Threat Actor Profile – Shathak malware group
Meet Shathak – a threat group tied to malware used in the Russian-speaking underground targeting enterprises across different sectors in the Americas, Europe and Asia
Threat actor profile: Shathak
Known Aliases
- TA551
- Shathak
- GOLD CABIN
- Monster Libra
- ATK236
- G0127
Key points
- Shathak is a threat group known for targeting enterprises with Ursnif and Valak malware that has been active since 2019.
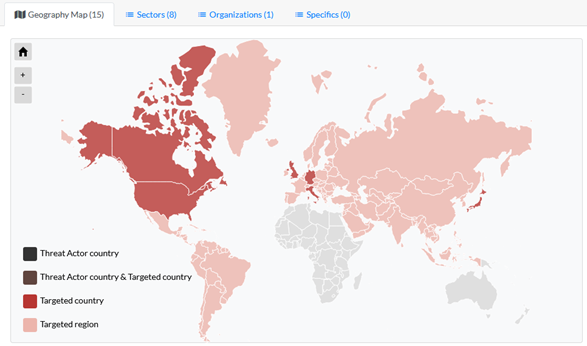
- The threat group has targeted the energy, healthcare, finance, manufacturing and insurance sectors in the Americas, Europe and Asia. · Shathak has used the banking trojan IcedID as follow-up malware after Valak infections.
Deep dive
Shathak is a threat group tied to malware used in the Russian-speaking underground that has been active since at least early 2019. The threat actor group has targeted the energy, healthcare, finance, manufacturing and insurance sectors in North America, South America, Europe and Japan. Shathak has carried out malspam campaigns consisting of phishing emails with an attached password-protected zip file. The zip file contained a Microsoft Word document targeting English, Italian, German or Japanese-speaking recipients with macros to install malware.
The attackers often leverage mailbox data retrieved from previously infected Windows hosts to conduct further spam campaigns, sending the email chain to original senders and recipients, plus an additional comment added to the most recent message providing the ZIP archive password.
The macros mostly generated a URL ending in a .cab file used to install malware. Until April 2020, Shathak deployed Ursnif malware, before they switched to Valak, an information stealer and malware loader. The threat group often uses Valak as a loader to install IcedID or Ursnif to conduct further malicious activities, likely with the object of profiting financially.
Since 2020, Shathak’s IcedID implants have been observed installing ransomware such as Maze and Egregor. According to Proofpoint, Shathak might be partnering with ransomware gangs as an initial access facilitator.
By June 2021, researchers observed Shathak stopped using IcedID in favour of TrickBot, and only a month later shifted to BazarLoader. According to IBM researchers, this usage of tools is the result of the affiliation partnership between the TrickBot Group and Shathak, which aims to distribute TrickBot and BazarLoader. The malware variants are distributed via password-protected files attached to phishing emails. As a further step in the attack cycle, Shathak uses BazarLoader to install follow-up malware such as Cobalt Strike and Conti ransomware.
According to a report from the French CERT and Mandiant, UNC2420 activity shares overlap with Shathak’s. This observation was made after the dismantling of Emotet at the start of 2021.
Threat actor Activity Map
Want to know more? Get a demo of our threat intelligence solution. If you are interested in learning how to access this information as Outpost24 customers, please contact your Account Manager for more details.