How hacktivist cyber operations surged amid Israeli-Iranian conflict
In June 2025, Israel carried out airstrikes against key Iranian military and nuclear facilities. Iran swiftly retaliated, escalating regional tensions to unprecedented levels. This military confrontation has not only unfolded in conventional warfare but also triggered a massive surge in cyber operations.
Almost immediately after the kinetic attacks, numerous hacktivist groups began launching cyberattacks primarily targeting Israel and its international allies. The vast majority of these groups present themselves as pro-Iranian and pro-Palestinian actors, motivated by ideological, political, and religious narratives.
However, cybersecurity analysts caution that certain attacks may involve nation-state actors disguising their activity behind the facade of hacktivism. This phenomenon is widely referred to as faketivism.
Summary of hacktivist activity in the Israel-Iran conflict
This article provides a comprehensive, evidence-based analysis of the hacktivist activity surrounding the Israeli-Iranian conflict, examining public statements, claimed attacks, profiles of the key actors involved, and emerging patterns suggesting state-sponsored faketivist involvement.
- Over 80 distinct hacktivist groups are actively conducting or supporting offensive cyber operations targeting Israel and its allies. To a lesser extent, there are some hacktivist groups supporting Israel as well.
- Primary motivations of these groups include pro-Palestinian solidarity, anti-Western sentiment, Islamic ideological alignment, and in some cases, direct support for Iranian geopolitical objectives.
- Attacks span across government, military, defense contractors, judicial systems, energy infrastructure, satellite operations, ICS/OT systems, social media platforms, and financial institutions.
- Several hacktivist entities (e.g., Keymous+, Mr Hamza, Mysterious Team, Inteid, Cyber Islamic Resistance) demonstrate coordination, sharing resources and intelligence, and form operational alliances.
- Suspected faketivist entities such as CyberAv3ngers, Handala, and Predatory Sparrow are likely operating with state support or directly under state direction.
Hacktivist groups’ statements and strategic alliances
Following the Israeli military strikes on Iranian targets, dozens of hacktivist groups responded almost immediately with statements of solidarity and coordinated calls for cyber retaliation. Most of these communications occurred via Telegram, with some activity spilling onto X (formerly Twitter).
These public declarations are ideologically charged, often referencing anti-Zionist, pan-Islamic, and anti-Western narratives. Below is an overview of key statements and alliances made:
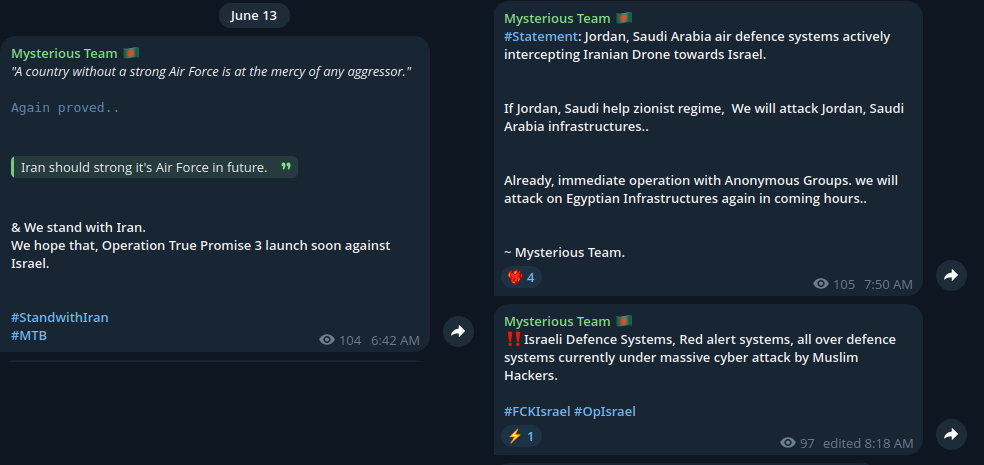
Mysterious Team Bangladesh
This group expressed full support for Iran, calling for “Operation True Promise 3” against Israel. The group warned Jordan, Egypt, and Saudi Arabia to avoid interfering with Iranian operations or risk retaliatory cyberattacks against their own infrastructure.
Team Insane Pakistan
The pro-Pakistan hacktivist group expressed solidarity, urging Iran to aggressively challenge Israel. They compared the conflict to Pakistan’s recent confrontations with India.

