WPS crack with Reaver: WPS pin attacks
Hackers are using the Reaver WPS tool to exploit the WiFi Protected Setup (WPS) feature found on many WiFi routers and access points. This method involves remotely brute-forcing the WPS handshaking process to potentially crack a WPA network. Most networks will now be running the much more robust WiFi Protected Access (WPA), with WEP running mainly on the older systems that haven’t been updated or maintained. But while it’s not as trivial as breaking into a WEP network, WPA is not completely infallible.
The article provides insights into the vulnerabilities associated with WPS and demonstrates how to crack WPS using Reaver. We’ll take a look at one of the methods used to crack into a WPA network, and some of the pitfalls you may encounter.
What is WPS?
WPS stands for Wi-Fi Protected Setup. It’s a network security standard designed to simplify the process of connecting devices to a secure wireless network. Instead of entering a complex password, WPS allows users to connect using either a push button on the router or an 8-digit PIN printed on the device.
However, while convenient, WPS has been criticized for security vulnerabilities, particularly with the PIN method which can be susceptible to brute-force attacks.
What is a WPS attack and how does it work?
A WPS (Wi-Fi Protected Setup) attack targets a feature found on many WiFi routers and access points. WPS is designed to make it easier for users to connect devices to a secure WiFi network, usually by pressing a button on both the router and the client device (the latter often being a software-based button). Once activated, the devices exchange information and automatically establish a secure WPA connection.
On the surface, this is a very clever feature. It allows less savvy users to establish a secure connection between their devices quickly and easily, and as it requires physical access to the hardware, it would seem relatively secure.
But a tool called Reaver has been designed to brute-force the WPA handshaking process remotely. Reaver uses a brute-force attack method to remotely guess the WPS PIN and complete the setup process without the button ever being pressed. This allows an attacker to gain access to the network’s WPA credentials.
While some newer devices are building in protection against this specific attack, the Reaver WPS exploit remains useful on many networks in the field.
Note: To be clear, WPS is the vulnerable system in this case, not WPA. If a network has WPS disabled (which they should, given the existence of tools such as this), it will be immune to this type of attack.
What is the Reaver tool?
Reaver is a powerful tool that brute-forces WiFi Protected Setup (WPS) to perform a wifi crack, targeting the network’s WPA passphrase. It focuses on the WPS PIN to gain network access, exploiting vulnerabilities in the WPS system.
The Reaver tool offers features like adjustable delay between PIN attempts, timeout settings, and mechanisms to handle locked WPS states. It logs progress, allowing for the attack to be paused and resumed as needed. However, the process can be lengthy, often taking many hours to complete.
How to find vulnerable networks with Reaver
If you’ve read the previous tutorial on cracking into a WEP network, you’ll recognize the command used to get the hardware into monitor mode:
airmon-ng start wlan0
From here you could use airodump-ng to look for networks, but Reaver actually includes its own tool for finding vulnerable WPS implementations which is much more straightforward. To start it, run the following command:
wash -i mon0
The output will look something like this:

This shows two networks which are, at least in theory, vulnerable to the WPS brute force attack Reaver uses. Note the “WPS Locked” column; this is far from a definitive indicator, but in general, you’ll find that APs which are listed as unlocked are much more likely to be susceptible to brute forcing.
You can still attempt to launch an attack against a network which is WPS locked, but the chances of success aren’t very good.
How to use Reaver
Once you’ve found a network you wish to run the attack against, operating Reaver is very straightforward. The basic command needs only the local interface, channel, and ESSID to be specified. The command to launch Reaver against the “linksys” network above would look like this:
reaver -i mon0 -c 6 -b 00:23:69:48:33:95 -vv
The only part of the above command that might not be immediately obvious is “-vv”; this enables verbose output which greatly helps when trying to gauge how well Reaper is (or is not) progressing.
Once you’ve started Reaver, you’ll start seeing output like this:
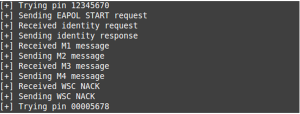
This output shows that WPS pins are successfully being tried against the target (here we see 12345670 and 00005678 are being tested), and Reaver is operating normally.
Advanced options for Reaver
Ideally, the basic command works and the attack progresses as expected. But in reality, different manufacturers have been trying to implement protections against Reaver-style attacks, and additional options may be required to get the attack moving.
As an example, the following command adds a few optional switches that can help to get Reaver working on more picky devices:
reaver -i mon0 -c 6 -b 00:23:69:48:33:95 -vv -L -N -d 15 -T .5 -r 3:15
The core command hasn’t changed, the additional switches just change how Reaver behaves:
-L
Ignore locked WPS state.
-N
Don’t send NACK packets when errors are detected.
-d 15
Delay 15 seconds between PIN attempts.
-T
Set timeout period to half a second.
-r 3:15
After 3 attempts, sleep for 15 seconds
This is by no means an exhaustive list of Reaver options, but it gives an idea on what kind of things you might want to try.
How long does Reaver take to crack WPS?
Even under ideal conditions, Reaver can take a very long time to complete its run. There is an element of chance involved, the brute forcing could theoretically discover the PIN very quickly, but in general it is going to take many hours to even make a dent in the possible pool of PINs.
Luckily, Reaver keeps a progress log file automatically, so you can stop the attack at any time and resume whenever it’s convenient. Spending a few hours a day running Reaver against the same network should uncover its PIN, and through that, the WPA passphrase… eventually.
How to defend against WPS pin attacks
Defending against WPS (Wi-Fi Protected Setup) attacks is important due to the vulnerabilities associated with the PIN method. Here are some effective defenses:
- Disable WPS: The most straightforward and secure approach is to disable WPS on your router. This removes the vulnerability entirely. You can usually do this through your router’s settings page, which is accessible via a web browser.
- Change the default password: Even if you disable WPS, it’s a good practice to change the default Wi-Fi password to a strong, unique one. This adds an extra layer of security.
- Use strong encryption: Ensure that your Wi-Fi network uses strong encryption methods like WPA3 or, at a minimum, WPA2. Avoid using WEP, which is outdated and easily cracked.
- Update firmware: Regularly update your router’s firmware to the latest version. Manufacturers often release updates to patch security vulnerabilities, including those related to WPS.
- Limit access: Use MAC address filtering to allow only specific devices to connect to your network. This can help prevent unauthorized devices from attempting to connect via WPS.
- Change the router’s default IP address: Changing the default IP address of your router can make it harder for attackers to access the router’s settings page.
- Use a strong router admin password: Change the default admin password for your router to a strong, unique password. This prevents unauthorized access to your router’s settings.
- Monitor network activity: Regularly check your router’s logs for any suspicious activity. This can help you detect and respond to potential attacks more quickly.
- Use a network security solution: Consider using a network security solution or a firewall that can help detect and block suspicious activity on your network.
By implementing these defenses, you can significantly reduce the risk of WPS crack attacks on your Wi-Fi network.
Interested in finding more vulnerabilities within your organization? Discover vulnerabilities within your applications with Outpost24’s Pen Testing as a Service solution.


