CompassDRP Social Media integration: Six real-world use cases
Social media can work both for and against an organization, so it’s worth treating these sites as extensions of your attack surface. CompassDRP’s Social Media integration continuously monitors both corporate and employee profiles across platforms such as Twitter, LinkedIn, and Facebook. It automatically flags unauthorized or impersonating accounts that mimic executive identities or misuse company branding, helping to thwart phishing and fraud campaigns before they gain traction. Security teams are also alerted the moment breaches or leaks first appear on social channels.
Additionally, it detects accidental or malicious sharing of confidential information by employees in public posts, enabling prompt remediation. By catching these social-media–based threats early, organizations can prevent attackers from exploiting publicly available intelligence for targeted attacks or reputational damage. In this post, we’ll walk through how these use cases work in detail with a real-world example.
How our real-world example works
To walk through a realistic example of how you could apply the power of CompassDRP to your business, we’ve chosen Mercadona, a Spanish retail store. We’ll also use their President Juan Roig, and some key brands (Hacendado and Deliplus). To be clear, we’ve chose Mercadona purely for illustrative purposes and will only show screenshots of publicly available social posts. So the ‘seed terms’ we’ll monitor for in this example are:
- Mercadona
- Juan Roig
- Hacendado
- Deliplus
Use cases we’ll walk through:
- Identifying content related to social media events
- Searching for defamatory content
- Early notifications for boycotts or labor conflicts
- Discovering general controversies or critics with key words
- Detecting fraudulent or uncontrolled accounts
- Notifications around potential cybersecurity incidents
1. Identifying content related to social media events
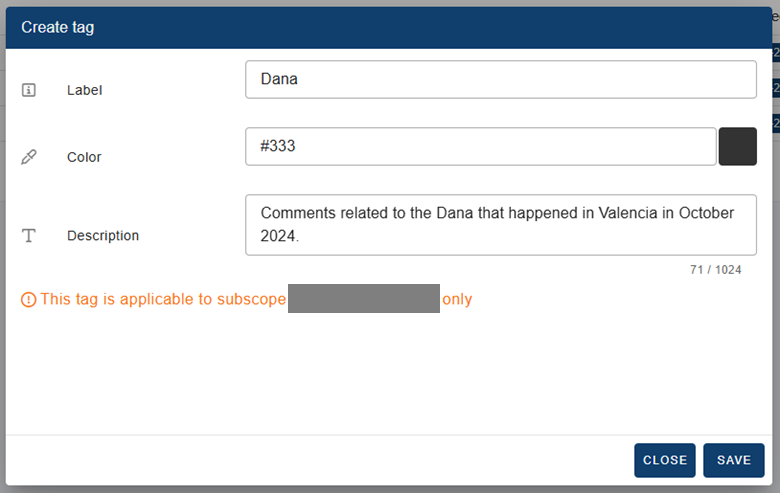
Whenever there is a major event that is going to index a lot of content, we can create a tag in advance for easily identifying those entries related to that event. Fo example, since there has been much talking related to Mercadona and its president after the DANA floods that happened in Valencia in October 2024, we can create an automation rule for adding a tag to all those entries that include the term DANA in the summary.
First, we create the tag:
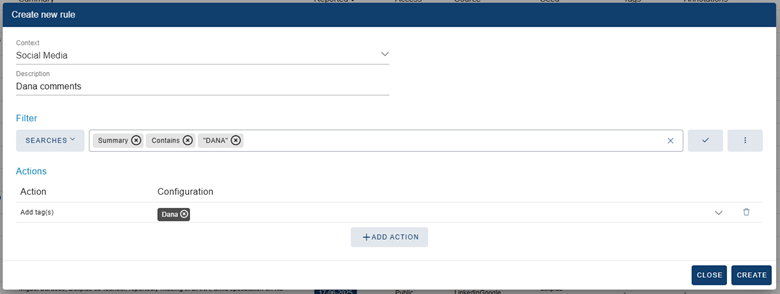
Then, we create an automation rule for the tag to be added to all those contents that include the term “Dana” in the summary:
When a new result shows the tag, we can see it is related to this event we are interested in:
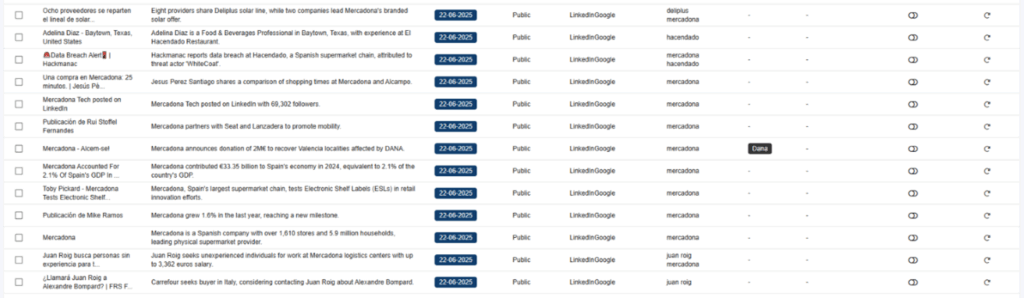
Afterwards, we filter to review only the content that is tagged as Dana and obtain a total of 70 comments:
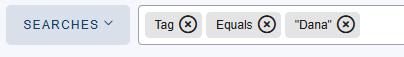
When reviewing this filtered content, we can see some positive content related to the donations made by the president Juan Roig to the flood victims. However, we can also find some negative content claiming Mercadona’s employees were forced to work during the floods.