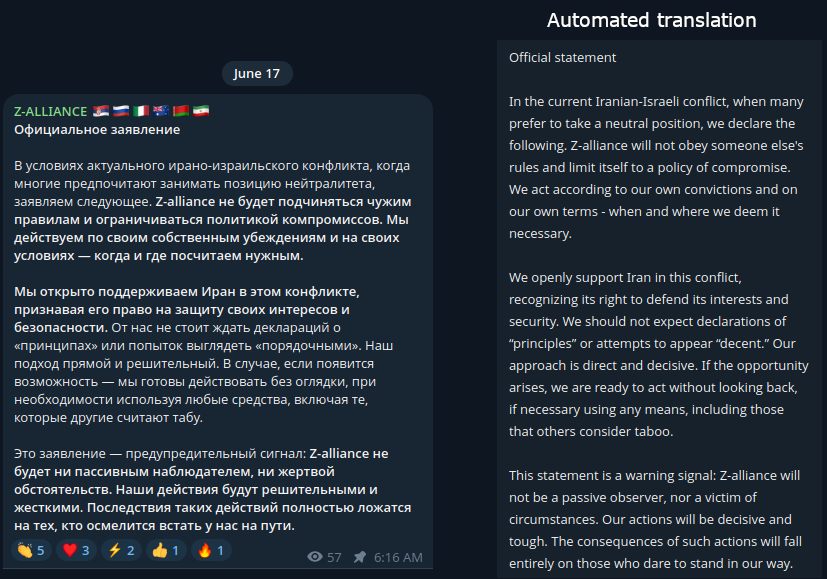
Z-Alliance
In a statement written in Russian, Z-Alliance openly declared their full support for Iran. They rejected political neutrality and stated their readiness to conduct offensive operations without constraint.
Server Killers
Server Killers publicly aligned themselves with the anti-Israel campaign and initiated attacks against Israeli judicial, educational, and governmental web infrastructure. They simultaneously encouraged widespread participation from external supporters.

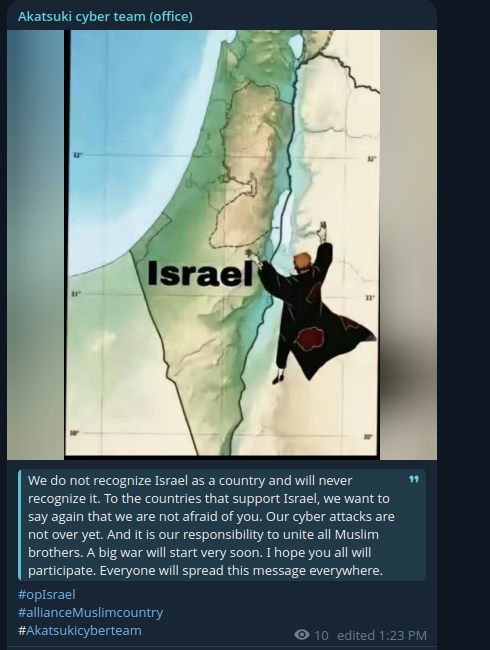
Akatsuki Cyber Team
Akatsuki Cyber Team positioned itself within the pan-Muslim hacktivist narrative, fully rejecting Israel’s legitimacy as a state and expressing intentions to unite additional actors for a broader coordinated cyber offensive.
GhostSec
GhostSec expanded its already ongoing campaigns against Israeli infrastructure, presenting a detailed summary of previously compromised Israeli water, industrial control, and satellite systems. The group outlined its ongoing multiphase attacks, reflecting both persistent operational capabilities and a continued escalation model.

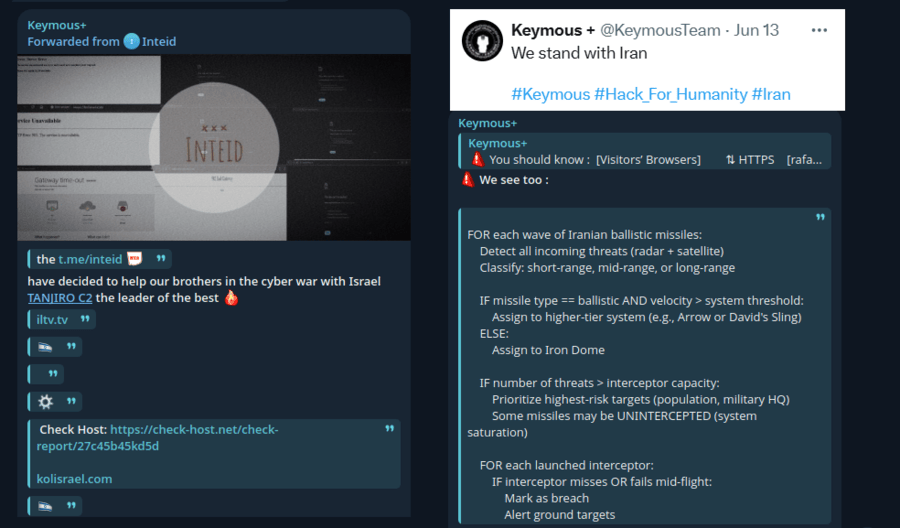
Keymous+ and Inteid
Keymous+ and Inteid announced collaboration, explicitly supporting Iranian cyberwar efforts and naming specific Israeli media targets, demonstrating operational coordination.
