How to master pen testing in an agile environment
Problems arise when teams are too siloed. In the past, organizations ran into trouble when Development teams would hand over finished code with security problems to IT Operations to deploy and manage. They realized it was faster and more effective to work together throughout the product lifecycle in a DevOps model, picking up on issues and resolving them as they went in an agile way of working.
We can apply the same logic to pen testing. Testing web application security shouldn’t be a static or siloed process – and it certainly shouldn’t be an afterthought. However, traditional pen testing methods don’t neatly lend themselves to an agile way of working. Pen testing as a service (PTaaS), gives organizations a way to overcome these challenges and continuously pen test their critical web applications to a high standard.
Challenges of pen testing in agile environments
Agile testing means integrating pen testing into the development cycle, instead of thinking about it as a distinct phase. However, continuous, iterative testing isn’t possible with traditional pen testing models. You can gain snapshots into problems and vulnerabilities at a given moment, but before long those findings could be out of date. It’s also hard to know if issues have been fixed until you carry out a new round of testing later.
Speed, flexibility, and collaboration between teams are key principles of agile working, which can be at odds with traditional pen testing. Security testing can be resource-intensive, time-consuming, and involves waiting for people with specialized skills to deliver feedback at specific times. This can hamper efforts to find defects in the code early and then continuously monitor and remediate security incidents in the production environment.
One way around the problem of static testing is to set up automated vulnerability scanning to pick up issues on an ongoing basis. These tools save manual effort, but they also lack some of the nuance and expertise needed by expert human testers to both detect novel attack vectors and reduce false positives. PTaaS can offer the best of both worlds – balancing the speed of automated scanning with human expertise and judgement when required.
Four benefits of a PTaaS model for agile teams
PTaaS is the delivery of on-demand manual pen testing and continuous security monitoring to keep your applications secure – no matter how often your production code changes. It’s ideal for agile teams for four key reasons:
1. Real-time reporting
A problem with traditional testing is that by the time the testers have been onboarded, work has been completed, and when the report has finally been handed over, the code can be almost out-of-date. This can then create uncertainty around code changes due to the older findings. As you can see in the below example from Outpost24’s PTaaS solution SWAT, PTaaS offers a faster experience, showing vulnerabilities in an interface that’s updated in real time. Developers can see vulnerabilities from day one and are able to prioritize issues, keeping track of solved problems and new ones arising.
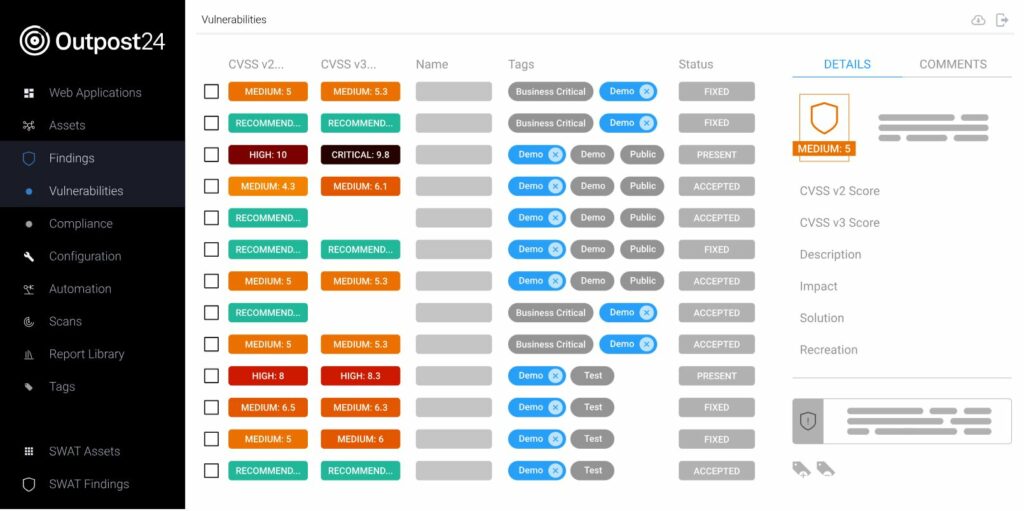
Image caption: Outpost24’s PTaaS platform interface
2. Fast remediation feedback
At the end of a traditional pen testing cycle, organizations receive a static PDF report listing vulnerabilities to remediate. Developers can address these issues, but it might be some time before the next pen test is completed to verify results. This is especially time-consuming if new vendors must be found and onboarded. Even with an existing vendor, new tests have to be arranged and scheduled.
With PTaaS’ real-time reporting and feedback, bugs can be found and remediated throughout the development cycle with instant feedback into whether remediation has been successful. In the spirit of agile best practice, it’s better to catch and resolve vulnerabilities earlier in development, before code ends up deployed.
3. Less need for vendor rotation
One of the most time-consuming aspects of traditional pen testing is onboarding new vendors. Some organizations believe rotating vendors is worth the cost and hassle, as different testers have different specializations and areas of expertise. Therefore, one testing company might pick up on a vulnerability that a previous one missed. PTaaS can make up for this by offering a larger pool of testers, ensuring a fresh perspective. There experts are always on standby to dig into problems when required.
4. Collaboration and communication
Automating processes saves time and costs, but manual tests by human experts are invaluable when it comes to creative and in-depth analysis. Critical context is needed to accurately assess potential zero-day vulnerabilities and reduce the amount of flagged false positives. However, customers often must wait until a report is submitted before raising any queries or concerns about findings with traditional pen testers.
With PTaaS, customers get visibility over the whole process and can interact with findings and the testing team in real time. Testers are available to field questions about possible vulnerabilities and the best ways to fix them. This open communication allows for a back and forth, where developers can work more closely with the testers to get issues resolved on-the-go in a way the fits their agile working style.
Combine PTaaS and agile development
Outpost24’s PTaaS solution, SWAT, combines continuous vulnerability scanning with the depth and precision of manual pen testing. All findings are peer-reviewed and available to view in real-time via our portal. This gives agile teams the flexibility, speed, and responsive feedback they need to pen test to a high standard without lengthy waits for onboarding or static reports to be completed. Speak to one of our in-house pen testing experts to learn how SWAT could best fit with your organization.