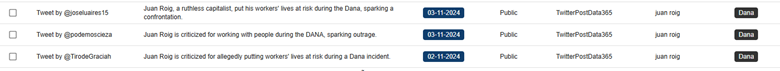

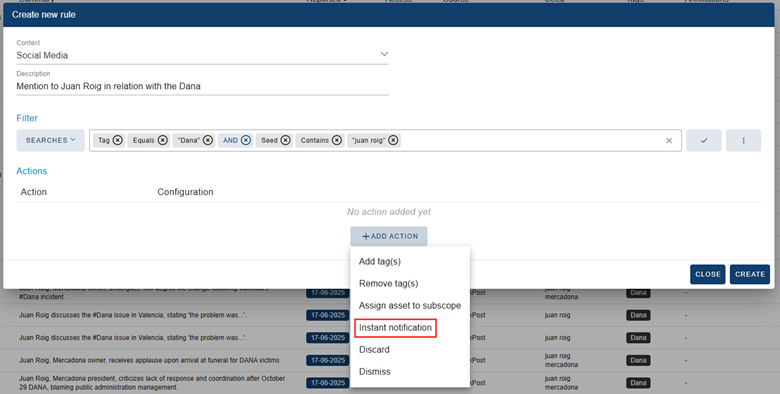
If we decide that this content related to the president and the flooding event are of relevance and must be followed up closely, we can create an automation rule. This will notify us whenever a new comment related to both the tag “Dana” and the seed “Juan Roig” is indexed. Alternatively, if we would like to see the implications of the event solely on the company and brands, we could choose to exclude posts that mention the president’s name.
2. Searching for critical or defamatory content
Depending on the company’s sector, we can create different searches specific to the kind of defamatory content they would be interested in. In our example, Mercadona is a supermarket chain, we might want to look for users criticizing the company’s products or the quality of their providers quality. Accusations that could signal potential health risks would be especially important to stay on top of. Let’s say: cautious, hazardous, risk, concerns, concern, & contamination.
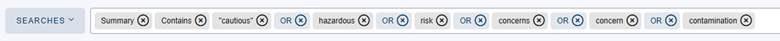
In this case, by identifying keywords mentioned in the summary section, we were able to reduce the volume of entries we need to review from 3,747 to 60. After manually reviewing the content, we reduced them by even more, to 40 of particular interest. Some examples found would be:

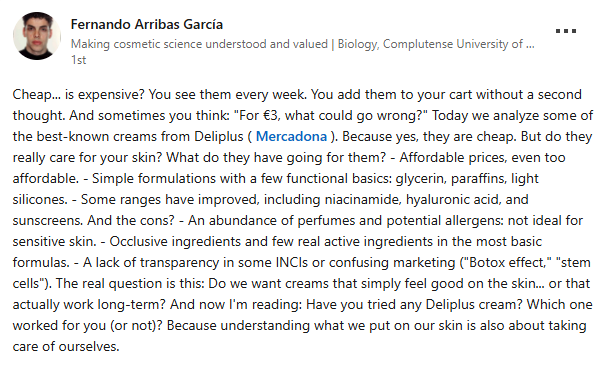

3. Early notifications for boycotts or labor conflicts
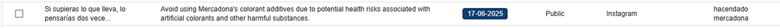
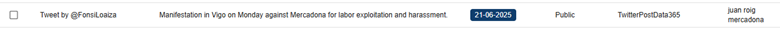
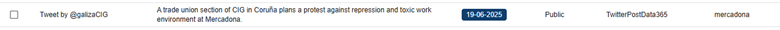
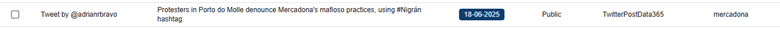
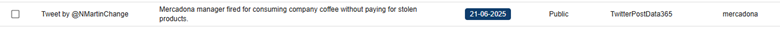