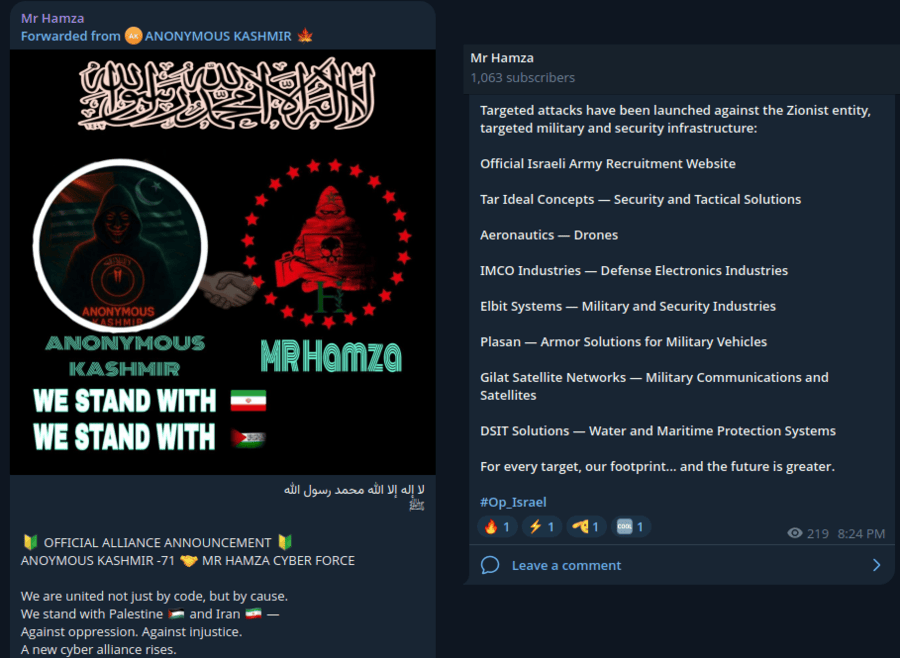
Anonymous Kashmir and Mr Hamza Cyber Force
Anonymous Kashmir and Mr Hamza Cyber Force formalized their alliance, explicitly stating unity based on shared ideological motives. They emphasized joint efforts in support of Palestine and Iran.
DieNet
The group has positioned itself as a vocal supporter of Iran in the broader cyber conflict against Israel, amplifying Tehran’s messaging while leveraging digital platforms for influence operations.

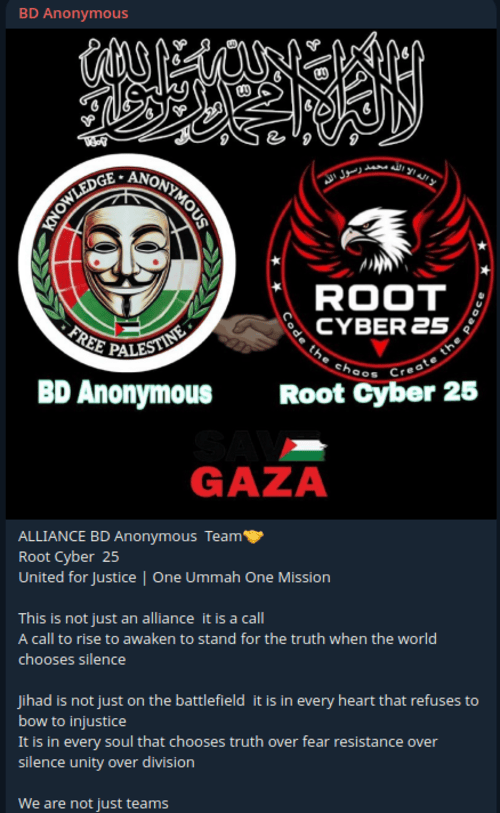
BD Anonymous & Root Cyber 25
They have formed a new alliance with religious and ideological messaging, stating their intention to support Palestine and oppose Zionism, colonialism, and the West.
Claimed hacktivist cyber-attacks on Israeli government and critical industries
Hacktivist groups have claimed responsibility for a wide range of cyberattacks on Israeli systems. While many of these claims remain unverified, they reveal the breadth and ambition of these actors, from symbolic defacements to alleged disruptions of critical infrastructure.
