Threat Actor Profile – Guacamaya hacktivist group
Meet Guacamaya – a hacktivist group advocating for the indigenous people of Central America
Threat actor profile: Guacamaya
Known Aliases
- alina
- weichafe
- Guacamaya
Key points
- Guacamaya is a hacktivist group acting in defense of the abuse performed on the territory and against the indigenous people of Central America.
- Their main goal is to exfiltrate compromised information from companies or organisms.
Deep dive
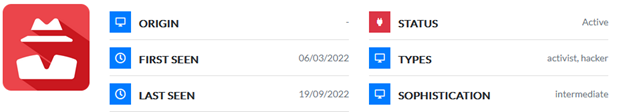
Guacamaya is a hacktivist group acting in defense of the indigenous people of Abya Yala territory. This is the name used by the Native American Guna people who inhabit the geographic region between what is now northwest Colombia and southeast Panama, to refer to the American continent since pre-Columbian times. Their name refers to the most common bird species in Central America. Guacamaya was first spotted on March 6, 2022, after sending a statement to the sharing platform “Enlace Hacktivista” with their presentation and the announcement of their first action against the company CGN-Pronico, which operates the Fenix mine in Guatemala with a history of human right abuses and environmental damage. The following statements done after performing an action have also been shared firstly through this hacktivist platform.
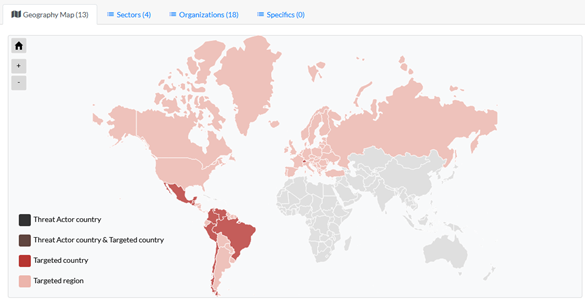
Their main objective is exfiltrating information about companies or organisms performing unjust actions against the indigenous people or territory. To do so, they gain access to the networks with open-source tools, then establish persistence and exfiltrate sensible information. They try to exploit public-facing applications and compromise employees’ credentials with password spraying, phishing, or checking against known breaches, whose emails are often obtained through LinkedIn. Once compromised, the threat group proceeds to download information, such as emails and files. Guacamaya also has a destructive goal since they carry out sabotage actions. Exfiltrated information is publicly shared through Distributed Denial of Secrets, a non-profit whistleblower run by a collective of journalists devoted to enabling the free transmission of data in the public interest, or directly through links in the Enlace Hacktivista platform. Their targets include Colombia’s Attorney General office, Armies of Mexico, Peru and El Salvador, and more recently the drag cartels in Yucatan.
They justify their illegal actions by saying that legality and laws have been invented by a system in which they don’t believe and can’t be accepted in solidarity and resistance
Threat actor Activity Map
Want to know more? Get a demo of our threat intelligence solution. If you are interested in learning how to access this information as Outpost24 customers, please contact your Account Manager for more details.
Other threat actors we’re tracking this month
- “Metador” is an espionage threat group that could be state-sponsored or a contractor offering their services to governments. The threat group is highly sophisticated and employs in-memory loaded custom malware frameworks.
- “Tea Pot” is a threat actor that came into the spotlight in September 2022, when he/she compromised American rideshare and food delivery company Uber. A few days later, Tea Pot breached into Rockstar Games’ Slack server and Confluence wiki, allegedly stealing GTA 5 and 6 source code and assets, GTA 6 testing build.
- “HomeLand Justice” is the threat group that serves as the figurehead for a network of Iranian groups that conducted a chain of attacks against the Albanian government in mid-2022. Because of this series of attacks conducted by HomeLand Justice and other Iranian threat groups against Albania, the country decided to cut diplomatic ties with Iran on September 07, 2022.
- “SiegedSec” is a hacktivist group mainly exfiltrating databases of sensible information of compromised companies and publishing them through Telegram and underground forums.
- “RSC Labs” is an independent company from Italy developing tactical tools for Law Enforcement Agencies, whose activities as a commercial spyware vendor have been denounced by Wikileaks and by firms like Google against the European Commission.
- “JuiceLedger” is a threat actor dedicated to credential stealing that employs a new info-stealer dubbed JuiceStealer. JuiceLedger has been observed compromising credentials through fraudulent applications, phishing campaigns, and compromised or typosquatting PyPI packages.
- “Hadoken Group” claims to be a team of developers and security engineers, and the masterminds behind tools such as Android trojan Xenomorph and dropper GymDrop.