We can create a search for key words within CompassDRP related to open calls for boycotts or that point to the existence of a potential labor conflict or an activist action. The keywords we’ve used for this example include: disruptive, disrupt, outage, fire, fired, boycotts, boycott, exploitation, sues, sue, protest, protesters, activist, activism, hacktivism, hacktivist
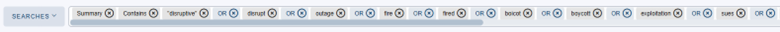
In this case, by identifying some key words mentioned in the summary section, we were able to reduce the volume of entries to review from 3,747 to 133. After manually reviewing the content, we reduced them even more, to 71 of interest. Some examples found would be:



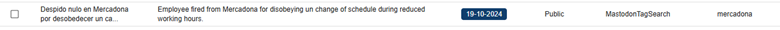
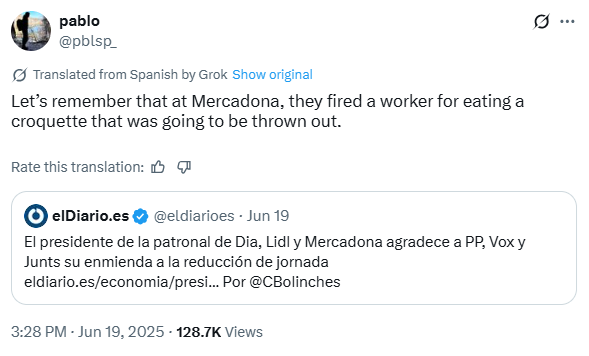
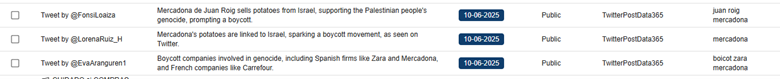
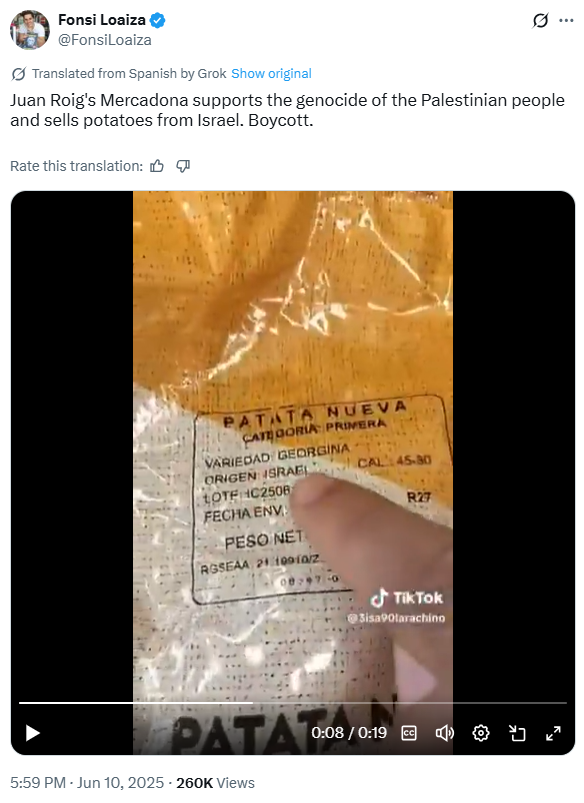
4. Discovering general controversies or critics with key words
We can use CompassDRP to identify general criticism of the company and its brands by searching for specific words. In this example, we’ll search for: dislike, disappointing, disappointment, controversy, criticizes, critics, criticism, criticized, discontent
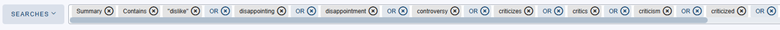
In this case, by identifying some keywords mentioned in the summary section, we were able to reduce the volume of entries to review from 3,747 to 120. After reviewing the content, we reduced them even more, to 106 of interest. Some examples found include:
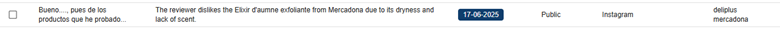
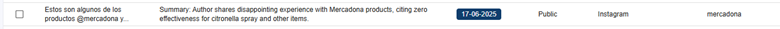
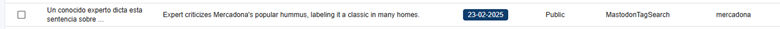
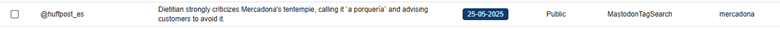


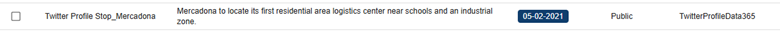
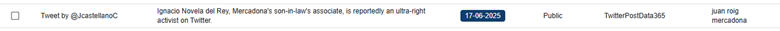
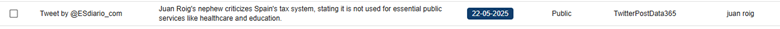
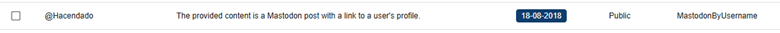