Here is a structured breakdown of publicly claimed attacks:
| Industry Sector | Organization / Targeted Systems | Claiming Hacktivist Group |
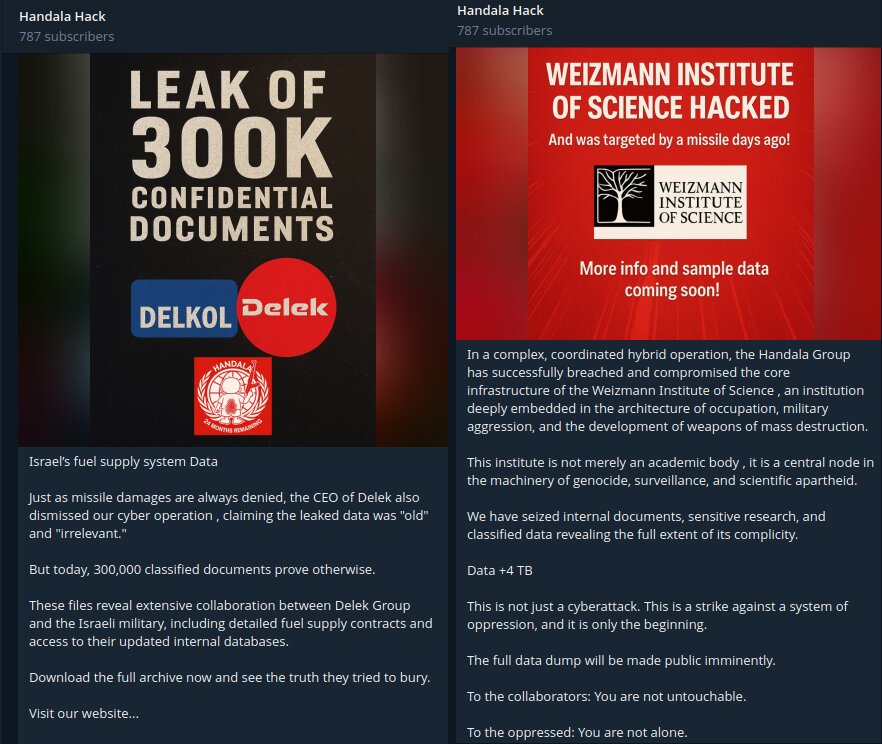
| Academic & Research Institutions | Weizmann Institute of Science (Data exfiltration) | Handala Hack |
| Agriculture & Food Security | Israeli Ministry of Agriculture and Food Security (data leak) | Digital Ghost |
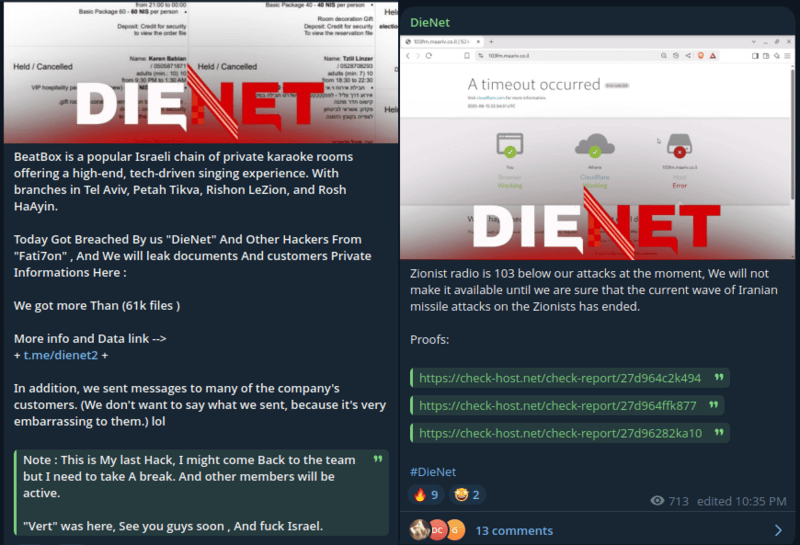
| Commercial Services | BeatBox Karaoke (Israeli entertainment chain) | DieNet |
| Energy Infrastructure | Delek Group | Handala Hack |
| Energy Infrastructure | Paz Oil Company, Rapac Energy | Mr Hamza |
| Energy Infrastructure | Haifa Refinery, oil pipelines, gas transmission lines | Laneh |
| Financial Institutions | BNP Paribas Israel | R3VOXAnonymous |
| Financial Institutions | Mercantile Discount Bank (Israel) | Inteid |
| Financial Institutions | Agura B.C., LTD (crypto infrastructure vendor, Haifa) | Handala Hack |
| Financial Institutions | Nobitex (Iranian crypto exchange) | Gonjeshke Darande |
| Government Alert Systems | Tzofar Red Alert System | GhostSec, DieNet |
| Government Institutions | Israeli Judicial Authority, Supreme Court of Israel | Server Killers |
| Government Institutions | Israeli Ministry of Education | Server Killers, R3VOXAnonymous, Dark Storm Team |
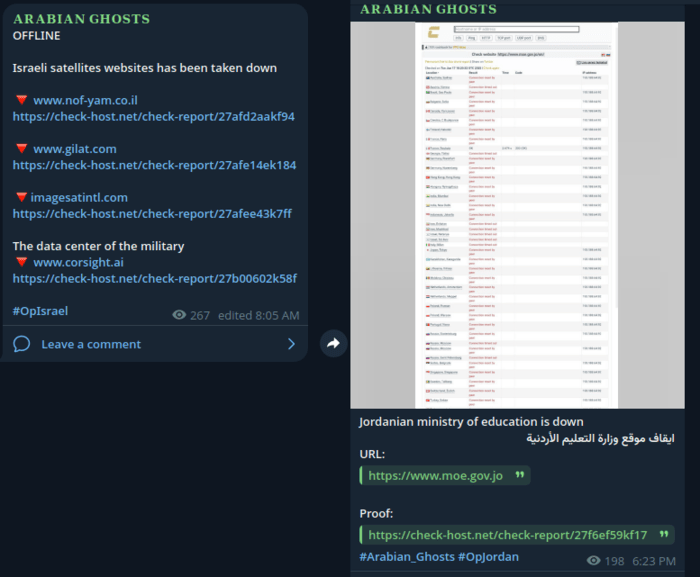
| Government Institutions | Jordanian Ministry of Education | Arabian Ghosts |
| Government Institutions | Israel Ministry of Justice | Dark Storm Team |
| Government Institutions | Israel State Archives | Dark Storm Team |
| Government Institutions | Israel Tax Authority | Dark Storm Team |
| Government Institutions | Israel Supreme Court | Dark Storm Team |
| ICS/OT Systems | 100+ Modbus PLC devices, 40+ Aegis 2 water control devices, 8 Unitronics devices | GhostSec |
| ICS/OT Systems | Siemens S7 PLCs in Tel Aviv | SYLHET GANG SG |
| Internet Infrastructure | Tel Aviv Internet (ISP: R.L Internet and Networks Ltd.) | Cyber Islamic Resistance |
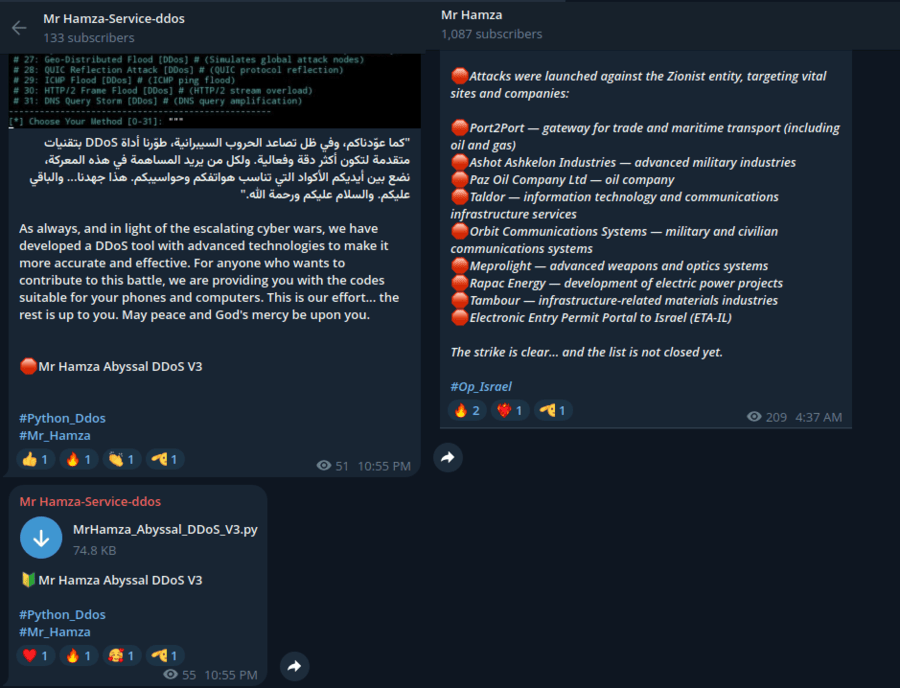
