Belsen Group: Analyzing a new and ambitious threat group
On January 14th, 2025, Belsen Group emerged in the underground forum Breach Forums publishing a list of sensitive data extracted from vulnerable Fortinet FortiGate devices. Since then, they have expanded their malicious activities into acting as initial access brokers. Who are they and what do we know about them? In this blog we’ll give you the lowdown on an ambitious new threat group to be aware of.
Key points
- “Belsen Group” is a newly emerged threat actor specialized in publishing sensitive data from compromised devices particularly targeting Fortinet FortiGate firewalls
- Their operations involve leveraging vulnerabilities to extract data, which was initially freely distributed. This is possibly as a tactic to establish credibility and notoriety in cybercriminal circles
- In late January 2025, the adversary started to pursue financial gain by offering the allegedly stolen data for sale
- In early February 2025, the gang expanded their malicious activities and started to sell network access to high-profile victims
Introduction to Belsen Group
“Belsen Group” focuses on compromising and leaking sensitive network infrastructure data, particularly from Fortinet devices. Initially, they aimed to gain attention by releasing data for free but have since shifted to a monetized model. Their motivations appear to be both notoriety and financial gain. They communicate their activities on platforms such as X (formerly Twitter), Telegram, and dark web forums.

First Fortinet FortiGate leak
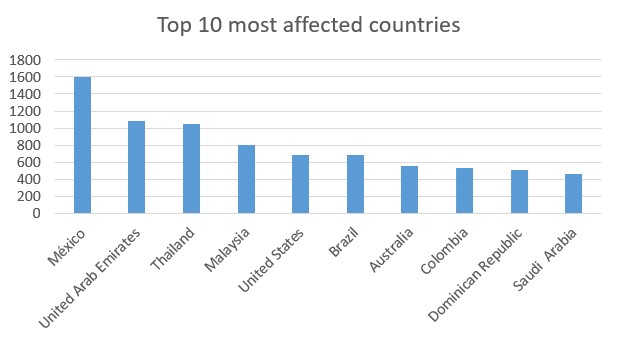
In January 2025, Belsen Group published sensitive data for over 15,000 FortiGate firewalls. The leaked data (dating back to 2022) includes plaintext VPN credentials, device configurations, and IP addresses, organized by country.
The data leak contains information from more than 158,000 users from 145 different countries, including corporations from different economic sectors including finance, technology, and defense.
Potential exploited vulnerability CVE-2022-40684
Kevin Beaumont connected the mentioned leak to CVE-2022-40684, an authentication bypass vulnerability exploited as a zero-day in 2022, which coincides with Fortinet analysis conclusions. A subsequent Censys scan revealed that, on January 17th 2025, 8,469 (54.75%) of the affected devices remain online, and 5,086 (32.88%) continue to expose login interfaces, increasing the risk of further exploitation.
Financial motivation
Initially, the data was freely distributed on their dark web site and promoted in underground forums but eventually transitioned to a pay-per-access model. On January 22nd 2025, the group announced on X that due to high demand, the data would no longer be freely available.
Instead, it would be sold on the regular internet for $100, with purchase instructions provided via Telegram. This shift signals their intent to monetize their operations while maintaining visibility in both the dark web and public platforms.
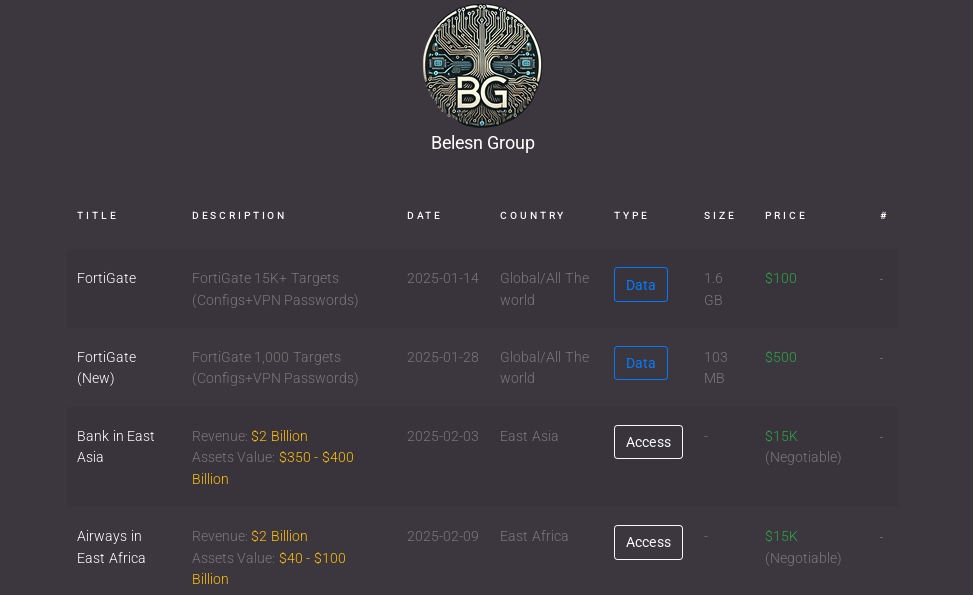
This new approach towards financial gain was confirmed on January 28, when the malicious actor announced on their dark web site a new leak affecting an additional 1000 FortiGate devices, on sale for $500.
Becoming an initial access broker
On February 3rd 2025, Belsen Group announced on their website and in the social media platform X that they would also start commercializing network access, announcing as their first sale the access to an undisclosed major bank in East Asia for $15,000.
A few days later, on February 9th 2025, the gang announced a remote control access (RCE) to a major airway company in East Africa also on sale for $15,000.
Based on the adversary’s activities and evolution, Outpost24 KrakenLabs analysts consider Belsen Group a significant emerging threat actor for 2025. We will continue tracking their malicious operations.
Stay safe from threat groups like Belsen Group
Learn how the Outpost24 platform keeps your organization safe from the list of exposed Fortinet VPN credentials discussed in this blog (and much more!). Get in touch to speak to an expert.