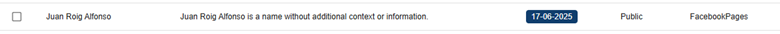
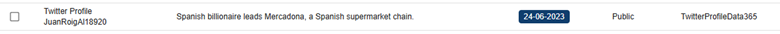
5. Detecting fraudulent or uncontrolled accounts
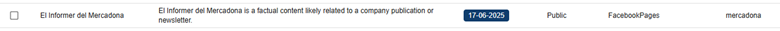
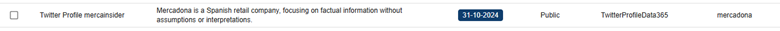
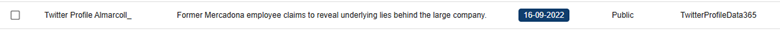
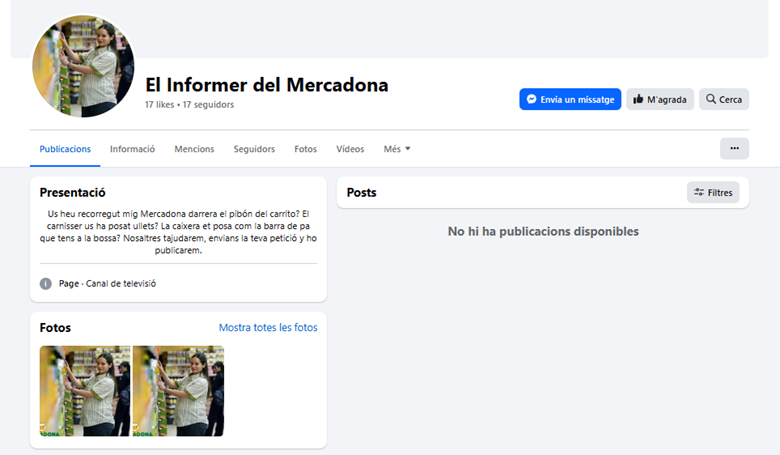
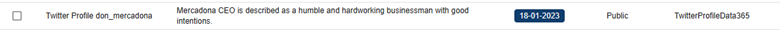
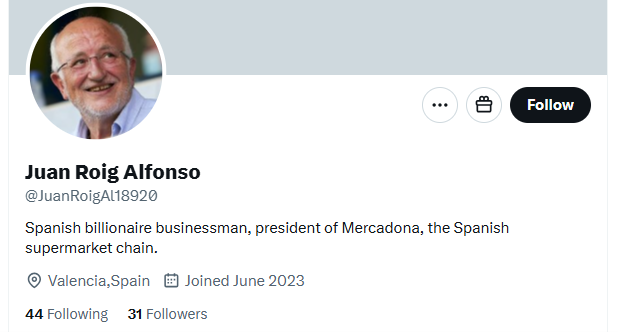
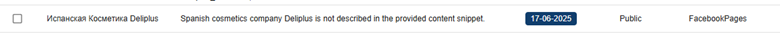
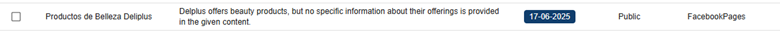
The CompassDRP platform also allows you to find fraudulent accounts in different social media platforms like Mastodon, Facebook, or X. Thes might include the name of the company either in the username or in the description included for the account. So for this example, we’ll search: MastodonByUsername, FacebookPlaces, FacebookPages, TwitterProfileData365

Once identified, analysts can review these accounts and observe the type of content published. From there, you can identify whether the accounts are attempting to impersonate your brand and if they were created with malicious intentions. In this case, the platform retrieved 394 entries, that were reduced to 168 of interest after the analysis. Some examples of interest included:







6. Notifications around potential cybersecurity incidents
In CompassDRP, we can create a search for key words related to public reporting of cybersecurity incidents to detect when such events are covered through social media accounts. In this example, we might use: hack, leak, ddos, defacement, hacktivist, hacker
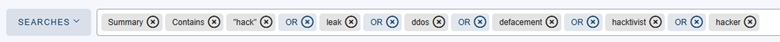
By identifying some key words mentioned in the summary section, we retrieved 8 results, 3 of which seemed to be related to a relevant security incident.