| Logistics | Part2Port (port logistics) | Mr Hamza |
| Logistics | Mor-Logistics Ltd (425GB data leak) | Handala Hack |
| Media Networks | Israeli television network TBN (data deletion) | Cyber Islamic Resistance / @zerodayx1 |
| Media Networks | Israeli Radio Live services | DieNet |
| Media Networks | IsraelNews.co.il, Nana10.co.il | Arabian Ghosts |
| Media Networks | Times of Israel (DoS outage) | Cyber Jihad Movement, Team Fearless (JOS) |
| Military & Security | Cyber Command operations under IDF Maj. Gen. Shlomi Binder | Handala Hack |
| Military & Security | Ashot Ashkelon Industries, Meprolight, Orbit Communications Systems | Mr Hamza |
| Military & Security | Elbit Systems, Aeronautics, IMCO, Plasan, DSIT Solutions, Tar Ideal Concepts | Mr Hamza |
| Military & Security | Iron Dome System (alleged data leak) | Digital Ghost |
| Municipal Infrastructure | Israel Antiquities Authority (document breach 2016–2025) | DieNet |
| Satellite Infrastructure | Nof-Yam, Gilat Satellite Networks, Imagesat Intl. | ARABIAN GHOSTS |
| Satellite Infrastructure | 10 VSAT devices | GhostSec |
| Social Media Platforms | Israeli Instagram Accounts | Team Fearless / #WeAreRootSec |
| Social Media Platforms | Personal data of PM Netanyahu (doxxing) | Team Fearless / #WeAreRootSec |
| Statistical & Data Platforms | Israel Central Bureau of Statistics (cbs.gov.il) | WeAreRootSec |
| Transportation Services | CityRide (Israeli ride-sharing platform) | Inteid |
| Water Infrastructure | Gan HaDarom pumping station, Gderot Regional Council | Z-Alliance |
These incidents range from relatively unsophisticated DDoS and web defacement campaigns to disruptions of ICS/OT systems, exfiltration of sensitive data, and psychologically targeted doxxing campaigns. Some groups have even hinted at ransomware deployments, suggesting an escalation in both capabilities and intent.
Who are the main hacktivist groups involved, and what are their capabilities?
The following groups have notably increased their operational tempo amid this geopolitical conflict:
Mr Hamza
