (Penryn Class Core 2)
- Intel Core i7 9xx (Nehalem Class Core i7)
- Intel Xeon E312xx (Sandy Bridge)
- AMD Opteron 240 (Gen 1 Class Opteron)
- AMD Opteron 22xx (Gen 2 Class Opteron)
- AMD Opteron 23xx (Gen 3 Class Opteron)
- AMD Opteron 62xx class CPU
It creates a new service that is run by svchost without any injection, but letting the system load it as another service that runs in this process. As a result, tools like autoruns do not show the service by default (to change this behaviour, it is necessary to enable the option “show Microsoft entries”).
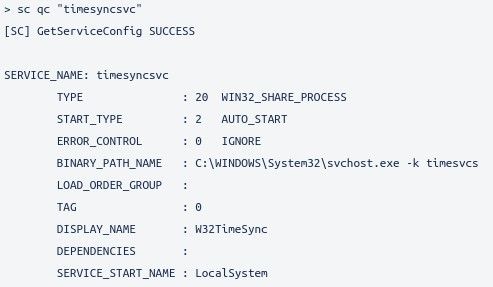
Output of “sc” command requesting information about “timesyncsvc” service.
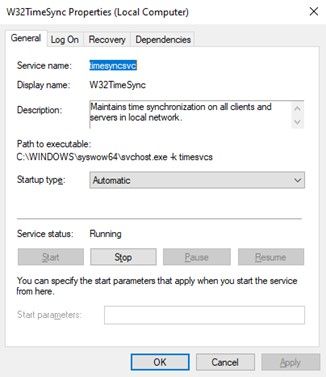
“timesyncsvc” service properties
The DLL that Windows loads in svchost is well disguised under the path: C:\Windows\System32\timesyncsvc.dll
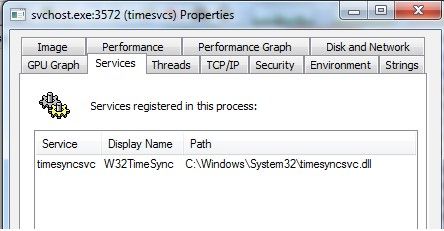
“timesyncsvc” service location path
On a related note, among the encrypted strings that are embedded in the binary, we have found some references to cryptocurrency mining. They take advantage of the computing power of the server (compromised or not) to obtain economic profit:

Opening to the Internet
The reverse proxy needs ports 80 and 443 to be accessible from the internet. To do this, it uses the UPnP protocol to open ports dynamically through NAT or by establishing the infected host in the DMZ. The process is as follows:

UPnP/DMZ flow chart
- It starts the service discovery process using SSDP on UPnP-based networks.
- If it finds a router and manages to open the ports, it performs a test to determine if the ports it has opened are accessible via the internet.
- In case it cannot find UPnP devices, it tries to access the router in the following IP addresses and activate UPnP or DMZ:
- 192.168.100.0
- 10.0.0.0
- 10.0.1.0
- 10.10.1.0
- 172.16.1.0
- 172.16.16.0
- 10.10.2.0
Some thoughts
Despite being an old technique, as we have already mentioned, Fast Flux is highly effective and resistant against censorship and improves availability and resistance to failures. It is a technique that is seen and used in botnets, but that can perfectly be given a legitimate use, contributing all its benefits to other legal projects. The list of domains belonging to this Fast Flux network is available in our intelligence tool to combat and establish the appropriate countermeasures within your organization. A new objective marked in our roadmap is to know the true final destinations where all requests for a given domain are redirected in the Fast Flux network, so that we can dismantle said network and obtain information on all the data that passes through it for our cyber threat intelligence tool.
IOC
| Domain | fuck00001.com |
| Domain | vyefb543.ru |
| Domain | gameclockersd.com |
| Domain | goodwoodmood.at |
| Domain | blackpass.info |
| Domain | thefreshstuffs.at |
| Domain | klll.at |
| SHA-1 Certificate fingerprint port 443 and 811 | d34ad02fa23233b6493e363d6337e8358d9747d7 |
| SHA-1 Certificate fingerprint port 4573 | c805af71e45d89805439296acb217e79d3aacde2 |
| SHA-256 Dropper | eb6f33269cd3232a43ad1bc9f82f205630308e80836a07bbb6f7471a60f96830 |
The list of routers that the malware tries to access to open ports through NAT / DMZ is very varied. Some brands of routers and the corresponding paths are listed below:
| BRAND | PATH |
|---|---|
| D-LINK | /Advanced/Network.shtml /post_login.xml/adv_network.php/ui/dboard/security/dmz/ui/dboard/settings/management/upnp |
| MOTOROLA | /goform/login /goform/advanced/dmz |
| TECHNICOLOR | /advanced/dmz.asp /advanced/options.asp /status/system.asp |
| TP-LINK | /userRpm/DMZRpm.htm /userRpm/UpnpCfgRpm.htm |
| DRAYTEK | /cgi-bin/v2x00.cgi /doc/MNATDMZ.htm |
| COMTREND | /scdmz.html /upnpcfg.html |
| ZYXEL | /rpUPNP.html /rpFirewall.html |
| SAGEMCOM | /DMZ.asp |
| ACTIONTEC | /advancedsetup_upnp.html |
| AMPER | /webconfig/upnp/upnp.html |
| COMTECO | /access/access_upnp.htm /advanced/adv_nat_dmz.htm |
| NETGEAR | /UPNP_upnp.htm |
| ARRIS | /fw_acl.html |
| HUAWEI | /html/security/firewall.asp /html/security/setcfg.cgi /html/application/upnp.asp /html/application/dmz.asp |
| ZTE | /getpage.gch /getpage.lua |
| THOMSON | /cgi/b/games/cfg/? |