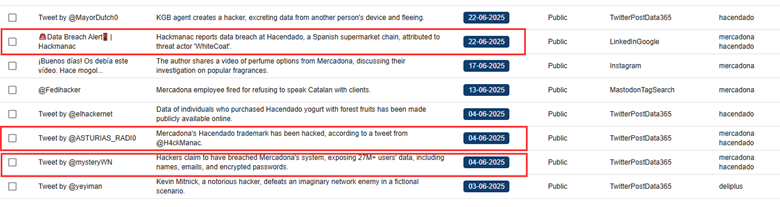
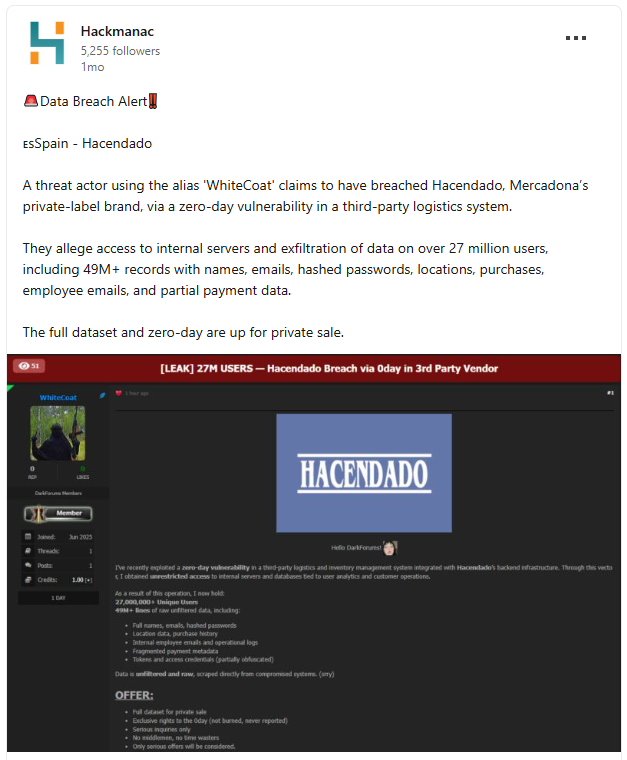
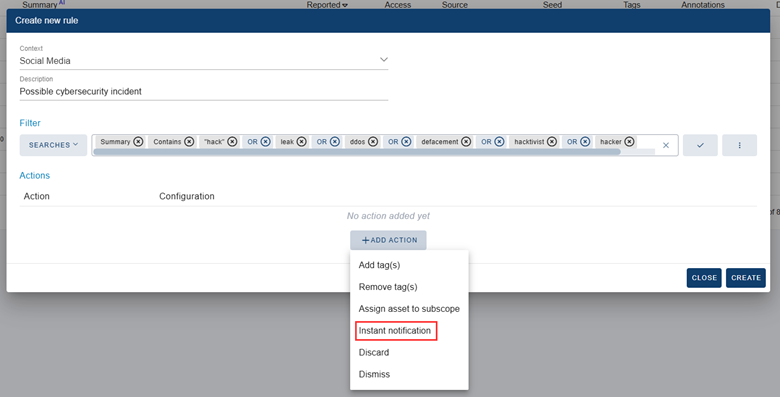
Furthermore, due to the high relevance of these types of content, we can create an automatization rule that will send a notification whenever one of these comments is detected by the platform.
What threats would show up for your brand? Try CompassDRP
By combining the new Social Media module with the existing Data Leakage, Leaked Credentials and Dark Web integrations, Outpost24’s CompassDRP delivers a holistic view of an organization’s external risk landscape. This unified approach empowers security teams to:
- Discover all external exposures (from credentials to social profiles).
- Prioritize based on threat intelligence severity and context.
- React swiftly through automated alerts and actionable insights.
CompassDRP helps organizations to protect their reputation, reduce phishing and fraud risk, and safeguard sensitive assets before attackers can exploit them. Book a live demo.