- Focus: Pro-Muslim, pro-Palestinian, anti-pornography, anti-Western platforms.
- Activities: Attacks on Israeli military suppliers, ports, energy companies, communications, defense contractors, IT, and government portals.
- Tools: Abyssal DDoS V3, botnets (Maple, Onyx C2, RebirthStress, Squid C2).
- Alliances: Anonymous Kashmir, Anonymous Guys, Team Fearless, Azzasec, Arab Ghosts Hackers.
- Origin Hypothesis: Possibly Moroccan-managed (unconfirmed).
Dark Storm Team
- Focus: Pro-Palestine, pro-Russia, anti-NATO, anti-Israel, financially motivated hacktivism.
- Activities: DDoS-for-hire services, web defacements, data leaks, crypto-based fundraising, anti-Western propaganda.
- Tools: Arthur C2 botnet, Telegram-based DDoS orchestration platforms.
- Alliances: Moroccan Black Cyber Army, Akatsuki Cyber Team, Z-Pentest, Keymous+, Noname057(16).
- Origin Hypothesis: Egyptian leadership.

GhostSec
- Focus: Pro-Islam, anti-Israel, human rights hacktivism; highly organized; former commercial cybercrime activity.
- Activities: DDoS, ICS targeting, industrial sabotage, data exfiltration, extortion, ransomware (GhostLocker), doxing, spamming, zero-day sales.
- Tools: Custom tools (GhostLocker ransomware, GhostStealer, Ghostly Development malware), botnet services; DarkZone forum launched in 2024.
- Alliances: SiegedSec (longstanding partner), Stormous (joint ransomware), Five Families (until 2024).

DieNet
- Focus: Anti-Zionist, anti-US, anti-Trump hacktivism; increasingly aligned with Iranian geopolitical narratives.
- Activities: DDoS attacks on Israeli emergency alert and radio broadcasting infrastructure; data leaks from government and media entities; defacements of commercial websites; public psychological operations via Telegram; announced development of the “LockNet” ransomware platform.
- Tools: Custom botnet for DDoS attacks (unnamed); third-party verification tools (e.g., Check-Host.net); bespoke scripts for service availability monitoring and attack confirmation.
- Alliances: Possible relation with Arabian Ghosts; public rivalry with Dark Storm Team.
- Origin: Decentralized international actor network; most of its members are allegedly from Russia.
Arabian Ghosts
- Focus: Regional and ideological hacktivism; initially anti-Iran/Russia, now aligned with anti-Israel operations.
- Activities: DDoS, defacements, ICS/OT disruption, data leaks. Claimed Red Alert app attack; announced but unconfirmed ransomware project BadLadyBird.
- Origin Hypothesis: Likely Syrian; self-identified as “Syrian Ghosts” supporting Anonymous Syria.
- Alliances: No formal ties, but recurrent references to DieNet, Mr. Hamza, SYLHET_GANG_SG, and others suggest informal collaboration.
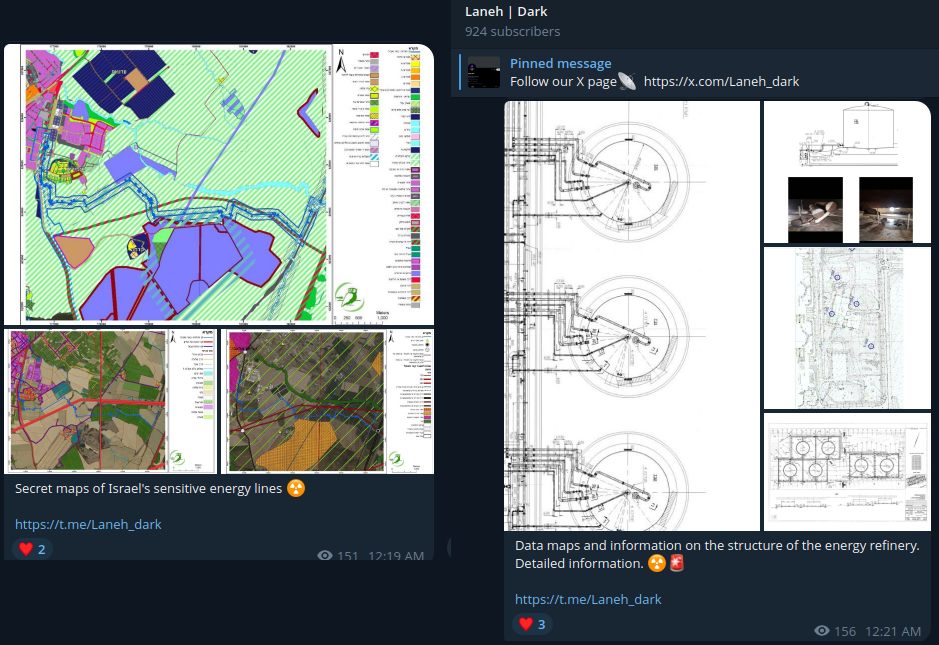
Laneh Dark
- Focus: Pro-Iran, anti-Israel, anti-Gulf states; ideologically driven hacktivism with elements of cyber extortion.
- Activities: Data theft and ransom-style pressure tactics on companies in Saudi Arabia, Jordan, UAE, and Azerbaijan; public leaks of sensitive infrastructure data; political messaging aligned with Iranian strategic interests; alleged mass device access via “All Seeing Eye” vulnerability.
- Tools: Custom leak operations; extortion demands; Telegram/X for psychological ops; claims of undisclosed vulnerability exploitation tools affecting 45,000 global systems.
- Alliances: NoName057(16); part of “Nest Security Group” alliance with Russian, Palestinian, and Iranian-affiliated actors.
- Origin Hypothesis: Likely Iranian-managed, ideologically motivated with indirect state alignment; emerged in 2024 with increasing visibility post-June 2025.
Are nation-states disguising themselves as hacktivists?
While many hacktivist groups appear motivated by ideological or political convictions, several actors involved in the Israeli-Iranian conflict are suspected of being state-controlled or heavily state-influenced, blurring the lines between grassroots hacktivism and state-sponsored cyber operations.
These so-called faketivist entities serve as plausible deniability fronts for nation-states, complicating attribution and escalating geopolitical risks. These groups blur the line between independent hacktivism and state-sponsored cyber warfare, complicating attribution and increasing the geopolitical risks of escalation.
Notable faketivist entities that analysts continuously monitor include:
Cyber Av3ngers
- Attribution: Iran-linked faketivist group likely operated under IRGC (Islamic Revolutionary Guard Corps) control.
- Focus: Disruption of Israeli and U.S. critical infrastructure (ICS/OT, energy, water systems).
- Activities: Targeting Israeli companies (e.g., BAZAN Group), U.S. water plants (Unitronics PLCs), oil & gas (Sophos firewall exploits); data exfiltration, limited sales of compromised data in underground forums.
- Tools: IOControl embedded Linux backdoor with wiper capabilities; AI-assisted vulnerability research; ICS/SCADA exploit development.
- Alliances: May have indirect links with other Iranian groups such as Moses Staff; unconfirmed relations with IRGC’s “Soldiers of Solomon“.
- Commercial Activity: Participated in data sales via Breached and DarkForums, though with limited underground presence.
Handala Hack Team
- Attribution: Likely Iranian-controlled faketivist persona posing as pro-Palestinian hacktivist group.
- Focus: Phishing-based wiper deployment using social engineering around high-profile events.
- Activities: Claimed “Operation HamsaUpdate” (Hatef/Hamsa wipers exploiting F5 vulnerabilities) and phishing during the 2024 CrowdStrike outage.
- Indicators of State Backing: High sophistication in targeting, Hebrew language proficiency, victim data inclusion, consistent with state-level preparation.
- Tools: Hatef (Windows wiper), Hamsa (Linux wiper); social engineering campaigns leveraging trending security incidents.
- Underground Presence: Brief activity in BreachForums and RAMP after December 2023 creation; maintains active Telegram channels and TOR domains.
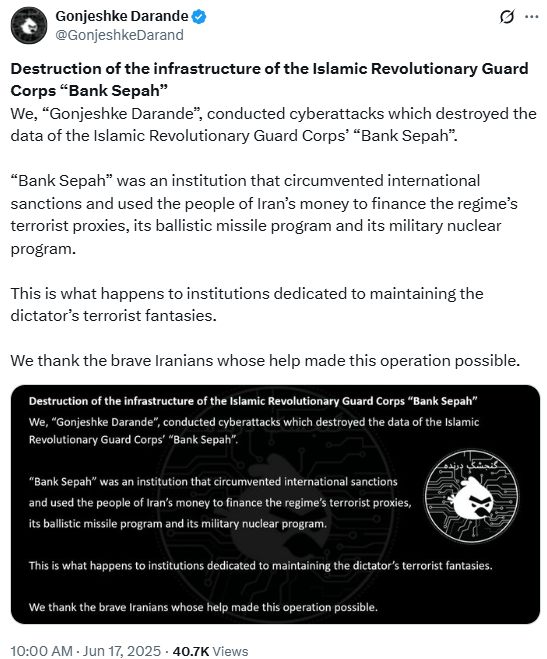
Preadtory Sparrow (aka Gonjeshke Darande)
- Attribution: Highly likely Israeli state-sponsored offensive actor masquerading as an Iranian opposition group. Read our recent analysis into their attack on the Nobitex crypto exchange.
- Focus: Strategic disruption of Iranian critical infrastructure.
- Activities: Sabotage of Iran’s railway (Meteor wiper), gas stations (payment system attacks), steel industry (Khouzestan mill sabotage), energy infrastructure.
- Tools: Custom wipers (Meteor, Stardust, Comet), lockscreen message payloads; highly tailored attacks involving prior detailed reconnaissance.
- Narrative Control: Justifies operations via Telegram/X accounts with anti-IRGC (Quds Force) rhetoric, emphasizing civilian protection.
- Tactics: Long periods of dormancy between highly impactful operations, often coinciding with major regional escalations.
What can we expect next in this evolving cyber conflict?
The dramatic rise in hacktivist cyber operations following recent geopolitical escalations between Israel and Iran underscores the increasingly central role cyber conflict plays within modern warfare. Ideologically-driven hacktivists, alongside possible nation-state faketivists, have clearly demonstrated their readiness to exploit geopolitical tensions to pursue diverse strategic objectives.
Given that the Israeli-Iranian confrontation is still developing, it’s hard to predict whether a ceasefire will hold. If cyber activity re-intensifies, expected trends would likely include:
- Increased DDoS campaigns targeting Israeli energy, telecom, defense, and government systems.
- Escalation towards allies such as the US, UK, and Arab states aligned with Israel.
- Emerging retaliatory operations by pro-Israeli groups such as Predatory Sparrow, already engaging in offensive activity against Iranian systems.
- Sustained propaganda and psychological operations, further exploiting public fear and political instability.
Organizations across all geopolitical fault lines are advised to adopt heightened cybersecurity postures to defend against what may evolve into a prolonged and highly disruptive cyber conflict.
Stay ahead of emerging threats
Outpost24’s CompassDRP solution combines the asset discovery powers of our EASM platform with threat-intelligence powered DRP modules. Customers are backed up by our world-class human-led threat intelligence team, KrakenLabs. Get in touch to learn more.

